By now it’s probable that most readers will have heard about LastPass’s “Security Incident“, in which users’ password vaults were lifted from their servers. We’re told that the vaults are encrypted such that they’re of little use to anyone without futuristic computing power and a lot of time, but the damage is still done and I for one am glad that I wasn’t a subscriber to their service. But perhaps the debacle serves a very good purpose for all of us, in that it affords a much-needed opportunity for a look at the way we do passwords.
What Does A Car Ferry Have In Common With A Password?

One of my favourite ways to leave the UK is the ferry from Harwich to Hoek van Holland. There’s an odd difference between its two legs though, the UK end has airport style security with metal detectors and x-rays, while at the Hoek I simply walk through passport control onto the ferry.
It’s a particularly egregious demonstration of security theatre, the practice of overdoing largely unnecessary security measures to appear to be doing something. In the case of a car ferry it’s especially pointless to use measures on foot passengers designed to protect aircraft, when all the motorists simply drive onto the ferry unobstructed. A ferry might seem to have little relevance to password security, but the idea of security theatre it introduces is definitely of relevance in the field of passwords. How often have you encountered a website that imposes arcane rules on your choice, demanding a a specified length, that it must contain numbers, or even worse, special characters? Does this help much? I’m not convinced, and I’d like to take a little journey through the issue to find out.
Weak And Feeble Human Brains Are No Match For A Computer!
The ideal password is a long randomly-generated string designed to confound brute force cracking software. These techniques rely on trying every possible combination of characters sequentially, and the longest string with the most entropy is intended to be the one that takes the most time to reach. If you take the 95 printable ASCII characters as the alphabet, an attacker has to try 95 to the power of the string length different strings to catch everything, something that is likely to take a while. For a 10-character password that figure is 5.987369392 × 10¹⁹, you do use passwords that long, don’t you?
Unfortunately very few humans use random strings as their passwords. They aren’t memorable at all, and thus if your passwords are like this you’re probably using some kind of password manager for them. Real humans have an unfortunate propensity to behave in predictable ways rather than random ones, so they’ll use words and phrases they know and remember. And when asked to add letters, numbers, and special characters, they remain just as incapable of doing so in a random manner as they were with strings. A simple string such as jennylist becomes JennyList with capitals added, then JennyList! with a special character, and finally JennyList!1234 when it’s been padded out to fit. The developer trying to crack it can try short cuts such as given names, dog’s names, football teams, and birth years with common letter substitutions and numerical sequences, making these memorable passwords secure in appearance but with substantially reduced entropy. But it’s all OK folks, because they pass the test of having a special character, numbers, and upper-case letters.
Incorrect Horse Battery Staple
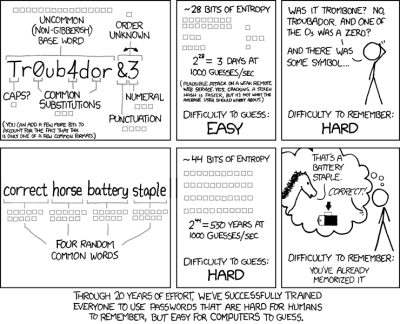
So we’ve established that password security theatre is a thing, so what are the alternatives? XKCD had a stab at it with “correct horse battery staple“, in which they put forward the idea of picking four memorable words to make a much longer password with greater entropy because of its size. This is a great way to make a memorable password, but it deserves a closer look. The attacker has only to guess four things to crack it, but that’s still OK. Assuming the owner of the password is an Anglophone and taking a back of the envelope estimate of around 250,000 English words including obsolete ones then we calculate that there are 3.90625 × 10²¹ possibilities, which is better than our random 10-character ASCII string.
The trouble is, the vocabulary of an average native English speaker is considerably less than the 250,000 figure. You can check yours here, but the average is around 20,000. When I worked for a well-known dictionary publisher we did the test and found most of us were in the 30,000 ballpark, with one specialist lexicographer colleague whose job was finding new words reaching an astounding 65,000. But if most users have 20,000 English words from which to pick their password, the number of tries drops to a more manageable 1.6 × 10¹⁷. Given that it’s more likely they will pick words with a higher frequency in the language that figure drops even further, and as they’ll tend to form a sentence rather than a random sequence the attacker can narrow down their choices even more. Are you still happy with your accurate equine power source fastener now?
Just How Far Do You Need To Go?
So the more we look at password security, the more it becomes evident that the whole edifice is built on foundations of sand. But should it be our only defence? Of course not, and we’re sure that most readers will already be using two-factor authentication, in which something you have as well as something you know becomes a factor. For many that’s a cellphone rather than a security key, but even then there’s the prospect of a miscreant hijacking your number. Is nowhere safe? Perhaps it’s time to dial back the paranoia.
There are probably several levels of service for which you need a password. Ones that don’t matter, ones that would be a mild PITA if cracked, ones that would be a major PITA, and ones that would be game over. And in turn there are several classes of attacker which you can probably classify by level of resources and by willingness to put in the work.
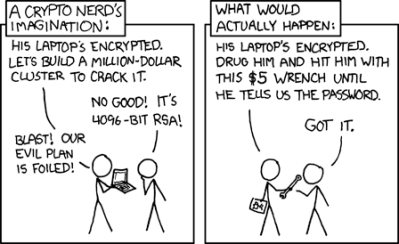
If a government agency wants your password they’ve already been through everything in your life and found it, or more likely they’ll haul you into jail and hit you with a wrench until you tell them. Likewise your local hoodlums, except they won’t bother hauling you into jail before breaking out the wrench. Scammers in a country far away will have you give it to them through a phishing scam or a piece of malware if you’re unwary enough to fall for them. Which leaves the shadowy hoodie-wearing “hackers” beloved of popular media, who will use the techniques described above on password hashes in leaked databases.
