There were some that doubted the day would ever come, but we’re happy to report that the ambitious self-destructing USB drive that security researcher [Walker] has been working on for the last 6+ months has finally stopped working. Which in this case, is a good thing.
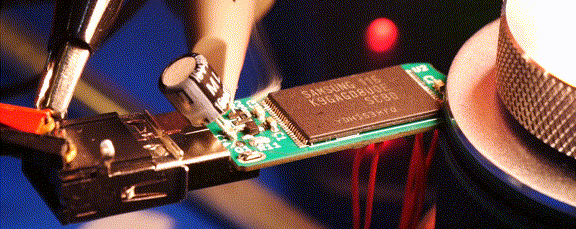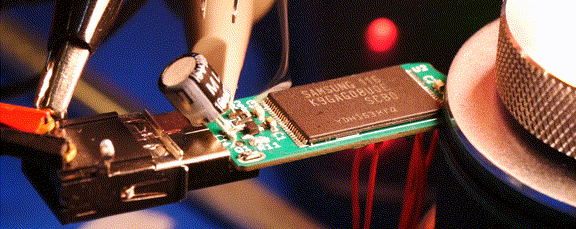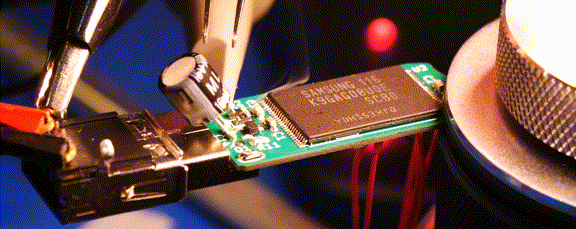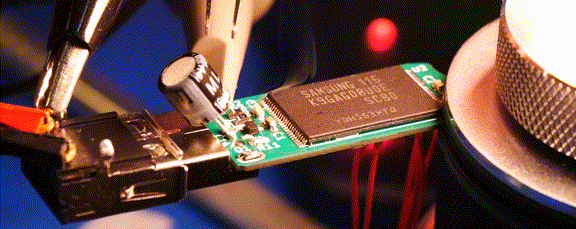
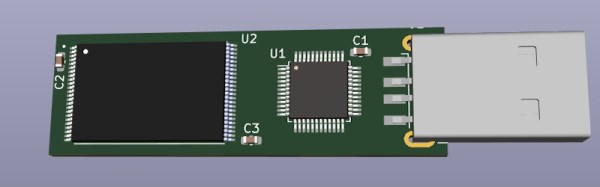
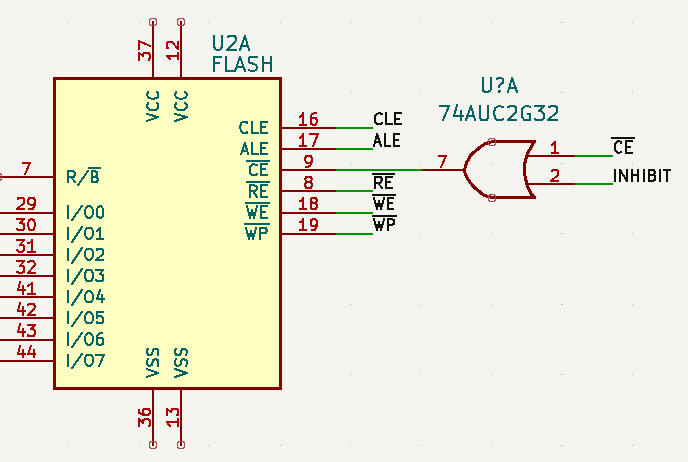
Readers may recall that the goal of the Ovrdrive project was to create a standard-looking flash drive that didn’t just hide or erase its contents when accessed by an unauthorized user, but actively damaged itself to try and prevent any forensic recovery of the data in question. To achieve this, [Walker] built a voltage doubler circuit into the drive that produces 10 volts from the nominal 5 VDC coming from the USB port. At the command of an onboard microcontroller, that 10 V is connected to the circuit’s 3.3 V rail to set off the fireworks.
Early attempts only corrupted some of the data, so [Walker] added some more capacitance to the circuit to build up more of a charge. With the revised circuit the USB controller IC visibly popped, but even after it was replaced, the NAND flash was still unresponsive. Sounds pretty dead to us.
Unfortunately, there’s still at least one issue that’s holding back the design. As we mentioned previously, [Walker] was having trouble getting the computer to actually acknowledge his homebrew drive had any free space available. It turns out that the SM3257EN USB controller IC he’s using needs to be initialized by some poorly documented Windows XP software, which might not be such a big deal if the goal was just to build one of them, but could obviously be a hindrance when going into production.
He hopes further reverse engineering will allow him to determine which commands the XP software is giving to the IC so that he can duplicate them in a less ancient environment. Sounds like a job for Wireshark to us — with any luck he should be able to capture the commands being sent to the hardware and replay them.
While we can understand some readers may have lingering doubts about the drive’s spit-detection authentication system, it’s clear [Walker] has made some incredible progress here. This project demonstrates that not only can an individual spin up their own sold state storage, but that should they ever need to, they can also destroy it in an instant.