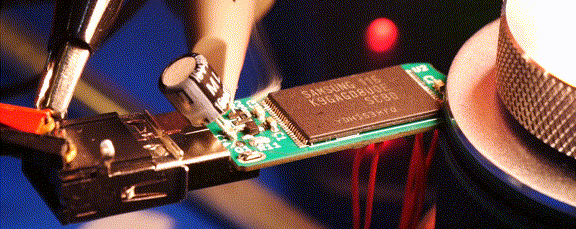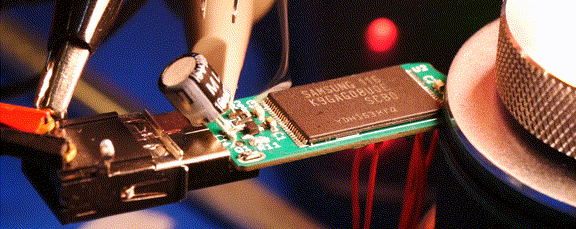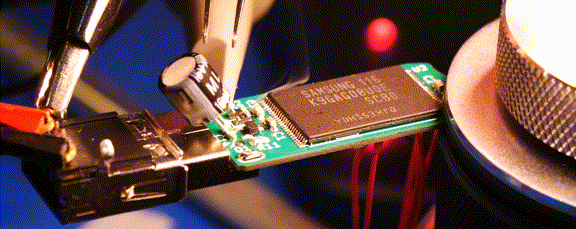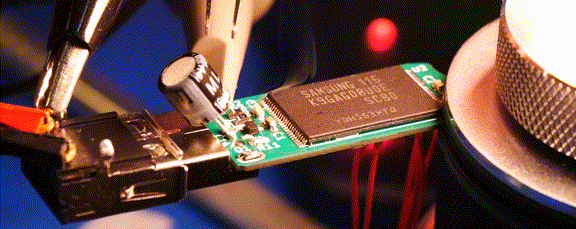
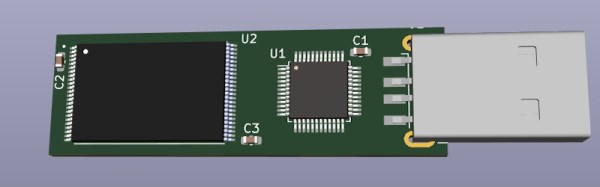
For almost a year now, we’ve been following the progress [Walker] has been making with Ovrdrive — a completely open source USB flash drive that features the ability to destroy itself should it fall into the wrong hands. It’s an interesting enough project on those merits alone, but what really made this idea stand out was that the user was expected to lick their fingers before handling the drive as a form of covert authentication.
Well, we’ve got some good news and some bad news. The good news is that [Walker] is just about ready to release the Ovrdrive officially on Crowd Supply. But it’s with a heavy heart that we must report that the device’s cutting edge spit-detection capabilities have been removed. Now if you want to preserve the drive’s files, you need to rapidly insert and remove the drive several times rather than just plugging it in.
 In all seriousness, this new approach makes a lot more sense. As entertaining as it might have been, the whole idea of a device that could detect moisture on the user’s fingers was fraught with problems. It was a bit more of a meme than a real solution, and if we’re being honest, kind of disgusting. This new approach sounds far more reliable, especially when combined with the new “Lite” self-destruct mode.
In all seriousness, this new approach makes a lot more sense. As entertaining as it might have been, the whole idea of a device that could detect moisture on the user’s fingers was fraught with problems. It was a bit more of a meme than a real solution, and if we’re being honest, kind of disgusting. This new approach sounds far more reliable, especially when combined with the new “Lite” self-destruct mode.
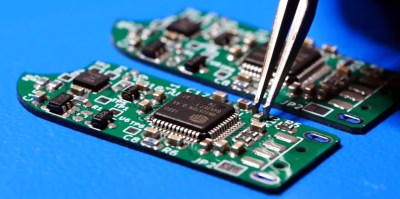
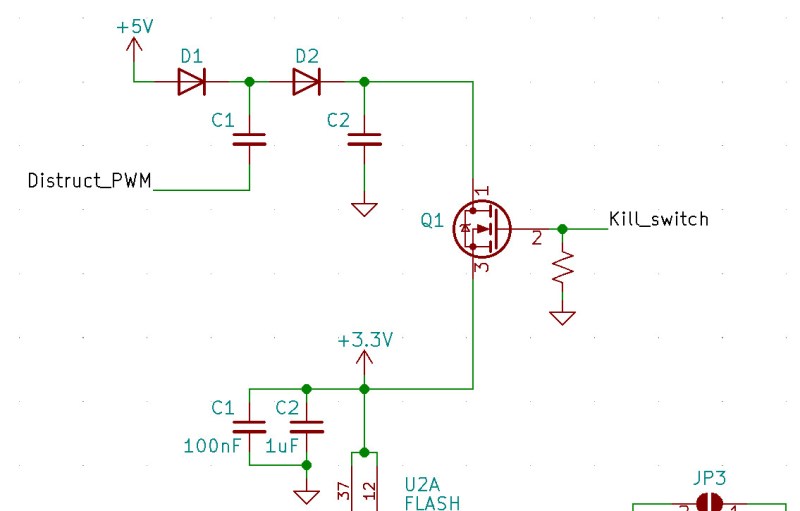
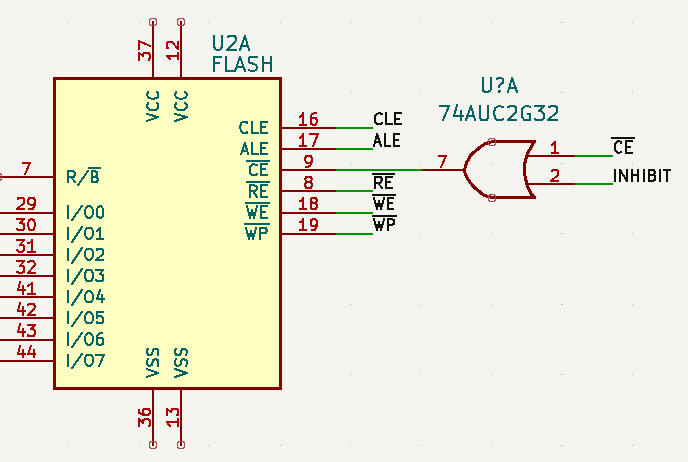
While the original capability of literally frying the flash chip by way of several capacitors and a voltage doubler is still here, there’s also a non-destructive approach that’s enabled by default. Unless you open up the drive and desolder the jumper pad on the PCB, the onboard ATtiny24A will simply use the enable pin on the flash chip to make it appear empty. This means that you’ve got to really want to cook your flash chip on the first hint of funny business.
Ultimately, whether it’s self-destructing or not, we just really like the idea of a hacker-developed open source hardware USB flash drive. Admittedly it would be a lot cheaper and more practical to just buy one like a normal person, but we strongly believe that if there’s a way for the community to build a OSHW version of something, they should at least give it a shot.
Continue reading “Updated OSHW Flash Drive Keeps Data Safe, Fingers Dry”