A modchip is a small PCB that mounts directly on a larger board, tapping into points on that board to make it do something it wasn’t meant to do. We’ve typically seen modchips used with gaming consoles of yore, bypassing DRM protections in a way that a software hacks couldn’t quite do. As software complexity and therefore attack surface increased on newer consoles, software hacks have taken the stage. However, on more integrated pieces of hardware, we’ll still want to return to the old methods – and that’s what this modchip-based hack of a Starlink terminal brings us.
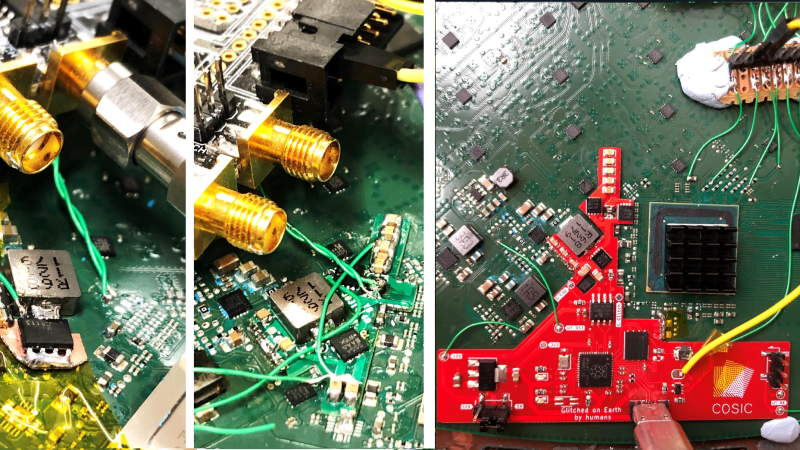
[Lennert Wouters]’ team has been poking and prodding at the Starlink User Terminal, trying to get root access, and needed to bypass the ARM Trusted Firmware boot-time integrity checks. The terminal’s PCB is satellite-dish-sized, so things like laser fault injection are hard to set up – hence, they went the voltage injection route. Much poking and prodding later, they developed a way to reliably glitch the CPU into verifying a faulty firmware, and got to a root shell – the journey described in a BlackHat talk embedded below.
To make the hack more compact, repeatable and cheap, they decided to move it from a mess of wires and boards into slim form-factor, and that’s where the modchip design was made. For that, they put the terminal PCB into a scanner, traced a board outline out, loaded it into KiCad, and put all the necessary voltage glitching and monitoring parts on a single board, driven by the venerable RP2040 – this board has everything you’d need if you wanted to get root on the Starlink User Terminal. Thanks to the modchip design’s flexibility, when Starlink released a firmware update disabling the UART output used for monitoring, they could easily re-route the signal to an eMMC data line instead. Currently, the KiCad source files aren’t available, but there’s Gerber and BOM files on GitHub in case we want to make our own!
Hacks like these, undoubtedly, set a new bar for what we can achieve while bypassing security protections. Hackers have been designing all kinds of modchips, for both proprietary and open tech – we’ve seen one that lets you use third-party filters in your “smart” air purifier, another that lets you use your own filament with certain 3D printers, but there’s also one that lets you add a ton of games to an ArduBoy. With RP2040 in particular, just this year we’ve seen used to build a Nintendo 64 flash cart, a PlayStation 1 memory card, and a mod that adds homebrew support to a GameCube. If you were looking to build hardware addons that improve upon tech you use, whether by removing protections or adding features, there’s no better time than nowadays!















Why?
Because it’s a clever hack, which is justification enough IMO.
Crikey guys! So many nay-sayers!
Haven’t any of you ever done anything for fun?
Nothing new here. We where performing voltage glitches in the 90s to gain entrance into things we where not authorized to do.
Think H cards, HU cards, etc.
Hu cards I was in high school good times
If you have to ask the question you wouldn’t understand the answer.
“Why?”
So I can connect to my own constellation of satellites, duh!
>>…commonly done on Dish and DirectTV network smart cards decades ago…
Ah, the olds days of interesting devices and pirate dens.
Whats the point? So you can get free starlink? That wont last or can you hack it to by pass the CGNAT crap? Seems like a big waste of time. And just like all the loosers who hacked Direct they got nailed by the FCC. Open your wallets hope they are full.
*losers
“no way in hell do I trust Musk’s company, especially with him in the state he’s currently in, strung out on stimulants, to keep this hardware patched” is a pretty good reason. also potentially plenty of additional useful utilities you could run on it — better packet filtering, any number of other things.
Do you have any evidence that Elon Musk takes stimulants? I couldn’t find anything on the net, do you have a link?
Or is this just a sour-grapes lefty thing because Musk is allowing free speech on twitter?
