There are a few possible ways to do a teardown of new electronics like the Apple AirTag 2 tracker, with [electronupdate] opting to go down to the silicon level, with die shots of the major ICs in a recent teardown video. Some high-resolution photos are also found on the separate blog page.
There are a few possible ways to do a teardown of new electronics like the Apple AirTag 2 tracker, with [electronupdate] opting to go down to the silicon level, with die shots of the major ICs in a recent teardown video. Some high-resolution photos are also found on the separate blog page.
First we get to see the outside of the device, followed by the individual layers of the sandwiched rings of the device, starting with the small speaker, which is surrounded by the antenna for the ultrawide band (UWB) feature.
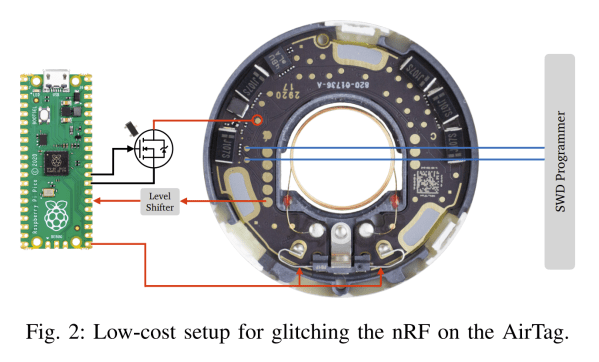
Next is the PCB layer, with a brief analysis of the main ICs, before they get lifted off and decapped for an intimate look at their insides. These include the Nordic Semiconductor nRF52840 Bluetooth chip, which also runs the firmware of the device.
The big corroded-looking grey rectangle on the PCB is the UWB chip assembly, with the die shot visible in the heading image. It provides the localization feature of the AirTag that allows you to tell where the tag is precisely. In the die analysis we get a basic explanation of what the structures visible are for. Basically it uses an array of antennae that allows the determination of time-of-flight and with it the direction of the requesting device relative to it.
In addition to die shots of the BT and UWB chips we also get the die shot of the Bosch-made accelerometer chip, as well as an SPI memory device, likely an EEPROM of some description.
As for disabling the speaker in these AirTag 2 devices, it’s nestled deep inside, well away from the battery. This is said to make disabling it much harder without a destructive disassembly, yet as iFixit demonstrated, it’s actually fairly easy to do it non-destructively.
Continue reading “Teardown Of An Apple AirTag 2 With Die Shots”