Looking to expand their hardware design experience, [mentalburden] recently put together a low-cost handheld gadget that can be used for various security-related tasks such as logging WiFi traffic, operating as a dead drop, and performing deauthentication attacks.
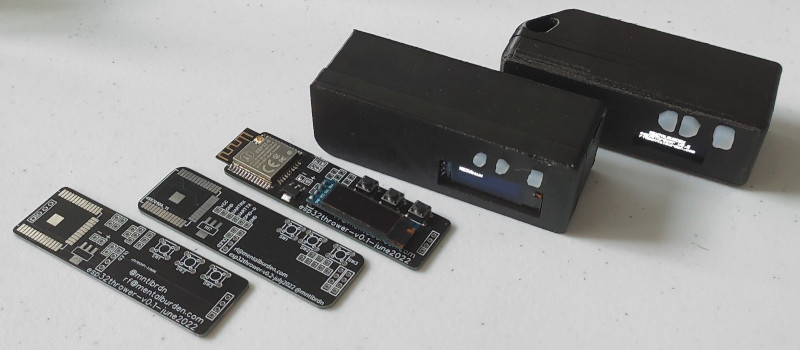
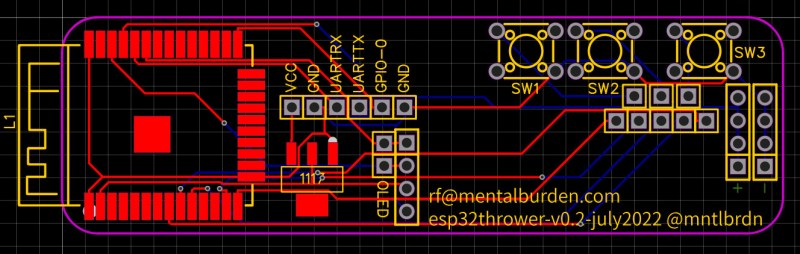
The custom PCB plays host to the essentials — an ESP32-S microcontroller, AMS1117 3.3 V regulator, a SSD1306 OLED, and a couple of buttons. This lets the user navigate through a simple menu system and select whatever function they wish to enable. During testing, a pair of 18650 cells kept the electronics running for an impressive 22 hours.
A second version of the PCB fixed a few bodges that were required to get the original prototype working, and given how energy efficient the hardware ended up being, [mentalburden] decided to drop the power supply down to a single 18650 for a total runtime of around 15 hours. A 3D printed case and some silicone buttons, produced with a simple clay mold, completed the package.
There’s still some improvements that could be made, namely integrating a battery charging circuit into the PCB and switching over to USB-C, but overall its a solid prototype with an impressive per-unit cost of less than $10 USD. Though if you’re looking for something even cheaper, we’ve seen an even more simplistic approach based on the ESP-01.















Meh. I wrote code for the TTGo Twatch 2020 v1 for packet injection (Broadcast Deauth, and beacon spam) tied into lvgl. A bonus is it also provides smartwatch functionality. Battery life is terrible while injecting though.
Unless he wanted the learning exp. I would just have used a M5Stack Core2
Literally the very first words of this post say it was done as a learning exercise. Though that doesn’t change the fact this cost $8 compared to the $50 for the M5Stack.
Why even comment if you clearly didn’t read any of the story?
ESP8266 is $7.50 or cheaper and would do the job
[mentalburden] is really worried about Shenzhen:
“EasyEDA and JLCPCB/LCSC are my favorite, just make sure to obfuscate your traces and partition the circuit with thru hole headers. This allows you to fly wire the final result while ensuring our friends in shenzen dont “borrow” your idea. Oh, and always run EasyEDA from a VM… Because reasons @_@”
and
“Consider using SMD jumpers (0 ohm resistors) instead of flywire jumpers for the circuit partitioning. Its important to ensure the design is segmented, because shenzen, but SMD jumpers are a more elegant solution.”
Does EasyEDA deliver malware? Do through-holes and SMD jumpers “thwart” anyone who’s even remotely interested? And how much does it matter if someone in Shenzhen copies something you’ve openly published?
Even smart people suffer from paranoia sometimes.
“Just because you’re paranoid, doesn’t mean someone isn’t out to get you!”
If later, you find out that they were plotting on you does it mean you weren’t paranoid?
“That’s some catch…”
If you are that worried, use kicad. You can do a lot more with it than with easyEDA anyways.
Also, that board has all of 5 parts on it, 3 of which are buttons. Like there’s not even filtering caps on the power rails. It would probably be more work to steal that design than to recreate it.
At a “per unit” cost of $10, would it even make sense to copy it? Unless you’re doing huge quantities, just buy them and use all your “free time” for coding…and everything else😏