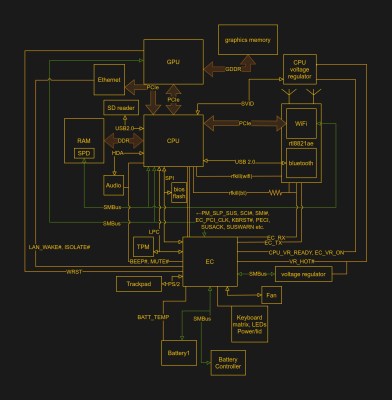
In the interest of simplification or abstraction, we like to think of the laptop on the kitchen table as a single discrete unit of processing. In fact, there is a surprisingly large number of small processors alongside the many cores that make up the processor. [8051enthusiast] dove into the Realtek rtl8821ae WiFi chip on his laptop and extracted the firmware. The Realtek rtl8821ae chip is a fairly standard Realtek chip as seen in this unboxing (which is where the main image comes from).
True to his name, [8051enthusiast] was pleased to find that the rtl8821ae was clearly based on the Intel 8051. The firmware was loaded on startup from a known file path and loaded onto the chip sitting in an M.2 slot. Careful consideration, [8051enthusiast] reasoned that the firmware was using RTX51 Tiny, which is a small real-time kernel.
The firmware is loaded at 0x4000 but it calls to code below that address, which means there is a ROM on the chip that contains some code. The easiest way to extract it would be to write some custom code that just copies the masked ROM back to the main CPU via the shared memory-mapped config space, but the firmware is checksummed by the masked ROM code. However, the checksum is just a 16-bit XOR. With a tweak in the kernel to allow accessing the shared config space from userspace, [8051enthusiast] was on his way to a complete firmware image.
Next, [8051enthusiast] looked at what could be done with his newfound hackability. The keyboard matrix is read by the Embedded Controller (EC), which happens to be another 8051 based microcontroller. There also happens to be an RX and a TX trace from the EC to the m.2 slot (where the rtl8821ae is). This has to do with 0x80 postcodes from the processor being routed out somewhere accessible via the EC. With a bit of custom code on both the EC and the WiFi chip, [8051enthusiast] had a keylogger that didn’t run on the main processor broadcasting the PS/2 keystrokes as UDP packets.
Of course, there are plenty of other 8051 based devices out there just waiting to be discovered. Like this 8051 based e-ink display controller.
[Main image source: Realtek RTL8821AE unboxing on YouTube by Евгений Горохов]
















mind blown :O
kudos to 8051enthusiast
RX/TX are NOT used, as they aren’t connected directly between EC and the wifi chip, he had to use a subterfuge with another pin, its right there under the diagram.
This open a new diy backdoor , and a high potencial risk for almost all laptops, if someone got for some minutes your laptop, could change your mind wifi probably left under couple of screws, and that’s all , new way for discovering infidelity, or steal bank account or check your navigation history
>if someone got for some minutes your laptop
This has pretty much always and universally been the case. Hardware access == game over.
As much as I hate to say it, TPM is all about making Hardware Access == Game just beginning.
Making it more difficult for Eve, but also less flexible for Alice and Bob.
Slightly more difficult for Eve in a few cases while adding even more vectors for Eve to Own Alice and Bob.
With HW access all bets are off. Permanently.
Extended hardware access sure. But 5 seconds? 2 minutes? At this point, you’re just playing for time but the game isn’t won.
I can think of some uses: flood the market with tainted computer parts. Become a wholesale dealer, resale, retail, computer repair shop, etcetera. Think of how much you could poison the world within 10-20 years of time!
A scary thought What if what you said already happened 20 years ago?
It doesn’t require any hardware access. The firmware is loaded to the cards by software on booting the card.
> new way for discovering infidelity,
LOL, or they could just read your Hackaday comments.
yep, we even have a term for this, Evil Maid Attack
Excellent way to steal Bitcoin passphrases by selling used laptops, better than mining.
Also I would imagine NSA already uses this.
What about Macbooks?
Yeah I’m pretty sure the nsa puts it in on the manufacturing line.
Correct. Look up the intel management engine, ARM’s TrustZone and AMD’s PSP. Everything core 2 duo and newer is compromised.
Everything core 2 duo and earlier is compromised due to Spectre. ME_cleaner on an ivybridge thinkpad is the best we have these days.
Some kind of owner-controlled secure boot (ie with a user-fused key) would be nice (rather than trusting the BIOS SPI chip as the root of trust), but that didn’t become a thing until Haswell and you can bet Intel locked it down thoroughly.
ME_cleaner on an ivybridge thinkpad with spectre-mitigating microcode updates (which sadly we won’t get any more of)*
It wouldn’t really work this way (unfortunately? lol). The firmware is loaded from user space for most of these cards and is part of the driver, so any driver update or software refresh would wipe any exploits.
A new driver would wipe this version. With that level of access, the 8051 might be convinced to read its firmware from somewhere else, or report that it has updated without updating. This is just a demonstration of the vulnerability, the real exploit will have a few more neat tricks.
exactly, Ken Thompson’s refections on Trusting Trust shows its self once again to be the root password for evil.
I wonder if it would be possible to get in there and hack the radio to do more than standard wifi?
This was my thought. Even if nothing more than wifi possibly improving connectivity, increasing the radio output power, ensuring the firmware doesn’t actually contain any trackers, recorders, keyloggers, etc…
Would be neat to make it work with the ZigBee protocol.
I can’t even make a peanut butter sandwich.
Welcome to the place to help you learn that and more.
BLE and now add this! Computers are just a chest full of hackers fantasies and realities! The future looks pretty dim for the uninformed and anti tech savvy suckers. Over all we are all doomed one way or another. So much for future tech dreamers of a great world.
I’ve said for along time that we no longer have mere computers, we have computers built out of several smaller computers.
** I’ve said for a long time
“I’ve said for along time” means you’ve said the word “for” along time, opposed to saying something for A unit of time…
The more you know 🌈
Don’t give the idiots ideas.
Also thanks for the idea… 🤔
So how many computers (processor/programmable memory) are in a consumer PC/laptop, and what/where are they?
I have been wondering this for a while, haven’t found much on it.
There’s an entire separate computer and os just in the cpu. Almost every subsystem has it’s own ‘computer’, the keyboard controller, hard disks (usually multiple cpus), sdcards, even usb C cables.
So, a lot.
This kinda thing has been the norm for intelligence agencies for quite some time.
Intercept a delivery of technology, add your exploit, and have it delivered to the recipient.
Without a low level examination of every chip in the machine, it’s impossible to tell it’s been exploited and is stealing your information.
Wouldn’t a tool like wireshark be able to detect something like this?
Now this is proper old school Hackaday content.
Nicely done.