When it comes to cyber security, there’s nothing worse than storing important secret data in plaintext. With even the greenest malicious actors more than capable of loading up a hex editor or decompiler, code can quickly be compromised when proper precautions aren’t taken in the earliest stages of development. To help avoid this, encryption can be used to hide sensitive data from prying eyes. While a simple xor used to be a quick and dirty way to do this, for something really sophisticated, polymorphic encryption is a much better way to go.
A helpful tool to achieve this is StringEncrypt by [PELock]. An extension for Visual Studio Code, it’s capable of encrypting strings and data files in over 10 languages. Using polymorphic encryption techniques, the algorithm used is unique every time, along with the encryption keys themselves. This makes it far more difficult for those reverse engineering a program to decrypt important strings or data.
While the free demo is limited in scope, the price for the full version is quite reasonable, and we expect many out there could find it a useful addition to their development toolkit. We’ve discussed similar techniques before, often used to make harder-to-detect malware.
[Thanks to Dawid for the tip!]















If you’d decide to use this over something that’s proven, well understood and free, like AES, then you’re insane.
That’s only because you misunderstand the purpose of polymorphic encryption. The purpose is not to keep it a secret forever but to create so many possible forms that it cannot be detected using simple automated detection methods.
Detected? No. That is stego. So many possibilities is already covered by verified encryption. I don’t hate bulking it up, but it is a weird step towards obfuscation with the justification being the same as what encryption already is.
What you’re describing is obfuscation. So why do the creator(s) not describe it as an obfuscation tool? Why do they only talk about this in the context of encryption? They literally say it’s a way of storing data in a “secure & encrypted form” – which it is not at all. It’s reckless to promote this as a legitimate tool for encryption.
It’s not obfuscation as you imply, because the one you are thinking is static. With polymorphic encryption, the “shape” of code is always different, the executable saves itself with different sizes, code paths, entry points, jump points, etc, every time it is run, so it is always a different beast.
This kind of technique is used for (very nasty) virus, and it is a nightmare for anti-virus, because they won’t be able to see the patterns and identify it as such, until someone cracks the pattern on the polymorphic routines.
It’s still obfuscation. Just somewhat convoluted obfuscation.
> that it cannot be detected using simple automated detection methods.
It’s pretty simple to just run the code…
Agreed, this whole blurb is just “modulating phasers”.
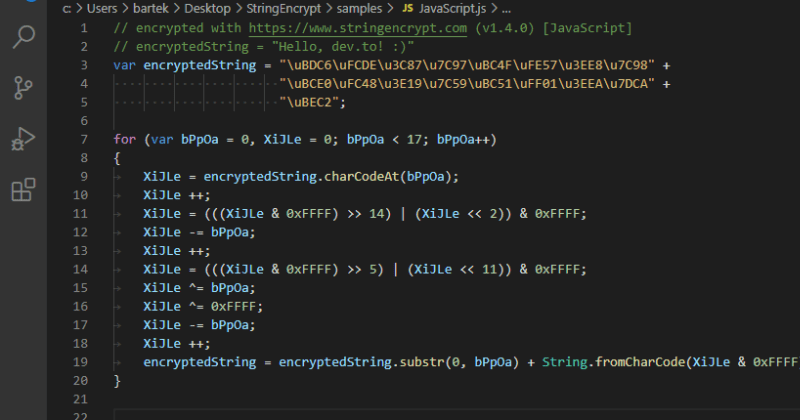
The example shown is Javascript. In what way could that imaginably give any hacker a hard time?
Because it’s hard to spot with automated tools. You might write a regex to find this one, but the next one won’t match your regex.
Polymorphic stuff is deeply disappointing once you realise it’s not going to turn into a lion or a bowl of petunias or something.
Oh no, not again!
`s/lion/sperm whale/`?
1.Hitchhiker 16,54
Can’t I just be random AND add a HHG2G ref? If we’re going to be anal about it, present your towel for inspection.
Is it such a slow news day that you’re posting adverts?
Obfuscating your strings with this tool will deter casual inspection but anybody even vaguely determined will be able to reverse it easily. The sequence of bitwise operations is an obvious hint for where to look. Feeding the binary into a decompiler like Ghidra or IDA would make this even more easy. There are IDA plugins which handle most of this already for you.
Too many warning signs here for an implementation of a substitution cipher tied to a server side service.
Your strings won’t change each time you rebuild your project unless you manually go through and rerun this tool on each of your strings. Each time you run the tool on a string, it uses up one of your usage credits and also sends your string to their server to be obfuscated which is amazing. If you’re capable of writing your own tool to automatically run all your strings through their API for each build then you could have made your own scheme for free.
I hope Dawid enjoys their 500 free usage credits for sending this to HaD.
for S&G I smashed out a version of this for go, not even a language they support, took me… oooh 15 mins?
Why would you obfuscate a string in a go binary? who knows, I was bored (it’s 2 am and my insomnia is playing up, so was reading HAD, yes I’m behind)
It should be called ‘STRING OBFUSCATION’ instead of “STRING ENCRYPTION”. it still has it’s uses.
I understand the purpose and using something like this makes sense. This being said… locks are for honest people…
I agree with Mark Smith above :)
This is among the most useless pieces of software I have ever seen. Just put a breakpoint after the for loop and bingo you have the string. Even in machine code the loop would be easy to find, as the multiple XOR with constant instructions are basically screaming “DEOBFUSCATION!!!”.
There are (free) tools that blow this out of the water. Node.js javascript-obfuscator for js, ithare::obf for C. I wouldn’t want to touch the output of either of those with a 10 foot pole.
I totally agree.
I came across something like this a few months ago in an abandoned plugin that I had to bugfix.
They obfuscated some Javascript inside a C# dll, but it was a simple matter to find the de-obfuscation function, and write a tool to de-obfuscate the strings, so I could then debug the javascript.
The program sends your data off to their servers to be “encrypted”. not sure thats the best idea.
Reminds me of some of the times I’ve run across maildroppers and such on websites that I’ve been asked to update. Some script kiddie exploits some PHP vulnerability and uses it to run code to download a PHP file manager and then download a obfuscated mail sending script to a server. A lot of times they use a lot of tricks that look like this so it’s hard to find the files and see what they are doing.
Can Open Source solve this problem? That is, just release the code on github?
I wondered how well it works when used in a compiled language, with compiler optimizations… It is only using constants, which the compiler can simplify, nicely deobfuscating it for you in the compiled binary… Well, GCC and Clang at -O3 both do exactly that on their example C / C++ code and also some simple tests produced by their online demo. -O2 normally doesn’t, although I did see Clang at -O2 do it with one of the (relatively simple) demo results.
This post really sounds like a covert ad and it is annoying. “The price is reasonable”… by what standard ? How is that journalism ? Did you receive a “reasonable” compensation too ?
I have done reverse engineering of a few apps before and had to deal with similar stuff before and it is clearly not going to stop even a beginner who is motivated enough (I consider myself a beginner).