It’s clear that password security is something we all need to have on our minds, and that using two-factor authentication with regularly changed unique and entropic passwords is probably about as good as it gets without descending into paranoia. But there’s still the problem of remembering passwords for hundreds of different sites, unless you simply reset the forgotten password with another arbitrary string every time you need to use one of the less-important ones. Has the LastPass incident put paid to the use of such services, or is that just more paranoia? Maybe it’s time to revert to the most secure method of them all, and write hem on the Post-It note under your keyboard.
















No word on 2FA and second factor? No word on self-hosting with vaultwarden?
Remember kids:
The “cloud” is just someone else’s PC. If I make a mistake it is my fault, if someone else makes a mistake with my data, I’ve been a fool for trusting them.
The internet is someone else’s equipment. Try maintaining security there. Leaky, leaky, leaky, even the government does it.
I would have to look up your fallacy, but no, you can perfectly send encrypted highly sensitive data over someone else’s net without issues. If you are working with professionals.
You still have the other endpoint not under your control. Hence the “leaky, leaky, leaky” comment. Or did you all miss some of the 2022 events?
Well my point was with self-hosting that you ultimately control both endpoints. I mean I am on a site with some real clever people. You have your own servers and SSH into them with your password protected SSH keys, right?
Hence why I brought up using vaultwared to self-host your password DB. Ideally this is only required for an emergency and you have to sync from scratch with your own data to access something from another country.
I see a point in password managers and syncing, just advocating strongly that you don’t rely on a “cloud” provider. That’s a large cookie jar a lot of criminals want to stick their fingers into. There was a medium write-up how poorly the company did enforce their customers to always migrate their DB to the current state of the art level of security required. There were people still on 500 rounds! They did not enforce their own standards. PBKDF2 instead of argon2id, in 2022? What a mess.
Anyone here can read up on the subject and select enough rounds to make any dictionary attack non-viable. Lots of people on 8 char passowords and too little rounds. All of you can do better than this company. I believe in you!
(HaD is not working today)
2FA is for logging into things. If the password DB is stolen, 2FA won’t help, only your password (or password + secret key if 1password). Or am I wrong about 2FA?
I wonder, if someone had an HSM which did individual key management per encrypted password for the DB, if the DB was stolen you’d need a lot more force to crack all the passwords (this assumes the attacker was able to access only the database and has not captured the other factor(s)), and it just makes this scenario another DiD layer, more channels for the attacker to compensate for (and I don’t mean to infer obscurity here) . Probably, I think your statement about 2FA is accurate as for most common implementations.
Your computer probably does have an HSM – a TPM, and could easily do this. So would using it on the server side to HMAC a salted password with an HMAC key persistently stored in the TPM.
As far as LastPass goes, you are correct. 2FA is not used to encrypt the password DB, only to protect logins. I assumed that was the case, and their support confirmed it when we asked them.
There’s still hardware keys to help with the problem.
That’s a fancy post-it note under the desk. Not that there’s anything wrong with that. Physical security is something most of us are good at, and is much easier to see where it’s weak. Plus the type of criminals who compromise physical security don’t usually overlap with those who try to crack your accounts.
Take a single line of a song lyric, or a poem, and use the 1st letters of each word in the line. For extra security, substitute “4” for “for”, “2”, for “2”, and so on.
So for example, the wifi password at my house is: luitsiabiapiS (“Look, up in the sky, it’s a bird, it’s a plane, it’s Superman”. “Superman” is a proper name, so it should be capitalized.)
One problem with passwords in general is that lots of places require a password… but don’t really need one.
For example, lots of sites just want to be able to take a payment. If everyone had 1 password for their payment method, and if you could use that password for any online site, it would be more convenient. One password for, for example, Visa, and you don’t need an account with E-mail verification for every 2-bit vendor and shop with a web page on the internet.
Paypal is “in the direction of” a good solution to this – one system that can be used anywhere – but they’re too screwed up as a company to be truly popular.
I’m surprised none of the credit cards have implemented a paypal-like system.
Virtual card numbers.
boa used to have those. and i used them religiously. then they dropped them without any excuse or reason and now i have to change my cc# at two dozen sites every six months. morons. clueless morons. /guy
Yes, they were great for ordering from lesser-known vendors or place i might not ever order from again.
I use privacy.com for my virtual cards. Anything I pay for monthly has its own card. If I want to buy something online, I can use what they call a burner card. One use and then it closes the card.
That likely had a lot to due with their stuff being based on Java applet then Flash, both of which finally died. I think they just couldn’t be arsed to rewrite it again, and there was not another dying technology like SilverLight left to port it to.
If an attacker knew your method of password generation, they could construct a weighted password generator and perform brute force attacks more easily — just weight more common English starting letters highly, and give them a slight chance of being uppercase.
draw a picture of a cat or something in ms paint, save the file. then use a hash function on the file and use the result as a password.
> So for example, the wifi password at my house is: luitsiabiapiS (“Look, up in the sky, it’s a bird, it’s a plane, it’s Superman”.
> “Superman” is a proper name, so it should be capitalized.)
To be honest….according to password complexity (luitsiabiapiS) isn’t good enough to considered secure.
It’s not just the length that is important, but also the entropy (eg. the difference or variance between digits).
You really need to use a mix of lower/uppercase letters, numbers, and symbols with no repeats — by only using letters (no numbers
or symbols) you have made it twice as easy to crack by reducing the keyspace by about 40 to 50% (ie. from 121 possible values to only 52).
That only applies if the attacker knows what symbol groups you use or omit. If the attacker does not know then the brute force tool must consider all of them possible. So it is not about the used password entropy, but about the potential password entropy.
