One of the simplest ways of keeping a computer system secure is by using an air gap — that is, never actually connecting the system to the network. This can often include other peripherals like USB drives and other removable storage as well, so getting information to and from secure (or compromised) systems behind air gaps can often present a challenge. But assuming you have local access to the computer and your parts bin handy, these optical solutions from [Nikolay] can allow data transfer to or from such off-line computers.
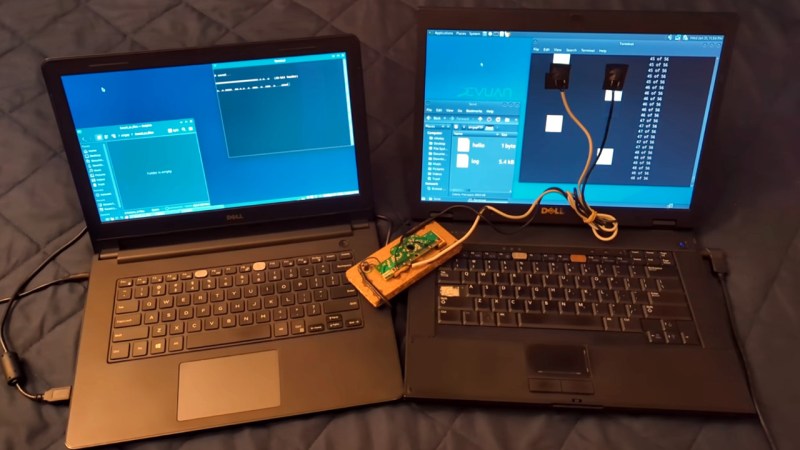
[Nikolay]’s specific use case for this project is to transfer small amounts of information to or from computers that may be compromised in some way, or computers that might otherwise be dangerous to connect to other equipment. There’s actually several methods described in the project, the first involves temporarily attaching a photoresistor to the computer’s screen which has been wired into the remains of a USB keyboard. A script running on the compromised machine translates data into a series of white and black squares. The sensors can detect these patterns much like playing Duck Hunt on an old CRT television and transmit the data across the air gap with reasonable certainty nothing harmful crossed with it.
The second is essentially a DIY optoisolator arrangement, where the audio output of the compromised computer is used to flash an LED by way of a simple transistor circuit. On the receiving side, a photoresistor connected to the audio input picks up the flashing LED as sound. The whole thing is enclosed in a black plastic box, and with the appropriate software, [Nikolay] says it can transfer 345 bytes per second between the two machines.
While the methods detailed by [Nikolay] certainly aren’t fast, they could still be extremely useful in a number of cases. He’s also set up all of the code so that it’s ready to go as soon as the diodes and transistors are soldered together. A friendly reminder to all, though, that although it’s definitely a step in the right direction an air gap isn’t an impenetrable wall of security.

















While I see some interest in the proof of concept, I don’t see a real case where this would be handy…
While you have complete access to the computer, assuming you want to keep it air gapped, it would make more sense to encode data in a video (qr code or similar) and just record it with your smartphone for later decoding. Better throughput and no special hardware needed
Or just use a speaker/mic/aux cable with a basic modulation scheme. I actually wrote an audio modem in software for my communications class back in college.
using a soundmodem is so cool and flexible!
In fact, the other 2 methods in my repo linked above show aux cord (1,111B/s) and LED with photoresistor (345B/s.) And 2 additional methods I had quit but also using headphone+mic lines: actual microphone taped to headphone face-to-face (366B/s, too sensitive to environment.) And second: tiny ferromagnetic torus wound with wires, 1 winding for mic line, 1 winding for headphone line.
The concept is usually called a “data diode”.
Useful when you have a secure system, but need to feed data into it.
Using a laser diode, and optic fibre, you can have significant isolation AND high speed. With no method of signalling a packet error, transmission protocol must be chosen with care – but optic fibre can carry data at rates over 1Gbit/sec.
If one can use a script to display patterns on the airgapped computer, one can also just get the data out on a serial port and cable only the Tx –> monitoring computer.
Or display a serie of QRcodes and use OpenCV on the other side to get the data in.
That should be much faster, no extra hardware and is as secure as the optcoupler trick
How do you get that sender program to the compromised machine?
you programm it on the maschine…
This has certainly left me with more questions than answers, but I assume the “sending” machine was at one point clean (and was able to have the script copied to it). This method is then to extract data after it has been potentially exposed.
I would have thought OCR would be a faster and easier method to achieve this however.
Yeah, camera and OCR seems like the obvious solution. Though in some high-security places all cameras are forbidden.
Bare electronics taped to a screen, though?
“No, nothing expressly forbidding that in policy…carry on!”
Yes, pretty much everywhere has electronic components in inventory, and if not it’s much easier to justify bringing in a couple passives than a DSLR or the impossible task of authorizing your cell phone.
This isn’t meant to be a commercial product that revolutionizes network security, but a cool demonstration of creative problem solving and learning about different ways to encode, transmit, and decode data with self-imposed limitations.
One time use flash drives, duh. Ever been to a trade show? They hand them out like quaaludes in a 1980s wall street office
Plausibly, you could write a script file. Frankly, it seems easier (and more covert) to simply blink the keyboard LEDs. https://doi.org/10.1109/COMPSAC.2019.00118
Why not simply use a usb to uart -> uart to usb?
Wouldn’t that be much easier and faster? The “air gab” is only needed if the voltage of the maschine is dangerous, isnt it?
Some places restrict USB connectivity by operating system policy. The “air gap” is for any danger, not just voltage, in this case they’re probably thinking of computer viruses and hackers.
So this is actually how industrial data diodes work. Except they use fibre optic transducers and only connect one fibre, such that you only have unidirectional traffic.
