There were some that doubted the day would ever come, but we’re happy to report that the ambitious self-destructing USB drive that security researcher [Walker] has been working on for the last 6+ months has finally stopped working. Which in this case, is a good thing.
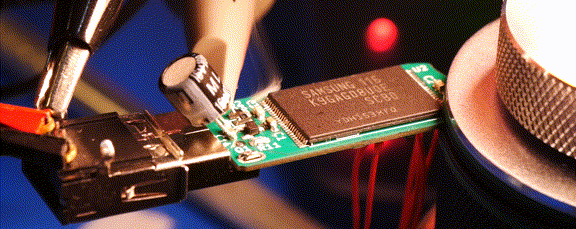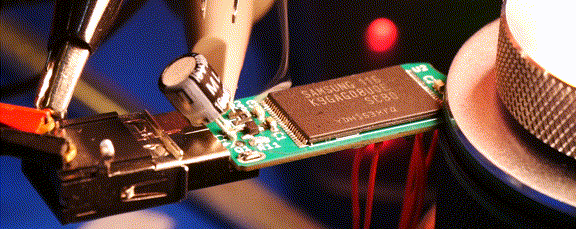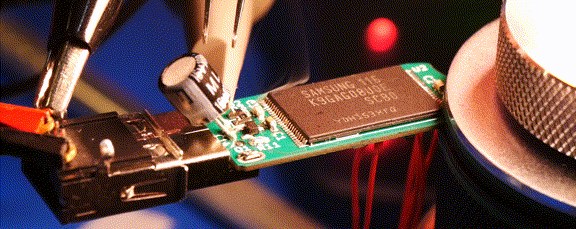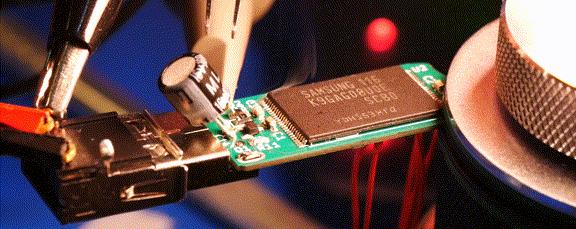
Readers may recall that the goal of the Ovrdrive project was to create a standard-looking flash drive that didn’t just hide or erase its contents when accessed by an unauthorized user, but actively damaged itself to try and prevent any forensic recovery of the data in question. To achieve this, [Walker] built a voltage doubler circuit into the drive that produces 10 volts from the nominal 5 VDC coming from the USB port. At the command of an onboard microcontroller, that 10 V is connected to the circuit’s 3.3 V rail to set off the fireworks.
Early attempts only corrupted some of the data, so [Walker] added some more capacitance to the circuit to build up more of a charge. With the revised circuit the USB controller IC visibly popped, but even after it was replaced, the NAND flash was still unresponsive. Sounds pretty dead to us.
Unfortunately, there’s still at least one issue that’s holding back the design. As we mentioned previously, [Walker] was having trouble getting the computer to actually acknowledge his homebrew drive had any free space available. It turns out that the SM3257EN USB controller IC he’s using needs to be initialized by some poorly documented Windows XP software, which might not be such a big deal if the goal was just to build one of them, but could obviously be a hindrance when going into production.
He hopes further reverse engineering will allow him to determine which commands the XP software is giving to the IC so that he can duplicate them in a less ancient environment. Sounds like a job for Wireshark to us — with any luck he should be able to capture the commands being sent to the hardware and replay them.
While we can understand some readers may have lingering doubts about the drive’s spit-detection authentication system, it’s clear [Walker] has made some incredible progress here. This project demonstrates that not only can an individual spin up their own sold state storage, but that should they ever need to, they can also destroy it in an instant.















How about looping some kanthal wire over the flash chip and just physically burning it? Once the wire melts through the casing and starts to carbonize the plastic, it should be very difficult to operate the chip any longer.
It would take a lot of power to heat a strand of kanthal wire enough to get the package hot enough to smoke. Due to the anti flame additives in the encapsulation it wouldn’t stay lit very long unless the wire was kept hot for quite a while, if you could even get it to do so.
Putting excessive voltage onto Vcc is a far more power efficient way to destroy a semiconductor.
Doing it to JTAG pins is pretty effective too…
I have a dead TI CC2538SF53 and an Olimex XDS100v3 clone because a +24V rail accidentally brushed against the pins of the FPGA (Actel ProASIC3) on said XDS100v3 while it was connected to said CC2538.
So I can say for certainty these pins are not +24V tolerant… who knew? :-)
Ever seen those FPGA boards with Arduino headers?
Arduino, the standard that includes a +5V power line. On an FPGA that’s rated for 3.3V maximum.
All this effort to design, when all I did was plug in an LCD that put 5V on the data lines.
