Given how fast technology is progressing, some consumer gadgets lend themselves to being replaced every few years. Mobile phones are a particularly good example of a device that you probably won’t want to hold onto for more than 4 years or so, with TVs not far behind them. On the other hand, something like a home alarm system can stay in the fight for decades. As long as it still goes off when somebody tries to pop a window, what more do you need?
Well if you’re like [Brett Laniosh], you might want the ability to arm the system and check its current status from your phone. But instead of getting a whole new system, he decided to upgrade his circa 1993 Gardiner Gardtec 800 alarm with an ESP32. As it so happens, the original panel has an expansion connector which he was able to tap into without making any modifications to the alarm itself. If you’ve got a similar panel, you might even be able to use his source code and circuit schematics to perform your own modification.
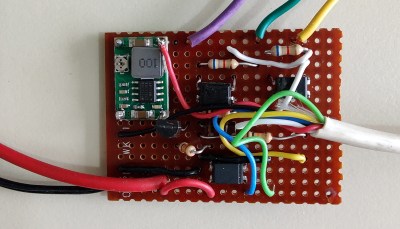
Now we know what you’re thinking. Surely there’s a risk involved when trusting an ESP32 connected to the Internet with the ability to disarm your home alarm system. [Brett] has considered this, and made sure that the web server running on the microcontroller can only be accessed from the local network. If he does want to connect from beyond WiFi range, he does so through a VPN. In other words, his code is never directly exposed to the wilds of the Internet and is always hiding behind some kind of encryption.
The WiFi connection allows [Brett] to arm and disarm the alarm system remotely, check if it’s been triggered, and reset it if necessary, all from his smartphone. But he’s also added in a 433 MHz receiver so he can use simple handheld fobs to arm the system if he doesn’t want to go through the phone. Even if you dropped out the Internet connectivity, this alone is a pretty nice upgrade.
For those not afraid to take the more invasive route, you could potentially reverse engineer and reprogram your old alarm panel. Or you could even so the full DIY route and create your own low-cost alarm system using the ESP32 and off-the-shelf modules.
















So I strip the purple wire, put 12v on it for 1 second, and the alarm is off. Convenient! If I’m willing to put a little more effort in, I have to sniff the 433Mhz signal (these fobs are not secured), and use that. And it’s all nicely documented online :)
It said the fobs only arm…the panel will have anti tamper and if you can get enough access to “strip the purple wire” then most alarm systems are done in by that point. It would’ve already gone off anyway, promoting investigation by neighbours.
As a rule of thumb, access to the hardware means full access.
“… his code is never directly exposed to the wilds of the Internet and is always hiding behind some kind of encryption.”
I’m sorry, but I have to disagree with this sentence. Until somebody hacks through the firewall, or figures out the WiFi password, or another new firmware vulnerability is discovered. WiFi and firewalls are getting hacked constantly and new vectors being discovered very, very frequently. The only way to 100% keeping your system from being exposed to the “wilds” of the Internet is keeping it from being connected in the first place. The only guarantee is having no WiFi and no wired connection AT ALL. Otherwise, no matter how small, the risk is still there.
I’m sorry to be such a cynic here, but at 53 years of age I’ve seen pronouncements of security and invulnerability of computer systems to outside attack proven wrong way too many times to count. This is only getting worse and happening more often now that people are determined to put every little device they have at home on their home network and connected to the outside Internet. So, if I may, let me fix that sentence for you:
“…his code is POSSIBLY NOT directly exposed to the wilds of the Internet AT THE MOMENT and is HOPEFULLY hiding behind some kind of encryption AT THE MOMENT.”
Well if you subscribe to the lockpickinglawyer channel on n youtube you might think that all locks are useless but all security.is relative, security can be “good enough” if the cost of entry is greater than the perceived reward.
+1
This is threat assessment 101
It seems like an almost entirely proprietary system, not exactly the low hanging fruit. Anybody who hacks it isn’t going to know the address. So if somebody does manage to stumble upon it, hack it and did find their way into the alarm system, is it really worth the hassle of finding the house to steal anything?
Possibly.
Now that there’s a write up, and details maybe a targeted phishing campaign might lead to some results. Id say there’s a higher chance of payment here than cold calling 100,000 people telling them you’re from Windows. And there are plenty of people around who do this type of thing for shits n giggles. If it was my system, id either not share it or keep everything anonymous (or as anonymous as possible).
This is a ridiculous line of logic. The average consumer router with a proper WPA2 key is more than secure enough. These “vectors” you’re talking about are Boogymen.
Not really – especially the ISP provided boxes being so very numerous (and often required as the ISP’s wont’ let you use your own modem) are huge targets for cracking, and many of them have massive security problems that are documented but not fixed for ages if ever..
Anything popular enough to real mass deployment is an obvious target for hackers to spend time on. No point trying to figure out the bugs in my own personal router/modem/security system build – I am not a high value target so the time sunk to potential reward is damn near zip.. But something that is deployed en mass – like those rubbish web exposed nanny cams and the like with so many units out there its worth finding their flaws.
I do think he has done the internet side of things reasonably however, its not really secure, but its not recklessly exposed by design either. (And really secure is damn nearly impossible if not actually impossible to make in a functional manner)
I forgot all common thieves were multi talented hardware and software hackers.
This sort of thing only really applies to things like relaying car fobs…not esp32 home alarms, every implementation is different, no idea what’s in the house. Car works because it’s a one button action for a particular model and a given value when the stolen car is sold.
Security is ALWAYS relative, there is no such thing as perfect security. Same goes for encryption. It will always be a trade-off for convenience. If i cast my house in a huge cement block, its pretty safe from break-ins, but now it is also useless to me.
Have all of the usual stuff per a building that houses an engineer – 21 magnetic switches, 72 strain gages on windows, PIRs, and some other stuff. But the best security sensor will always be my dogs. Woof. An would never trust home security to wifi/TCIP/etc.
There is a relatively cheap product called Konnected that does something like this, retrofits to your old security system to give you access wirelessly. I have it and it works great, not as fun as rolling your own though I imagine.
I’m looking to do a similar thing with my Texecom panel. There are two exposed 5V TTL serial ports that I plan to hook up to an ESP32. One port will be used as a “COM-IP replacement”, which bridges the alarm to an IP network, and allows remote reconfiguration, log retrieval, and keypad emulation, and the other will be configured as an Alarm Receiving Center (i.e. when the alarm is triggered, it attempts to dial the ARC and notify it of the zones etc in violation).
The standard COM-IP makes use of a Lantronix XPortPro, which provides a mechanism for the panel to actually configure the IP parameters of the XPortPro. The idea is to implement an AT command processor in the ESP32, similar to the RS232-ESP8266 modem replacements, and process the commands from the panel as expected. Similarly, the ARC port actually thinks that it is talking to a GSM modem, so it tries to send SMS’s, etc. The AT command processor would be used to translate that into MQTT messages, ultimately relayed to something like Home Assistant.
Good luck with the Texecom. What you describe is a different league, I based my project on what was available to me via the panel IO. Initially I was only planning on an email notification system but the project grew somewhat.
Saying that internet faced esp32 is not secure for your home, but using 433Mhz remote for unlock?
yeah that’s secure /s