Given how fast technology is progressing, some consumer gadgets lend themselves to being replaced every few years. Mobile phones are a particularly good example of a device that you probably won’t want to hold onto for more than 4 years or so, with TVs not far behind them. On the other hand, something like a home alarm system can stay in the fight for decades. As long as it still goes off when somebody tries to pop a window, what more do you need?
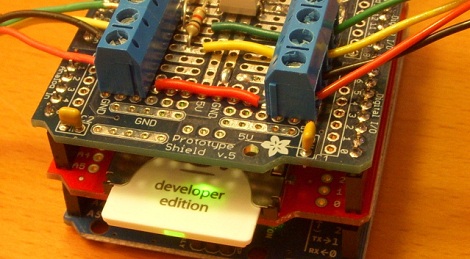
Well if you’re like [Brett Laniosh], you might want the ability to arm the system and check its current status from your phone. But instead of getting a whole new system, he decided to upgrade his circa 1993 Gardiner Gardtec 800 alarm with an ESP32. As it so happens, the original panel has an expansion connector which he was able to tap into without making any modifications to the alarm itself. If you’ve got a similar panel, you might even be able to use his source code and circuit schematics to perform your own modification.
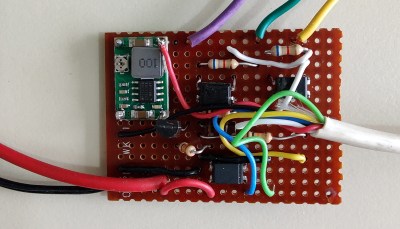
Now we know what you’re thinking. Surely there’s a risk involved when trusting an ESP32 connected to the Internet with the ability to disarm your home alarm system. [Brett] has considered this, and made sure that the web server running on the microcontroller can only be accessed from the local network. If he does want to connect from beyond WiFi range, he does so through a VPN. In other words, his code is never directly exposed to the wilds of the Internet and is always hiding behind some kind of encryption.
The WiFi connection allows [Brett] to arm and disarm the alarm system remotely, check if it’s been triggered, and reset it if necessary, all from his smartphone. But he’s also added in a 433 MHz receiver so he can use simple handheld fobs to arm the system if he doesn’t want to go through the phone. Even if you dropped out the Internet connectivity, this alone is a pretty nice upgrade.
For those not afraid to take the more invasive route, you could potentially reverse engineer and reprogram your old alarm panel. Or you could even so the full DIY route and create your own low-cost alarm system using the ESP32 and off-the-shelf modules.