Well, you have 5 Volts and up to 500 mA available on most USB sockets. Since you have a second micro-controller between your flash chip and the USB socket, it can turn on the heater to kill the flash chip and remain on for as long as necessary.
The point isn’t getting it to smoke – the user would notice – the point is to heat the flash chip to the point of breaking it.
considering the chip is guaranteed to survive reflow cycles, it needs to be really hot to reliably break it, which is going to take a while with only 2.5W available. the housing needs to survive this, without the user noticing.
No, but a small blob of thermite on the package might help!
If the tracks were made from magnesium and it had a large ground plane that stuff burns quite well with 5W through it.
I doubt it, since the chip is passivated. the carbon would only short the pins, and would be easy to remove, with nothing more sophisticated than a hobby knife
Or if we’re going into the thermomechanical realm: a burnthrough wire restraining a spring-loaded copper contactor that when released will drop over all the non-ground the NAND contacts and short them together. Use the impact of the contactor to smack a piezo crystal – like those used in spark-gap lighters – with the end result being a high voltage pulse being applied to every contact through to ground. For extra pizzaz, use a strong enough spring that releasing it will also physically snap the board, and possibly even add a little carbine spike to snap the NAND die too. Electronically burning and salting the earth.
something like a electronic cigarette lighter kind of situation up in there you mean
Interesting. However, you’d have to make sure that the pen drive looks like an ordinary pen drive. If this goes to market, then it will be easy to spot, and if you see one in the while, you’ll know that 1) it probably contains some sensitive data and 2) crack the case open, cut one leg (or both) of the big cap that looks out of place, and you’re golden.
What I’m trying to say is that although it is a nice idea, it needs to be more difficult to spot (the big case needed to host the cap is going to be a giveaway that) and circumvent. Ideally you’ll want to put it in an ordinary Sandisk or Kingston case, which would be great for a personal one off, but probably a big no for a commercial product. But if you could, then by the time the thief/finder realises that the data is more valuable than the drive, it’d be too late.
It would be stupidly easy to produce it with various generic plastic shells that look like other brands.
This was merely a proof of concept. Stop presuming this is the finished product.
> He hopes further reverse engineering will allow him to determine which commands the XP software is giving to the IC so that he can duplicate them in a less ancient environment.
Use Facedancer ? ( https://github.com/greatscottgadgets/Facedancer )
I just doubt if it’s actually destroying the data. How do you know the 10v isn’t just blowing some internal fuse that can (with great difficulty) be repaired and the data copied off? I’d at least do a chip erase and then send the 10v.
I have not looked at it, but I just automatically assumed it was -10V that was applied, which usually does far more damage to chips.
But chips usually have reverse diodes in the pins that prevent that…
On IO, sometimes. On VCC, never seen that. Every time we had negative voltage on VCC we could replace the chips afterwards.
Likewise. So far, all chips which I have dealt with on a troubleshooting level which experienced an overvoltage, especially a negative voltage condition via the VCC have been irreparably fried.
Yeah I’m betting it’s burning the thinnest trace somewhere and leaving the majority of the chip unscathed. Reading that would be hard… but not beyond the most determined forensic specialist. I wonder if it would be better just to have it write random data over it if the self-destruct protocol trips.
Not instantly. Before the trace pops voltage would make it into the chip. It’s not like a fuse that’s designed to prevent too much voltage from passing through before it melts, it’s just a Trace. Also is it a trace? I would think that the part of the device that delivers all that voltage would have a wire going directly to the chip.
Not necessarily, many chips could have fuses or other protection. Itikely would need to be special silicon specifically engineered for security. Determined forensics could file the thing down, etc. If it literally catches fire it would be a firehazard as well. It seems like a brute force attempt.
Perfect update for the next Get Smart secret mission. ” Agent 86.. should you accept this mission.. this pen drive will self destruct in 5……..maybe 6 seconds.. good luck” 😃. Great addition to your shoe phone and the Cone of Silence. 😂
Whats stopping someone from taking the nand chip off?
10 Volts? …… Maybe 10,000 Volts would work better?
I’m not sure you’re qualified to even be here if you think it would take 10,000 volts to properly fry a flash drive.
I was thinking of the dramatic effect. Charge up a few large capacitors on the PCB whilst we’re at it. BTW, it’s not a production idea IMO, it’s just a fun DIY thing.
That’s why ESD is so damaging as the voltages can be extremely high, even though the current is miniscule, it still fries the chip. You can do a SEM of the traces inside the chip and they look like a volcano erupted in the middle of the trace.
240V seems quite effective.
https://www.youtube.com/watch?v=Gg0sdeAwN5A
I had a job at a place which provided secure communication equipment to various government operations in the late 1970s / early 1980s. If a situation of potential physical compromise was about to occur, the ROMs and sensitive ASICs of the equipment were to be destroyed. It was a manual operation and the tool was a Waring blender equipped with a standard steel mixing chamber. I was told a few seconds in the running blender was sufficient to achieve the objective of rendering the parts useless.