Of course, it might make sense to first try all the passwords with no numbers, but 13 characters wifi password will take a bit of a time to crack even without numbers. And it requires a physical presence (neighbour?).
If they have a lot of password databases, and you’re using the same symbols that are commonly used (the easy ones) then they do know what symbols you used, even if they don’t know your exact generation scheme.
> That only applies if the attacker knows what symbol groups you use
or omit. If the attacker does not know then the brute force tool must
consider all of them possible.
No, it always applies….irrespective of what the attacker does or
doesn’t know.
The software and hardware available for password cracking has gotten
more sophisticated such that brute-force, or exhaustive search,
attacks can be done much more quickly and with less expertise needed.
Moreover, if the attacker knows something about the service, that the
login is tied to, then they likely already have a fairly good idea
about what the minimum length is and what possible digits are used —
most sites will (incorrectly) give you this info when creating an
account. This also does not preclude the possibility of social
engineering or phishing attacks to further reduce the amount of work
needed to be done.
> but 13 characters wifi password will take a bit of a time to crack
even without numbers. And it requires a physical presence
(neighbour?).
It doesn’t have to be a neighbor, nor does it require physical access
to crack.
Physical access is only required during the data collection phase
(ie. war-driving). After the data has been collected, the attacker
can leave and do the cracking offline themselves or farm it out to a
third-party with more processing capability.
It’s even easier if someone is still using WEP (as I’m sure there are
still people out there that are), or heaven forbid no encryption at
all.
Apple Pay/Google Pay
Those are awful. They “anonymize” the transaction through a throw-away account, but Google still keeps a record of it, so they can then sell the information to the company anyways. I refuse to use these sort of man-in-the-middle extortion “services”.
I end up doing this but substitute special characters for certain letters etc. Gives a bit higher entropy. I simply use the password generator included in *insert favorite password manager here* to generate the rest of my passwords. The downside is I will never remember them. But that’s really what password managers are for; generating and storing secure passwords.
“nggyu,nglyd”
I like the idea of a password manager and long random-character passwords but I don’t like the idea of using some cloud service for it.
That’s why I use KeePass. They do kind of encourage syncing between devices using DropBox or similar services. Again.. don’t want to keep all my passwords on someone else’s server. Fortunately many of the KeePass clients support syncing via scp. That works great for me!
Not to mention when they use fuzzy logic.
[ Looking at you Facebook. ]
You can still log in even with a slight username error.
So getting the password wrong a few times causes a pain of trying to reset it.
But if you start with the password and guess the username, there’s not a lot of guessing to gain some access.
Not using the cloud is so obvious when you want security. I use strong passwords AND keepassx as well.
KeePass is good.
I use pass, which has the virtue of extreme simplicity. GPG encrypted text files. Organize them, back ’em up however you want. https://www.passwordstore.org/ Different password for every important service, but a common, weak password for the ones that don’t matter.
Probably only works for Linux with xclip, but I actually use a wrapper around pass that copies the password into the clipboard, and the second line in the file, which I save for username, into the primary selection. So a center-click pastes the name, and a ctrl-v the password.
The real killer app for the web password stores, however, is when you have to share credentials with an organization.
I used to do that, too, right up to the point where Dropbox admitted that they can still read all your files if they want to, despite them being encrypted. https://www.cbsnews.com/news/at-dropbox-even-we-cant-see-your-dat-er-nevermind-update/
So now I use nextcloud, truenas, and openvpn instead.
You used to use KeePass with scp directly to your own machine until you heard about Dropbox’s security problem??
Add another vote for KeePass! It runs locally on your own PC, is portable (can run from USB stick), and can use an image instead of a master password.
I use KeePass on Linux and Android. I host my password vault on my server. I also keep a copy locally on my phone and tablet just in case I have no Internet connection. I use a key file. It is used to add a layer of encryption to my vault. Without that file good luck decrypting my vault. It is not on my server so if you get my vault you will not be able to decrypt it.
And you can have a separate binary file as part of the “key” separate from the db and login password… That binary file can be stored on a thumb or a separate networked computer. Keypass has been used by me for years, I too, enjoy the “off-line”, just have to manage the updates accross the other machines. It also has a pretty good multifunction password generator..
for like protecting a private key that is going to be compromised, you really might want to be secure against billions of attempts. and that really is a scenario that happens, specifically if you let outsiders store your private keys (like password vaults)! and combining things like 4 common words, a misspelling, and an oddly-placed punctuation can accomplish that.
but i never do that, and the only private keys i have that i’m worried about if they get out are passwordless ssh keys and if they are compromised i’m in for a world of hurt…hopefully i notice and invalidate them real quick!
all of the passwords i care about today are for access to specific services. and for that, relatively unambitious strategies are fine. most highly-sensitive services (i.e., banks) will lock you out after less than a dozen attempts. and even things that allow unlimited attempts will generally have enough delay/rate-limiting that the idea of having more than a few million attempts is implausible even if it’s allowed to go on unchecked for months.
passwords are a tool to accomplish a task and as long as my accounts aren’t being compromised (and i can get in, myself), that tool is serving my purposes. security by obscurity is another example of a tool that can work very well, you just need to know its limitations. not giving a hoot is another valid security tool, if you recognize its limitations. i’m just advocating for a degree of materialism in these sorts of assessments…things aren’t bad in a vacuum of philosophical analysis, they’re only good or bad in relation to how they’re used.
i recently had my credit card compromised by a vendor who stored my cc# and shared it with others after insisting they would do neither of those things. they had a high duty of care and they failed it, but my personal password was neither here-nor-there for that compromise — they report they had more than a million customers compromised. you have to know the value of what you’re protecting to come up with a good strategy for protecting it.
Yes, this. Brute-forcing can be made unproductive by friction: a small time-delay per username or IP so that robots can’t just hammer away, and a lockout plus a warning email after X failed attempts.
