Those with security clearance are capable of making foolish mistakes, just like the rest of us. So is the story of how a Dutch journalist made an appearance on video meeting of the European Union’s Foreign Affairs Council (Dutch language, Google Translate link).
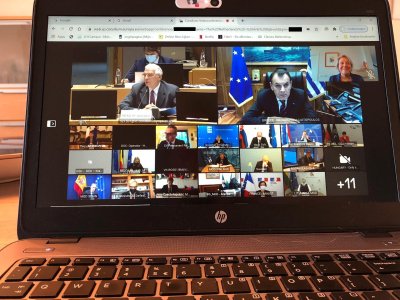
Like any other video call, if you had the link you could enter the meeting. So when Netherlands Defence Minister Ank Bijleveld Tweeted a photo of a video call last Friday, the address bar of the browser gave away the secret to anyone with a keen eye. Dutch journalist Daniël Verlaan working for the broadcaster RTL saw the URL on the screen and deduced the login credentials for the meeting.
We say “deduced”, but in fact there were five of the six digits in the PIN in the clear in the URL, leaving him with the difficult task of performing a one-digit brute-force attack and joining with the username “admin”. He joined and revealed his presence, then was admonished for committing a criminal offence before he left.
On one level it’s an opportunity for a good laugh at the expense of the defence ministers, and we certainly wouldn’t want to be Ank Bijleveld or probably the EU’s online security people once the inevitable investigation into this gets under way. It seems scarcely credible that the secrecy on such a high-security meeting could have sat upon such a shaky foundation without for example some form of two-factor authentication using the kind of hardware available only to governments.
EU policy is decided not by individual ministries but by delicate round-table summits of all 27 countries. In a pandemic these have shifted to being half-online and half in-real-life, so this EU defence ministers’ meeting had the usual mosaic video feed of politicians and national flags. And one Zoom-bombing journalist.
















That last digit does make it a hack and unlawful, but my greatest concern is that governments trust Zoom at all.
The screenshot doesn’t look like Zoom to me. (I had the same thought!)
– Yeah, the article doesn’t say Zoom, but titling the article ‘zoombombing’ kind of leads that way… Not Zoom-hosted – bigger fail seems to be “consilium video conferencing platform” putting pin/cred info right in the URL shown making this easy to do…
It’s from pexip
I don’t know the first thing about laws, but iirc, that is how it works in the US, not everywhere.
In the Netherlands this might result in a 100 € fine for RTL for guessing a decimal digit and a thank-you letter from the minister herself for having pointed out the blatant IT security vulnerability, combined with a fine worded request to approach these matters more tactfully in future attacks to spare her the embarrassment.
Zoom? for a supposedly truly secure government meeting? ha ha ha ha ah ha!
In The Netherlands it is not allowed to use any web conference tool to discuss defence issues.
But hey these are EU morons don’t confuse this with government.
This time last year I’d never heard of Zoom, and now we have governments using it. Given that this isn’t the first Zoom conference we have seen being infiltrated, I do wonder what the attraction is. My suspicion is that it’s ease of use compared to other offerings.
It’s not zoom, and if it was, the PIN wouldn’t have been exposed in the URL. This is probably the EU’s private “high” security video conferencing tool. Got to build something with £350m/week.
“This is probably the EU’s private “high” security video conferencing tool. Got to build something with £350m/week.” thats what I call enterprise software. Very expensive, closed source, bodged together, bad security, built on bullshit framework/language….
“Got to build something with £350m/week.”
…instead of giving it to the NHS :P
This is why you need to have a conference room, a bald wig, a grey suit and a white cat ready.
LOL!
I think that the irresposible thing to do would have not highlighed the error. Otherwise it could have been used by someone with a different agenda. So Zoombombing was really the easiest way to bring it to everyones notice, along with getting some free publicity.
Good job,
I wish he had also worn a spiderman mask and talk about refugees’ sunken boats as spiderman might be the only person these guys would listen carefully
Did you notice the bookmarks?
Either it’s a professional laptop and I’m afraid of the time spend watching movies during his job, or it’s his personal device and I’m quite sure that this is not a well secured one!
A pity!
‘s/ his / her /g’
I also noticed a Gmail tab.
My thoughts too..
However (almost) all people use their work laptop/PC for private stuff. This makes our govenment more human like ;)
>EU policy is decided not by individual ministries but by delicate round-table summits of all 27 countries.
EU policy is not decided by summits, but by a commission of bureaucrats who are not elected but appointed to the task, who make the policy proposals and initiatives, which are then voted on by the council of national ministers and the parlament of representatives from each country.
https://en.wikipedia.org/wiki/Institutions_of_the_European_Union#/media/File:Organs_of_the_European_Union.svg
This is the usual way a government works: career bureaucrats do the actual policy, and populist politicians vote yay/nay depending on which option benefits them personally. In the normal case, the bureaucrats can expect the representatives to simply act as rubber stamps, because despite their disagreements about the policy, there’s still a 50/50 chance it will pass anyways.
Is it just me that’s absolutely horrified by the number of governments using Zoom over shaky Wifi?
That is definitely not zoom. The interface is different
It seems to be a videoconferencing solution called “Pexip infinity connect”.
from their website: https://www.pexip.com/security
We offer security-first, enterprise-grade video conferencing solutions using industry-standard encryption and security protocols to maintain privacy and security.
for a company which has the pincode in the URL (yep, handy if you forward the link…)
“…without for example some form of two-factor authentication using the kind of hardware available only to governments”
It’s a little depressing to see this kind of comment on hackaday – secure 2 factor is mathematics and convenience, not top-secret hardware, and far more likely to be actually used if it is simple and convenient, such as a mobile phone based system
How were they not using a VPN or the like!?
What if her were to have joined without a camera and microphone and just put in some believable name? He could have simply sat there and recorded everything and for who knows how long? This is cool!
So you think they wouldn’t notice there’s now an extra country in the union?
UK is opening up a spot soon, so no problemo
MoD SUOMI PERKELE: Part 2
would not fear to be money on the fact they wouldn’t notice at all…
so why isn’t the first sentence of this article saying it wasn’t zoom???? Or didn’t the author know?
EU and military intelligence cannot mix. A house of cards.