10kV could also arc out like 10mm, so that could cause potential harm to other things, including humans.
arent there any UV erasable flash storage? like those eproms with a window. UV LED on top of chip, fired when unauthorized access.
These are EPROM chips, usually rather small, and it takes rather more than a second to wipe them.
Nest step: explosives!
Actually a tiny shaped charge over the memory chip(s) would work great. Encase the whole thing in epoxy and carbon fiber, so when it blows, the only thing that gets destroyed is data.
Or just make a RAM based storage with its own power supply that would get disrupted as soon as someone attempts to tinker with it. That’s how such things are done.
Or just use a tiny explosive to pop open a teflon bag of fluoroantimonic acid over the memory chip.
Or just use a tiny hot resistor to pop it
We have a winner! This is how Xilinx FPGAs store bitstream decryption keys for certain secure applications. The key is stored in a little RAM. When a tamper event is detected, the FPGA can erase the key and then erase most of the current configuration.
If the storage was encrypted the ram would only need to store the key, ram that small could be kept alive for months with a battery.
I’m wondering if he can’t put it in package with USB C plug. if unauthorized access, communicate that it needs 20V to operate and run that into a chip?
How about dumb USB C ports? That only supply 5v, and can’t negotiate higher voltages. Those might defeat the purpose of these devices.
The SM3257EN can read its configuration from the NAND flash or an external SPI Flash chip. The protocol for writing it is not documented, and from what I can tell, isn’t trivial.
As others have stated this is only really effective if the target has no idea how it works. Any foreknowledge of it being self destructive will be trivial to circumvent, so you’re really just back to good ol’ security through obscurity.
I really have to ask though, what problem are we solving here? There’s a whole host of software (and hardware!) encryption methods that are far more secure and reliable then relying on a capacitor to make things go pop. In the typical use case when everything goes as planned the end result is identical: unreadable data. Barring an extremely weak password, it’s also impossible to bypass for the foreseeable future even if you know exactly how it’s encrypted.
Ultimately, this is totally fine as a hobbyist project just for fun. But since production was brought up in the article, it’s worth noting that if this was in production it would be worse than useless. The only way it can be made effective is by adding a whole slew of anti-tamper measures which will require always on power to function reliably, and even then it’s still only as effective as the tools available to the person that wants to read it.
There are a number of documents and defcon videos available pointing out the blatant flaws of most disc and ssd encryption techniques. Some use a fixed key, others are fake epoxy, some you just unplug and move with power on and there is no standard that is upheld so one manufacturer running OPAL might be OK whilst another may not.
How about a hidden micro-switch under a flexible covering. The real user squeezes the drive to click the switch off so the drive works and then when done removes the drive and squeezes to click the switch on. In the on position the unsuspecting thief sticks it in a port and the circuit fries the drive.
You could take advantage of the USB connector design: have PCB with connector traces on both sides, but one of them will connect 5V and GND wrong way around. Good luck plugging it right way around every time yourself either though ;)
Nice. but one thing I don’t understand is why pump 10V into the supply voltage rail? Apparently it works but it will be hard to predict which chip lets out the smoke first, and a blown, but a shorted IC (even if it’s just a voltage regulator) can short circuit and thus protect the rest, and some of these devices may be repairable.
If you directly put the 10V to for example the chip enable or the read pin of the memory IC, then you can be quite certain the memory IC will get damaged.
The way to do it: Make the memory chip socketable and gulp it down.
Note: Always have a glass of milk at hand and get a lavage within the next two hours ;)
How about an old disposable camera flash capacitor? That would toss enough juice into it. I’m just not trusting the 10 volts.
I made this take on the seemingly unsolvable problem of keys a while ago, emplying a Raspberry Pi zero:
https://hackaday.io/project/185266/files
To avoid the rather high threshold of producing high speed electronics, using a Pi might lower the gate for experimenting.
As a friend, not one for higher studies, once put it: “Well in the end, somewhere you have to store the key, whether it is a code or an actual key.”
To add to this the code required for a safe storage is rather long, pin-codes or biometrics often just make the device itself into swiss cheese security.
The general idea was to let the users themselves release their human ingenuity to invent a storage method for the full AES(or similar) key: paint a picture (correct horse battery staple…) solder some resistors in an amp to represent the code, have it scribbled on a gum to eat it when you hear the black helicopter and so on. It does not handle evil maid.
So far the only comment I got was that my solution ‘was safe since AES cannot be cracked’. Bit unimaginative one would think..
Did this 10 years ago for the silk road (my inferno drive)…
Equal parts thermite, powdered magnesium and clear nail polish (layered not mixed)
Dab of that on the center of the NAND with a model rocket ignitor (or tiny bit of 28awg nichrome) rigged to a submini, N.O. momentary switch and the power rails (or a 123 12v battery) works every time…we added the battery after frying too many USB host controllers.
where do i get one?