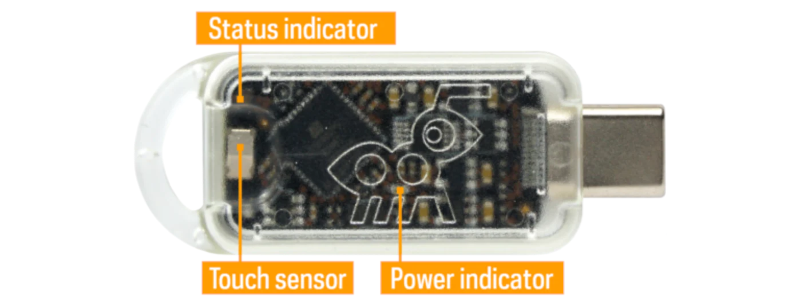
The TKey is a RISC-V-based security key that plugs into a USB port. The device has a number of features, including a device-specific serial number, RAM scrambling, and a monitor that kills the CPU in the event of access to protected memory. There is also an FPGA that, on the end-user version, is locked down. This prevents you from changing the core features and the unique ID number for the device.
As part of the start-up code, the device calculates a hash of the application and merges it with the device ID and, potentially, a user-defined secret. If this number matches a previous calculation, it is reasonably certain that nothing has changed between the times of the calculations.
Don’t trust the developers? Make your own key since it is all on GitHub. If nothing else, having everything out for review means that any glaring problems will be open for scrutiny by the community.
Of course, you can just buy the device for about $70, and that’s probably what most people will do. We will leave it to the experts to tell us if it is better or worse than commercial offerings out there today.
A key like this can be one factor in a multi-factor authentication system. It isn’t like these hardware tokens don’t already exist, but they never seem to be widely adopted.















It’ll be a good comparison to see how it holds up with Nitrokey 3c.
Even that’s open source with schematics & application, plus it’s similar cost with nfc.
The difference would boil down to this having fpga & rics v while the other has nfc & runs using Google’s rust based 2FA rtos (which udk if this does as well)
https://duckduckgo.com/?t=ftsa&q=Google%E2%80%99s+rust+based+2FA+rtos yields much 2FA but no RTOS
I can take a guess that the reason for the lack of widespread uptake for hardware tokens is twofold: a) the trainwreck that was / is getting SecureCARD and Windows AD to play nicely; and b) the death-grip that RSA had on hardware tokens in it’s infancy, and it’s expense to maintain.
I got a sandbox lab implementation of SecureCARD set up at one point back in 2019 using the YubiKey fobs and it worked pretty well, at least until the CIO found out what I was up to in the lab- his reaction was as if I had brought in a live rattlesnake into the office and nixed it immediately. :(
At [RedactedCo], we had the hardware tokens and hardware appliances for a long time, and support was pretty expensive, AND you had to pay something like $1000 USD for twenty hardware fobs every few years when they ran dead.
I wondered what happened when they ran out of juice. That’s interesting to hear.
Correct is that Nitrokey doesn’t run any Google RTOS but its own firmware developed in Rust and with the Trussed framework.
Saw YT clip the other day outlining how newer guided missiles run on FPGAs with a dynamically loaded core. The idea is that when the battery depletes or tampering is detected the FPGAs wipe. Interesting concept though could be problematic.
This tape will self destruct in five seconds…