Apple AirTags are useful little devices. They essentially use iPhones in the wild as a mesh network to tell the owner where the AirTag is. Now, researchers have shown that it’s possible to clone these devices.
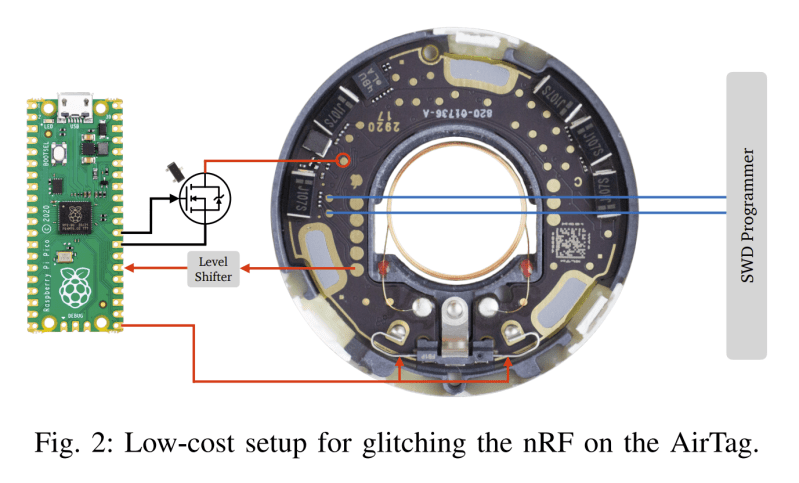
The research paper explains the cloning process, which requires physical access to the hardware. To achieve the hack, the Nordic nRF52832 inside the AirTag must be voltage glitched to enable its debug port. The researchers were able to achieve this with relatively simple tools, using a Pi Pico fitted with a few additional components.
With the debug interface enabled, it’s simple to extract the microcontroller’s firmware. It’s then possible to clone this firmware onto another tag. The team also experimented with other hacks, like having the AirTag regularly rotate its ID to avoid triggering anti-stalking warnings built into Apple’s tracing system.
As the researchers explain, it’s clear that AirTags can’t really be secure as long as they’re based on a microcontroller that is vulnerable to such attacks. It’s not the first AirTag cloning we’ve seen either. They’re an interesting device with some serious privacy and safety implications, so it pays to stay abreast of developments in this area.
[Thanks to Itay for the tip!]















I understand the alerting system, but having had a RZR stolen from me last year, I’d love to have it track without alerting someone that the device is following them. Perhaps I could have gotten my ride back or alerted police to it’s presence. I do understand how unscrupulous people would use this to track unsuspecting victims.
if it’s expensive, buy a GSM/LTE based tracker…chinese clones are like $25 and you can self-host the server part (search for Traccar)
Airtags will work only near iPhones…
“Only work near iPhones” sounds a bit misleading. Because iPhones are damn near everywhere, and if you happen to have one – it’ll even give you a range/directional heading once you get close enough. There have even been people who have sent things to North Korea, and been able to track them the whole way while only working “near iPhones”
Can you use this to find an Airbag that is stalking you?
Yeah they only work near apple devices enabled with “find my” app. Apple has over 1 billion customers and that is more than triple samsung or tile users so stfu and get lost cos apple air tags are the leader in this market loser
I didn’t know Find My was basically using crowdsourced GPS-that-is-not-GPS.
Good, now perhaps the software can be reverse engineered to locate the phone tracking the airtag, so when you find one in your car, you can hunt down the stalker and beat him to death.
Why so violent? I would just put the airtag on my shoe and return it to sender where the sun doesn’t shine. Always got to stay in the legal frame :)
I’d put it somewhere on a random semi (lorry -Jenny) or railroad car.
I’ve always found this to be a rather creepy product; I can’t think of many legitimate use cases, and while they have a stalker alert for iPhone users, anyone without an iPhone is apparently fair game.
This should never have existed, and Apple should be sued into oblivion for making a tracker that seems specifically designed for stalkers, robbers and sexual predators, with many known cases of such “use”.
You could say the same about knives.