Also, making companies liable if their security gets breached/hacked would be a nice incentive for them to step up their security. Lastpass… wtf?? Sure am glad I wasn’t with you.
The attacks typically happen against the hashed passwords, not at the login screen.
When someone steals the hash they can brute force it or throw rainbow tables at it as fast as they like. That’s what happened with lastpass, they are free to bruteforce those passwords all year long.
yes, that’s why i said “for like protecting a private key that is going to be compromised, you really might want to be secure against billions of attempts. and that really is a scenario that happens, specifically if you let outsiders store your private keys (like password vaults)!”
Not if you store them properly. See: password salting.
OR you could just set a lockout of 24 hours after 3 failed attempts…. what’s the math with that?
Greg A beat me to it!
Doesn’t even need to be 24 hours (as pointed out above). Just a few seconds between each attempt…. Just like when getting into my Linux systems… If I type my password wrong there is a ‘delay’ before I can enter it again. Orr A bit irritating but necessary for those brute force attacks. Instead of 1000+ attempts a second, reduced to 1 attempt per second at least…..
It leads to people being able to intentionally enter the wrong pw on your account 3x so you can’t get in. A sort of DOS attack.
True, and then you can spend the next 24 hours learning how to set up an allow-list with your IPs with slightly more permissive permissions. :)
True story: 8 year olds do this to each other on their Chromebooks and call it hacking.
Then the next year the teacher puts all the passwords for all students up on the projector at once. Can’t make this crap up.
24 hours?!?!
I take it that you NEVER mess up your own password 3 times in a row. And following that thought process you just failed your Turing test.
That’s a learning experience. Better than a security breach. But yeah I’d probably favor 5 attempts before lock
I’m glad the lockout limit is higher than that on Nintendo accounts on the Switch. The on screen keyboard means I regularly bumble my password repeatedly.
Fine for “online” brute-force attempts but not for leaked/hacked password databases where the attackers can brute-force offline at their leisure to extract the right password and log right in 1st time.
Wells Fargo increased security like this after a public ‘data leak’. Three strikes and you’re out… To unlock, you had to call a phone number from the cellphone number they had on file.
Normally that wouldn’t be an issue, just a pain. Unfortunately, I’ve never had a cell phone. So when my bank’s autopay service used the wrong password three times out of the blue… I was screwed.
It took them FOUR MONTHS and me six trips to their ‘local’ (75minute drive) office to get my account unlocked because what kind of crazy person in 2023 doesn’t have a cell phone?
Sitting there in their office with passports, SSN cards, driver licenses, birth certificates, etc…. just thinking about that Sandra Bullock movie…..
..Who Do I Gotta Kill.
j/k it was The Net.
I think the Apple/Google passkey system is going to solve this. It effectively turns your phone into a universals hardware key.
The problem then reduces to the fact that your phone is now a physical manifestation of “you” in any way that matters. The only hope for security is that the biometric access controls are sufficiently secure. Apart from that, there’s just the inconvenience of being unable to do anything when the battery is dead or it’s lost, stolen or destroyed.
And the inconvenience of the situations when your phone is taken from you, along with some redundant apendages….
If you even use/have a phone in the first place. I only have one because my company requires it. In a way I can’t wait to retire to no longer be ‘tied’ to a phone.
The phone being a physical token for authentication is not a problem. The fact that it has to be Google/Apple is the problem.
Point being, it’s not really any different from your passport, you SSID card, you driver’s license… all of which you can lose and without which you’re in a world of difficulty.
A while ago I had to prove to my bank that I have valid personal ID or else they would lock up my accounts. Only problem was, I needed a valid personal ID to apply for a valid personal ID. Meanwhile, the government had decided that a state-approved driver’s license is no longer valid personal ID because it has to have the biometric holographic embedded stuff now. My passport had expired, so I had to go to the police station to get “identified”, so I could apply for a new SSID card, so I could tell the bank that I have it. In the end, all they wanted was a photograph of the card.
What proves that I am me as far as the society is concerned is still just a laminated card that says whoever is on that photo is me.
Well the physical aspect is very important, otherwise your clone could go in your place.
Although to be sure, the bank only wanted to see a card, not whether one actually exists… so if I had wanted to cheat, I could probably have just sent them a fake photo, then use the bank’s ID services to validate myself to then claim I lost the card and get the real SSID card as a “replacement” without ever going to the police station.
There would of course be the risk that the bank checks with the authorities whether the card actually exists, but that would depend on someone actually doing their job.
Or your identical twin
> all they wanted was a photograph of the card.
This is another problem entirely…..(like paying with cash, but the bills are just photocopies).
I mean how can they be 100% sure that the card actually belongs to you (if all you show is a photocopy) — unless of course, if maybe, the card is next to your face in the photo.
Yep. Weakest link in the whole story – like faxing a signature.
> unless of course, if maybe, the card is next to your face in the photo
Now that you mention it, they did ask me to also send a photo of my face in a separate file.
But of course, I also have a printer and a laminator, so I could have just made myself a fake ID with my face on it either way. Without physically seeing the card and checking the embossing, hologram, chip… how would they tell?
It doesn’t _have to_ be Google/Apple. They designed it together with Microsoft and they were the firsts to implement it.
Oh goody, so it’s Google, Apple, or Microsoft then. Which of the three foreign multinational mega-corporations would you like to depend on as your national identity services provider?
It’s just U2F with resident keys, Yubikey will work.
The huge advantage of Google/Apple is that the FIDO alliance let’s them clone the keys (the politically correct term is sync, but it’s the same thing). You can backup your keys and use the same keys across multiple devices, much more user friendly than Yubikey. That only works when all your devices are either Google or Apple though.
>That only works when all your devices are either Google or Apple though.
Or Microsoft, which is precisely the issue.
