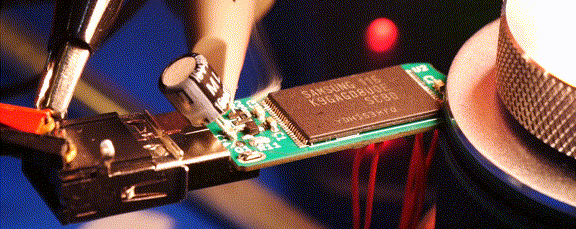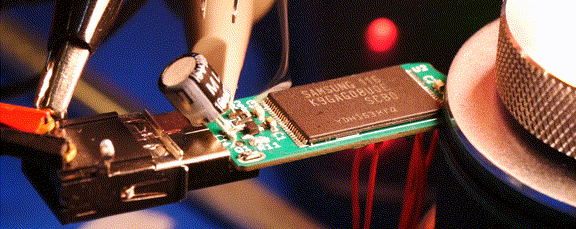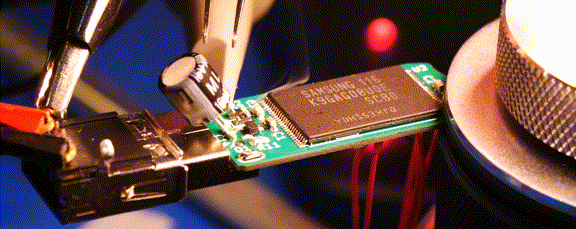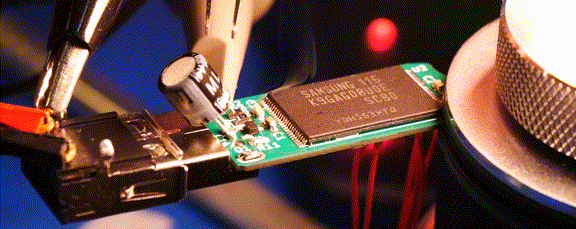
Every year, USB flash drives get cheaper and hold more data. Unfortunately, they don’t always get faster. The reality is, many USB 3.0 flash drives aren’t noticeably faster than their USB 2.0 cousins, as [Chase Fournier] found with the ultra-cheap specimens purchased over at his local Micro Center store.
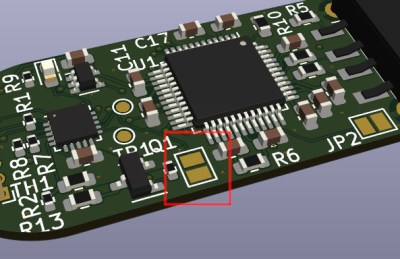
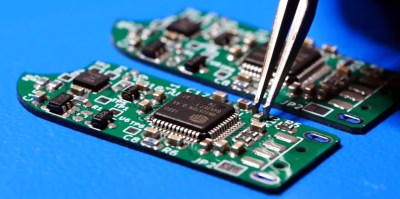
Although these all have USB 3.0 interfaces, they transfer at less than 30 MB/s, but why exactly? After popping open a few of these drives the answer appears to be that they use the old-style Phison controller (PS2251-09-V) and NAND flash packages that you’d expect to find in a USB 2.0 drive.
Across the 32, 64, and 256 GB variants the same Phison controller is used, but the PCB has provisions for both twin TSOP packages or one BGA package. The latter package turned out to be identical to those found in the iPhone 8. Also interesting was that the two 256 GB drives [Chase] bought had different Phison chips, as in one being BGA and the other QFP. Meanwhile some flash drives use eMMC chips, which are significantly faster, as demonstrated in the video.
It would seem that you really do get what you pay for, with $3 “USB 3.0” flash drives providing the advertised storage, but you really need to budget in the extra time that you’ll be waiting for transfers.
Continue reading “Why Are Micro Center Flash Drives So Slow?”