AirTags certainly do have legitimate uses – certain people *ahem Mrs Rex* seem incapable of putting their keys in one place. Putting them in your checked luggage can also provide reassurance and even help when the bag suddenly disappears without trace.
Checked luggage is the use case I had a couple days ago. At the Miami airport 2 of my bags made it, the other was missing. Didn’t take long to figure out it went to the wrong carousel so it was very close but would have taken hours/days for the airline to find it.
What ludicrous assertion. They’re useful for tracking anything that might be lost or stolen. A purse, bike, car… do we really have to spell this out?
Android apps exist to scan for them. Apple devices even warn you. Where do you take it from they can protect against theft? What ludicrous assertion!
android apps and apple devices also notify the thieves, warning them to find, remove, and discard. CONGRATS you can track your airtag and get IT back. Sorry about your swag.
And as a result,….
USELESS AGAINST THEFT
Lots of decent uses actually. Stuff them in a backpack, camera bag, purse, attach them to keys, dogs who like to go on adventures.
Hysteria. From pets to bags to small children there’s no end of usecases for these.
Personal use cases here: Multiple sets of car keys. Wallet. Backpack. Embedded/hidden one into my laptop(should submit that one to hackaday). Dogs (attached to collars). One particularly useful feature is you can set them to notify you if you leave something behind, such as if you accidentally leave your wallet home, or a bag at a hotel, etc. They are no doubt a flawed device/implementation but the use case is there for such a thing. I think the use case to stick one on a dog collar is huge. Pets are lost every day and unless they end up in the middle of the forest it is going to ping off an iPhone somewhere sometime.
There is an Android app that purports to locate AirTags within range, though I’ve tried it a few times and never seen it trigger.
I’m surprised someone hasn’t built an appliance that you could keep in your car that would alert you.
AirGuard, and it does work for me at least. I get notifications mostly about AirPods though, not Tags.
I’d love to see a business crop up around this. If you find you’re being tracked, they clone the tracker 10 times and scatter them around your area.
no, you give one to a local “problem solver” along with some motivation money and let him…solve…the problem how he sees fit.
But why? And “rotate its ID to avoid triggering anti-stalking warnings” again, why?
I originally got an Airtag in my car in case it was stolen (like the one it replaced). Now, it’s basically useless for that purpose because it’ll just advertise itself to a thief.
There’s plenty of other security “things” too, so I’m not reliant on just the Airtag.
Why what exactly? Why demonstrate the insecurity of a popular system? So it’s known about and not just by people using it for nefarious purposes. There is an entire field of security research, are you confused about it’s existence?
One of my coworkers had her iPhone keep telling her an airtag was nearby every time she went to her car. She eventually went to her mechanic that located one tucked up under the wheel well. She didn’t have any crazy ex’s (sp?) or anything but it creeped her the F out. Unless some super-weirdo did it (possible I guess) I got to thinking about alternate explanations. Maybe some guerrilla market research company (purpose?) or car insurance or something of the sort? Who knows.
That sounds like one for the police!
I wonder if they can trace the thing back to it’s owner? Would Apple assist or obstruct?
*Its, damn autocorrect.
I’ve heard them being used to follow a car home & steal it while the owner sleeps, which is probably one of the less creepy options TBH.
> AirTags can’t really be secure as long as they’re based on a microcontroller that is vulnerable to such attacks
So all we need to do is fine a micro that isn’t vulnerable to attacks, sorted.
/s, natch.
Could this method help to reuse a found airtag? My parents found one walking in the woods, it would be a pity to just have to throw away valuable hardware.
An airtag walking in the woods? Curiouser and curiouser!” cried Alice.
[sorry, couldn’t resist]
I keep reading about voltage glitching as an attack vector – or should I call it a “diagnostic technique”? ;-) Anyway, it strikes me that manufacturers could – with perhaps a slightly bigger package – incorporate supply bypass capacitors that would reduce or eliminate the ability of glitching to put a chip into an (un)desired state. With enough capacitance they might even be able to get away with a small amount of series resistance between the external world and the bypass capacitor; this would further slow rise and fall times. De-capping such an IC might be necessary in order to make glitching viable.
I’ve never tried glitching and don’t know a lot about it – am I missing something?
Is there a nice tool yet to find these things with an RTL-SDR or similar?