Microsoft doesn’t have a mobile phone, so they are the inferior option.
Maybe they’ll pay Google though to get syncing between Windows Hello and the Google keychhain.
Either way, no private company – much less a foreign one – should have access or anything to do with my personal ID that identifies me as a citizen, because I use the same token to access services by my medical provider, my insurance provider, my bank, state social security, pensions… It’s just a complete no-go. It would be entirely daft to even consider such a critical service to be handed over to Google or Microsoft.
An old joke: Why do the state offices use triple ply toilet paper even though it’s much more expensive? Answer: One copy goes to the state archive, another to the CIA, the third to the KGB.
You got it all backwards. None of those corporations is the identity provider. AFAIU they implement an FIDO open standard in their products (Chrome, Safari, Edge) and that’s about it. They can store the keys in the cloud, but that’s not relevant here. Firefox could implement Passkey as well and store the secure material in their Firefox Sync service.
https://www.wired.com/2012/11/ff-mat-honan-password-hacker/ Even after a decade, this hasn’t improved much.
Remember to secure your password recovery path as well. Perfectly complex passwords (even those on post-it notes) can be thwarted by a compromised email account and 30 seconds of finding a forgot my password link.
If I am targeting you, I can spear-phish you with a better than 30% return rate on clicking a malicious link
If I am blanketing your org, I can get 30% return if you haven’t trained and practiced phishing campains 20% if you have (better if I proof read my email and correct grammar and spelling)
If I look like I am giving away a free ipad, vacation, or can entice you in some way half of you will gladly create an account and use the same password you use everywhere else.
usb stick/micro sd card in the parking lot, break room, mail… 50%, 90% if it has an official logo
You have likely been compromised enough times in enough breaches to define a pattern of variations you generally use in your passwords, and reduce your likely words from 20k to 200 and your special character
and numerical increment patterns.
Computing power scales well enough that targeting all 8 billion people wouldn’t be particularly difficult, you can no longer hide behind not being special or interesting.
Your brain relies on pattern recognition to recognize safe looking things. If I can nail a pattern that looks safe to you, I can own your accounts.
FUD for thought doesn’t really help any though.
The most helpful thing is to realize you can’t rule out the possibility that I can get access to your data and get or compromise your data with relative ease so the security practices you build should be thought of in terms of time not am I secure/insecure.
Time ratings for a locksmith to breach a vault:
Class M: 15 minutes
Class I: 30 minutes
Class II: 60 minutes
Class III: 120 minutes
Safes and vaults are not secure, they are presumed secure for an amount of time. To protect a class III vault you have to send a security guard around every 120 minutes or less to detect whether a locksmith has started the clock. Class M is secure as long as you are in the room with it.
Think of password security as a time rating. Not how long does it take to crack, but, since I’m susceptible to giving it away, how can I notice I’ve lost control and start recovering my accounts. MFA is good, multi-factor alerts of changes is also important.
Post-its move one vulnerability, and it is worth considering in addition to:
– Certificate validation whenever possible
– Isolate recovery email from daily driver so you don’t give away your retirement
– Data isn’t secure/insecure, data is secure for x amount of time once someone starts trying
– If something is free you are the product, they didn’t build sufficient security to trust with any identifying data. (prove me wrong with a link to your bug bounty program and APIs :-)
– Keep an eye on the pivot. Once they have something you don’t care about it is much easier to get to something you do care about.
– Verify important requests from a human you trust by more than one method. Don’t send money above an amount that matters to you based on just one communication source. I can spoof any one thing fairly quickly, but it is hard for me to anticipate and spoof the next thing you will try.
I was once forced to change my password to login at work, without any back-story as of why I had to do that.
I had to cycle though 20 passwords and it took me over half an hour before I could re-use my old password again.
This is why (at one time) standards recommended a minimum password age as well as a max. It prevented changing password more than 1/day, so yeah you could reuse your password, but it would take 20 days instead of 30 min.
People are still the weakest link when it comes to data security. You try to help protect users that are trying to do the right thing (following the spirit of the policy) and forgive when they make a mistake or are attacked through a spear phishing campaign. Users that are actively trying to work around security controls that are there to protect them and your company’s or customers’ data need to be encouraged to become someone else’s problem however.
The security controls are in place typically because the organization is trying to do something insecure and extremely stupid, like having a single login to everything from the company internal news board to the accounting system simply based on user privileges.
True. The more I think about it, the more I’m convinced that single login to everything is a very bad idea ™.
We change work password(s) periodically. Forced too. And of course if someone leaves the company that is in your ‘area’, all passwords need to be changed regardless as soon as notice goes out. Also, new passwords do have to follow certain rules and length to be valid for ‘change’. Life in the new world order.
“if someone leaves the company that is in your ‘area’, all passwords need to be changed regardless as soon as notice goes out”
Curious, why are you changing your passwords if someone else leaves? I’m not sure I’ve seen that level of paranoia anywhere.
Read the safe combination hacking chapter of Surely You’re Joking, Mr. Feynman!
Excellent recommendation!
Actually it is government NERC CIP standard now for changing passwords when a person ‘leaves’. Have only a set number of days to make it so…. ‘Every machine (firewalls/routers/VMs/etc) ‘ that person had access too needs new passwords as well as the co-worker personal passwords. I work in the ‘heart’ of a electrical utility. Hence we have a bunch of ‘hoops’ to jump through just in daily work. Physical Security as well as Cyber Security. Paranoid? We just have to follow the ‘rules’ … if we don’t there are penalties if found not in compliance when an audit comes through….
Is a third party password manager still viable? For most use cases, yes. Is it better than a browser native password save? Absolutely! Does it help employees use unique passwords across all the various accounts they use outside of the enterprise?
For most users, the fact that all their accounts are recorded, use unique passwords, are backed up off device AND require a password to access is light-years ahead of their current password management.