Online, it’s listed that Musk takes ambien to help him sleep. His recent lefty troll image of his nightstand shows cans of *decaffeinated* coke, so there’s that as well.
Why are you defending a man who would step on you to avoid getting his slip-ons wet in a mud puddle?
This aged poorly
0xKruzr don’t be afraid of free speech :)
– for fun
– to learn something
– to modify it to do something different
– as a first step in compromising the security of the rest of the system
– any combination of the above
somethingpracticalandboringaday.com
This person is literally a security researcher at a university. This is their job. For the rest of us, it’s a neat opportunity to learn some of these classic techniques and learn more about how Starlink works.
They’ve been Hacking Satellite TV Since the nineties And still are hacking it. Both DISH & DIRECT. There are literally thousands of hacked boxes that have never been found and never will! Millions in India get DISH for $5 a month US from dishwallas that pay NOTHING!
So with root access on your star link, what possibilities does this open up? I’m dumb so help me think.
This project brought to you by university security researchers. They’re looking for security bugs, ways that an unfriendly attacker can take control of your system. Getting root makes it far easier to investigate and modify the system.
Yep, I don’t get the criticism here. As said above this is just research on how to break into things. You note they brought their findings to Starlink’s attention. Starlink even gave them a dish…. Anyway neat stuff. Not worth my time as I enjoy ‘using’ hardware… not breaking into it :) but Uni students have lots of time on their hands.
As long as it is white hat hacking
The RP2040 is venerable now, I thunk parts would have to be at least a decade old before they got that moniker.
So what’s the hack gonna do, break into the command channel and line all the sats up 340×200 and play sky-doom in 16 grayscales according to how you tile them for albedo?
Hey! That’s the opposite of country-wide blinkenlights while “hacking” power infrastructure. :-)
Or in Putin’s case “shooting at” instead of “hacking”. :-(
Nice hack that opens up quite a few possibilities I’d wager.
– SDR(A) (=SDRAstronomy – okay maybe not A but still).
– Monitoring internal Starlink stuff -> gleaming other data from that (maybe jamming evasion and what not)
– Monitoring / Tracking / pinpointing other -non Starlink – stuff?
– Receive SAT TV with Starlink.
The Starlink antenna is a phased array and it uses quite a few frequencies -> https://www.americantv.com/what-frequency-does-starlink-use.php
– Satellite network hacking maybe?
I have been trying to get far enough into it to fix the horrendous bufferbloat the starlink network has with sch_cake for a year now. Getting closer…
I think it gets that description not for the reliability and respect earned through age but for the high position of respect it holds – wonders of English means that is technically a correct usage, even if an odd one. But its hard to argue with the 2040 being respected enough to hold a high position in the toolbox.
People can stop being holes and appreciate people’s work! You got all the mod chips and other hacks because people were doing what they love and not beep about it. grow up
Never mind the Why? Why not? discussion this exact hack was already posted in August by Elliott Williams:
https://hackaday.com/2022/08/14/starlink-ground-stations-successfully-hacked/
Only new development since then is the linked Black Hat presentation.
I don’t get all the people freaking out because people want to know if this has some nonobvious use. My first thought was why would you need root on an antenna, but it never crossed my mind that it shouldn’t have been done. What’s going on here? Now people can’t ask questions? Lame.
The people asking “WHY?”: Welcome to Hackaday!
The short answer is that it doesn’t matter why. A good place to start getting more informed could be the Wikipedia article on “Hacker culture” and “Hacker”.
— Happy hacking!
A stellar hack, beautiful! The presentation is also so good! Thank you :-)
Instead of asking “why?” you should ask “why is the terminal protected?”. Other routers give you access officially and there shouldn’t be a downside to it.
If you’re worrying about MITM, you should rethink your usage of protocols like https.
I believe this is an inaccurate depiction. Buy any commercial “home router” off the shelf, and all you get are (sometimes encrypted!) binary blob firmware updates. You have no clue what (vulnerable, open source) libraries are included, what kernel it might be based on, etc. Sure on a select few routers hackers have reverse engineered how to apply your own firmware (e.g. openwrt), but in general most purchasable hardware (TVs, IOT, phones, downloadable apps, Windows, etc). I’m not saying that everything needs to be open source, but pointing out that most (99%) of devices are closed, without anything resembling root access.
“we’ve seen one that lets you use third-party filters in your “smart” air purifier”
It’s worth noting this was an RTFM failure: the Mi Purifier filter can be reset by holding a button, the NFC tag hacking is unecessary.
I guess that this will open the way for some form of GPS like tech that Elon has refused to allow.
Would it be possible to Geo spoof so a RV or Roam can be used at sea?
That seems unlikely to work, since your lon/lat is required to access the correct set of overhead satellites.