I dare to say, even a breach of LastPass in plaintext could have minimized impact with disclosure and a rush to reset critical passwords. At least you have an idea what’s exposed and can take action.
“We’re told that the vaults are encrypted such that they’re of little use to anyone without futuristic computing power and a lot of time”
Thing is, some of those guys are stealing conventionally encrypted databases cause quantum computing is just around the corner and poses a serious threat to the current state of file encryption.
“some of those guys are stealing conventionally encrypted databases”
There are 2 major forms of “conventional encryption”: symmetric, secret key encryption and asymmetric, public/private key encryption. It is public/private key encryption that is vulnerable to quantum computing.This is because the public and private keys are mathematically related. What QC enables is calculating the private key from the public key in a reasonable time.
While quantum computing does provide a small speed up to secret key encryption, AES with 256 bit keys is still infeasible, even for quantum computers.
As long as only the account users have the master passwords and have chosen strong passwords, then those vaults could well be of little use.
With a decent key size quantum computing really only changes the game from “until the heat death of the universe” to “until the sun blows up” many orders of magnitude apart, but not useful acceleration in terms of human lifespans.
what pisses me off the most are the idiots who make me change a perfectly good password every 90 days. i’ve worked in some variety of communications and network security for 45 years and it amazes me how clueless 98% of people are about what constitutes real security. /guy
I worked for a company that made us change our passwords MONTHLY for a while. You make someone try and remember a new password every month they’re going to pick something stupidly simple and repetitive.
My 1st job we had logins to about 3-5 special systems (all old terminal logins to vast mainframes dragged into the internet age) that were required to do our job, all had similar but subtly different password rules and all were mandated to be changed every month.
Literally everyone in the company had worked out almost identical patterns for changing their passwords by the time I joined, anyone caring to look could’ve worked out the system to brute-force it in seconds or indeed just use the $5 wrench to hit the nearest engineer over the head & look in the back page of his notebook.
I use a 2-byte hash of the domain name that I can calculate in my head, combined with 8-bytes of ascii that I have memorized. For the few sites that have restrictive rules about which special chars have to be used, I have a hint file with reminders like “use – instead of ! for abc.com”
biometrics are interesting — one of my daughters (at age 5) discovered that she could unlock my phone — I guess she looked enough like me. I caught her telling her sisters how to do it — Just look at it she said, but the other two couldn’t get it to work
Now you need to compare your other 2 daughters faces to the mailman’s.
B^)
I agree that passwords suck, but having them is still better than NOT having them. Case in point, Microsoft’s passwordless system. Approve a login from your phone, sounds valid, right? But all you need to initiate a login attempt is your username… your PUBLIC username, which is your email address, which a whole lot of people know. Anyone that knows your email address can initiate a login attempt and approval prompt on your phone, essentially reducing it to one-factor auth, Something You Have. (And no, fingerprint biometrics to approve the prompt does NOT add Something You Are, in this context. It does in the case of username plus Windows Hello facial recognition, but let’s be real, who uses that?)
Google on the other hand, does it right. They know your username (your email) is Something Everybody Knows, so they keep the password as part of the auth process, and only after proving Something Only You Should Know, will it then attempt the Something You Have challenge (approval prompt on your linked phone).
Passwords need fixing, but getting rid of them entirely is NOT the solution. You will ALWAYS need Something You Know (password) to prove that it’s “probably” you attempting to login, before going on to a Something You Have challenge (phone app, yubikey, etc). Even a Something You Are challenge isn’t enough (fingerprints can be lifted, facial recognition can be fooled, etc).
We need a way to create and enforce /better standards/ for Something You Know, while maintaining end-user usability (there will always be cases where hand-typing a password is your only option, like a shared computer, a bank website that disallows password managers and pasting, etc). Passphrases are a good starting point, but the idea can and should be iterated on (and while we’re at it, we need to abolish arbitrary maximum password length limits. a disturbing number of FEDERAL GOVERNMENT WEBSITES still cap you at 12-16 characters, strongly implying they’re storing plaintext. Hack This Site lets you use “tweet length” passwords, which should be more than enough for a memorable passphrase, but assuming everything’s being hashed and salted, there shouldn’t BE a length limit. I should be able to use the entire text of Homestuck as a valid password.)
…But in the end, the strongest Something You Know in the history of paradox space, still won’t protect you from a little “lead-pipe legilimency”.
I’m glad you mention salting, there’s many here talking about how leaked hash databases will let hackers get around time delays and attempt counters which otherwise prevent brute force attacks. But even if the database is leaked, it ought still be useless; Where passwords are needed, they just need to be done right.
This may be foolhardy, but when LastPass crapped the bed, I said, if I have to change my passwords, I’d rather do it AFTER migrating to a new provider. Employer provided LastPass as a site license. So now I’m paying for a competitors product out of my own pocket. Hopefully we don’t get fooled again.
my biggest problem with two factor is the specific requirement of phone ownership. i still have doubts that relying on a device that can easily be lost, stolen, or destroyed as the the keystone of security. i do not use smart phones, and if i did i sure as hell wouldn’t use it to store passwords or for two factor, i just dont trust the thing that much. there are a few sites that can do email, and others that can use an totp authenticator. most just assume that anyone who doesnt own a phone is an unperson and is unfit to use their services. its got serious mark of the beast vibes.
i think a bigger problem though is the number of things that shouldn’t require accounts that do. one of the reasons i even bother posting on had comments is that there is no requirement. people for the most part, are civil. most people would rather buy software than pirate it and would prefer to do away with all the phone home drm. frankly i miss thumbing through discs.
Yeah. My phone recently just died during the international flight. It was of course used for MFA, which caused a lot of problems.
Password security is massively misunderstood topic. My most secure password is a phrase in a foreign language, written phonetically in English letters. It uses upper and lower case letters, no numbers and no special characters. How is it so secure? Adding 4 characters increases security more than adding uppercase letters, numbers, and special characters. A slight increase in length makes a far bigger difference than increasing the number of character classes used.
I actually wrote about this a few years ago. There’s an even better strategy than using foreign words written phonetically in English. Instead use pronouncable made up words.
https://techniumadeptus.blogspot.com/2018/11/comprehensive-password-security.html
pwgen. Enough said.
The more important ones (disk encryption, backup medium encryption) are 16 chars, the less ones 8. Some intermediate level for sites out there is 12.
I memorize four or five of them, the rest is in an encrypted file.
This and *never* use one password for two unrelated things.
2FA, vaults and all this is snake oil.
I get it why companies out there who want to treat you as a commodity want you to outsource your identity (to them, at best), but I’m not a commodity, so…
(Yes, I’m looking at those fakebook, wordpress and twitter icons down there)
Yeah, I’m still using my FinalKey and it’s still the best password manager for my workflow.
Passphrases are still the best (human rememberable) option, you just need to allow for greater length and encourage punctuation and proper noun usage. Basically a ‘pass sentence’ is both memorable and has a high degree of uniqueness. Even moreso as people incorporate unique mispellings and phrasing.
^This. It’s trivially easy to make a very long and complex password this way which is not too hard to remember. Use quotes from books, lines of code, write out mathematical equations, chemical formulas or names… The biggest issue with using these is finding out that many sites and services have unstated character _maximums_, and a large fraction of those don’t fail gracefully when this limit is exceeded. The worst ones silently truncate your long passphrase to n characters when you change or create your passphrase, but accept n+m characters in the login. Slightly less bad ones limit the ‘special’ characters that are allowed. Seriously, there’s no good reason I can’t use spaces, an equals sign or symbols from foreign languages in my passwords. Or even emojis if I wanted to. If it’s a valid character, its should be allowed in a passphrase.
The site deficiencies you mention are just a result of lazy programming, or reusing code from before, which is also a form of lazy programming. It is the same reason so many sites want to use your social security number as a unique identifier. The vast majority of websites use password rules that are completely arbitrary, chosen for their ‘appearance’ of security.
i went to change my paypal password to something more secure, but i was alarmed to find out how low their maximum character count was, especially for a website that touches financial stuff. needless to say i dont use paypal anymore.
problem with using language structure is that its easy to predict. fortunately most people do not follow all the rules of grammar. im lazy with capitals you can see. others are perhaps bad with spelling or intentionally use bad spelling creatively. i like the pass phrase concept in general because long passwords are harder to crack. but posing any hard requirements on passwords will affect the diversity of all passwords and make dictionary attacks more viable.
so rather than pass phrase, why not high minimum password size with no restrictions? you dont tell people what they can do with it. it can be a phrase, a random hash, or a base64 encoded picture of your cat. a 256-byte password minimum would certainly be nice.
LOTR fans are going to have some impressive ones then.
Password must contain upper and lower case Tengwar, and at least 3 Cirth runes.
I know very little about the back end of password security and encryption and all. Can someone explain to me why having a simple 30 second delay between failed login attempts, and a longer delay of say, an hour with an alerting email to the account holder after 5 or 10 failed attempts wouldn’t basically make brute force attacks impossible? I see systems like this implemented occasionally, why aren’t they universal?
First, brute force attacks account for <1% of unauthorized access. Typically the company's own server is compromised. This means a file is copied from the server to the hacker's computer. So the hacker can now can try a nearly infinite number of possibilities as fast as they want because they're just playing with that file on their computer. Something I always thought was funny is that the 'file' that was stolen is typically sold. Eventually someone buys it, cracks a small percentage of accounts, then sells that account info.
This means that you don't have to have a good password, just a password that's not as obvious as ~50% of other users!
Second, even if someone was trying to brute force the password, the server already looks for other information like IP and computer hardware identification information. If it doesn't match to what they're accustom, they typically ask you security questions anyway.
Thanks for the reply! Makes sense.
Two way public key encryption could allow verification of the user and the website.
Sure, PKI is greater in quantity than password, but there’s always the case of fraud, forgery and theft.
Security is about 3 things: Lying, Cheating and Stealing
The whole premise of this article is based on the insecurity of using ascii text for passwords. But its security theatre in its own right. Its no use trying to mend the reputation of companies like lastpass et al that have been shown to be poor holders of passwords in fact rather than their theory. Each of them has lost all their passwords as well as other information for all sites people use.
Losing the bulk of all your most secure passwords instead of having one off accounts hacked is a huge risk that has proven to be beyond the capabilities or willingness of companies to manage. Yea someone could hack my password to a given site, but thats 1 password, AFTER they figure out what site I use and my username (both given out by this latest hack as well).
Further the article is theatre because it totally ignores the fact that we can use different cases, letter substitution, and non-alphanumerics which most security minded people nowadays do use. Then for more secure sites 2fa is available in multiple forms. Even the simplest and least secure of them still requires a compromise of an entirely different system (sms) which reduces the risk even further.
Having one place, thats a known goldmine of user security data be the place you hold it isn’t security theatre though, its worse. Its foolishness.
When I worked as a systems engineer, I had to login to dozens of Unix servers daily. I used ssh and setup my logins to use public key encryption to verify both the server, and my computer. Once that was configured, I no longer needed to login. Just ssh to the server, and the public key handshake would take care of authentication both ways. I only had to type in a password to unlock access to my private key.
Usage of default setting with xkcd password are bad .
https://www.unix-ninja.com/p/your_xkcd_passwords_are_pwned
I think if I have entered the password wrong after 5 attempts, it should just let me in.
Because, if it don’t, I might cause physical damage to it.
Our admin password for about five years back in 2004 was : M1K59+So#1
Have always remembered this. Back then the hacking/cracking/phracking/phishing wasn’t quite that of today, and I always felt it was a pretty secure password for that era.
I refuse to use any password manager. One of the cloud servcies, whichever one, was zapped some 12 months ago, and now Lastpass. And the locally installed password managers – do you have the source code to ensure that your own passwords aren’t being leaky leaky to the China-written / Russian-written / Slovenkian-written author ?
My dumb trick for the past 15 years is to use an English property name that is pronouncable, but isn’t anywhere in the English language. 21 characters long. Then add the usual three numbers, exclamation mark, three hashes for the websites mandatory special chars. I use this everywhere, but then ya add the name of the service or website and then the password change number. Ends up being a minimum 28 chars before adding the service name. Can easily blow out to 36 plus char’s. Works ok for me.
It sucks when you have to change it but.
UP UNTIL THE POINT of those few dumb web sites that have a freakin’ maximum of 12 or 16 characters as the password. What the hell dude?
Or dumb sites that refuse to have double or triple char’s in a row. What the hell x2 dude? This does nothing other than publically show the lack of entropy knowledge of the bloke who wrote that routine.
These dumb websites I find a contact , get on my soapbox and write them a letter.
…Or am I the dumbo and am missing something here?
I use “Incorrect” coz the website always says : “Your password is Incorrect”
I bet you license plate is “EXPIRED”
I’m convinced most web forms are never actually used by the person who develops them. I had a sign up form the other day that asked for a password with at least 8 characters, a number, an uppercase, and one of the following special characters: !@#$^&*. These were the only characters accepted! My randomly-generated password that also included /() was not accepted!
I have been using a method of concatenation for years, and no password is the same on a site / service.
It starts with 2 special characters, a memorable word/name with every other letter upper case, the first 3 letters of the url of the site (not the www) and a date.
It translates to something like : #$bUcKrOgErShac200979
I tell my customers to use an easily-remembered word, but mis-spell it.
Then combine two or three of these mis-spellings and add numbers and punctutation, e.g.
diamond – dymund
golf – golph
beer – beeyuh
two numbers and punctuation:
dymundgolphbeeyuh39$
Non-dictionary (except for “go” and “bee”, and maybe “yuh”), and 20 characters. Add extra punctuation if desired. $$$ or $*# takes you over 20 characters, and easy to remember, compared to random strings of lower/uppercase and numbers & punctuation. If it’s not easy to remember, you then depend on the security of password managers. And look at that, Lastpass was cracked – not the passwords themselves, but still…
>$$$
Being my gripe that a lot of website algorithms wont allow repetitive alphanumeric symbols, which I will never understand (and tied in with the password that should be at bare minimum of 16 chars)
I have started using a password keeper on my cell phone.
Yeah, insecure as it may be. But how I make it MUCH MORE DIFFICULT is that the sites that are listed for the passwords and my usernames are all puzzles based on my history of reading books and oddball names I give the vendors.
So yeah, you might get my passwords, but for WHAT? And that username will do you no good.
There’s definitely some misunderstanding of the idea behind the XKCD passwords here. The idea is to choose _random_ common words. “common” just means that the dictionary can be limited to words that you’ll know, not really obscure ones, but they should be chosen randomly, and should not be interpreted as “the first 4 words you think of”
2^44 is based on only a~2048 word dictionary, so doesn’t rely on having a large vocabulary, and the comic still makes its point, that just making it look hard to remember doesn’t mean it’s harder to guess by a machine.
What has changed over the past decade since that comic was written, is how much processing power is available. As it says, “hard” is based on 1000 guesses/sec, which is probably assuming brute-forcing a website, etc, not trying to break a locally stored hash.
If you want to make an xkcd password more secure by modern standards, just add a couple more of the most common 2048 words, and you’re there.
Ideally, you would use your 6 words as a passphrase for key based authentication instead, and patch a lot of the other large weaknesses. (key grabbing, shoulder surfing, etc.)
One of the main security issue is not the passwords, but the login name. It is usually exposed as your email. Not knowing the login name, makes it virtually impossible to guess the password.
The other stupid problem is forcing you to answer questions which ask for more unique to you private data which many muppets post on facebook etc. Silly things like first school you went to, first car you owned.
Not only can I not remember because I dont care, it’s something that many people will publically share.
Let me set my own questions and answers and they are impossible to guess as I’ll never write them down and the question/answer are not related at all.
Eg: (not one I use) Q: what colour is the sky? A: octopus
And few companies let you use the horsebatterystaple, they instead want upper/lower number special characters.
Which 99% of average people are going to write down somewhere or use commonly known methods like 3 = E, 1 = l etc.
Like my folks do, but at least they are old enough to write it on paper.
I ignored L1 certification because it’s pretty much useless and will in the future be rejected by most websites. A Firefox synced authenticator implementation would only ever get L1 certification, because there is no trusted computing environment to run third party signed code with attestation on all platforms, only SGX really. Probably one of the reasons Mozilla don’t seem to be interested in supporting passkeys.
Apple and Google get L2 certification for their synced/cloned U2F authenticator implementations, because they do have access to secure enclaves on all their synced/cloned platforms.
The lack of syncing/backup was what held back U2F, passkeys will change all that …. inside the Google or Apple ecosystems and to a lesser extent Microsoft.
My friend may (or may not) use SuperGenPass (https://chriszarate.github.io/supergenpass/). It doesn’t store anything, so there is nothing to steal. It just hashes the URL with a password that you enter each time you use it.
I’m curious to hear your opinions on the security of this approach. (My friend has not had a password compromised in 10+ years of using this tool. Is that just due to the obscurity of this approach? )
You could always use a Mooltipass…