Well sure, but those require quite a lot of additional expensive hardware. This IS a “data diode” with an optic transducer, which requires only a couple cheap components that many people have in their parts bin.
First method is similar to how Timex Datalink watch transferred data (https://hackaday.com/2023/07/18/modern-software-brings-back-the-timex-datalink/). Blinking a light is a truly eternal data transfer method :)
That was my first thought. Plus old Palm Pilots used a IR link to “beam” data to each other.
Not just palm pilots. In the late 90s and early 2000s, many devices supported IrDA. And this was the way I often connected to the Internet when away from home. Long before “tethering” was even an idea, I would just line up the infrared ports between my Nokia 8210 and my laptop and tell both to start the connection. Doing IP over UART over infrared is was so common that it was a standard feature of consumer grade hardware, and was natively supported by windows.
… actually, come to think of it… “beaming” data between graphing calculators was pretty common before palm pilots, even in the early 90s. TI-85s had that feature, as did the HP-48 series. Made it easy to transfer programs between your fellow students in math class.
Datalink was cool because it depended on the physics of a CRT as if it were a reverse barcode scanner. Just like a light gun it depended on a phototransistor being fast enough to pick up the bright spot the beam makes as the CRT rasters over the light from the surrounding excited phosphor.
Each vertical refresh the software would display a pattern of horizontal lines that made up a serial data stream that the watch could decode as the monitor scanned through the lines sequentially. This doesn’t work on LCDs, so the tech died off quietly in the early ’00s.
Make it parallel transfer 8 blocks=8bytes
This for sure. Also can anyone explain how a non I2C optocoupler chip with much faster and accurate transfer would not be better other than not being able to see the airgap? I am not trying to be demeaning as I get it is a very niche interest but I just see many opportunities to sell audiophile like magic gear for this group ;)
With appologies for missing the point entirely, but I wish Dell still made laptops with full-sized arrow keys in a proper cross like the one on the right in the cover pic! We don’t all have svelt touch-typing fingers!
+1
+2 The 7720 had full sized arrows, but the 7730’s I’m using at work now do not… very annoying!
Isn’t this very much not air-gapped and just security through obscurity since no malware would target this method of data transport?
That said, it got me thinking about a system where you point two laptops at each other then have their cameras read each others screens with suitable pattern generator programs.
Yep. When you build a network, you don’t have an air gap any more. Just cluelessness.
aka data diode. https://en.wikipedia.org/wiki/Unidirectional_network
The novel “The Vor Game” by Lois Bujold had this trick as a plot point. There’s a high tech secured network with secured terminals that’s supposed to prevent data being smuggled out or being copied. One fellow calls friend on what’s basically a video telephone and asks him to call up something from the high security network. There’s too much to simply read out loud, so the fellow in the secured room turns his video phone to face the secured terminal so his friend can read it and see the photos.
It’s a minor incident in the story, but it pulled some laughs.
https://en.m.wikipedia.org/wiki/The_Vor_Game
I agree, I think someone took the word “air gap” too literally. Isn’t WiFi technically an “air gap”, if all we care about is the literal meaning?
I don’t recall if Ethernet uses an optocoupler. I know MIDI does.
Anyway, the point is that they’ve really just created a ln obscure network peripheral.
Would a less obscure one serve the same purpose better?
Ethernet and a router firewall for just those two devices? Or wifi enabled microcontroller emulating USB on one end? Just some ideas.
+1. What I came here to say. And no, Ethernet uses transformers to isolate, to avoid problems caused by different ground potentials across the network.
The actual meaning of “airgapped” in a security context means having no connections to the rest of the world, electrical or otherwise. This is just a concept, though; there is no such thing as perfect isolation. Requiring an airgapped computer is an acknowledgement that firewalls are not perfect.
And also, “Security through obscurity” is practically the opposite of “airgapped”, regardless of the transmission medium.
And one other thing, the optoisolators in MIDI were put there to prevent you from grounding your sensitive analog audio equipment to your noisy computer. Not sure how that works these days, with so many people using USB for MIDI.
To be fair, having one-way data transfer to get logs from a compromised machine could make sense in some cases. This is effectively a side channel ‘attack’ used to get data from an isolated system without using network or USB communication. As others have noted, a serial port could provide the same functionality far more efficieny. And let’s face it, the purpose of air gapping a system is not to eliminate all possible means of data transfer to/from it. If that were the case typing what you see on the screen of the compromised system on another machine would break the air gap, and you might as well just never power it up.
So, does everyone know that cadmium sulfide photo resistors are very slow to recover from light exposure??
https://en.wikipedia.org/wiki/Photoresistor
They are just about useless for data communications. (As pointed out, they can be slow.)
If the designer switched to a photo diode or photo transistor to detect the light, the throughput is likely to increase dramatically.
This surprised me too, like tv remotes never existed…
Gosh, a DIY optocoupler. But it requires physical access to the computer, and when you have physical access, this hack does not mean much anymore. For example, what do you think of taking the phone out of your pocket and video the monitor while hitting the pagedown key. You can easily capture quite a lot of data quickly that way.
https://hackaday.com/2013/02/25/using-a-flashing-lcd-monitor-to-transfer-data/
There’s one more very old project posted here that displays the clock and data on-screen, while you swipe the reader over the screen.
Next level: he should use my new hack to double the datarate: mix the white color with black in 66-33% ratio and in 33% 66% ratio – lets name its gray1 and gray2 -, which can be used in conjunction with black and white to store 2 bits information in the intensity level! I call it Penetrating Airgap with Modulation – 4 (PAM-4).
IRDA anyone?
https://en.wikipedia.org/wiki/Infrared_Data_Association
Damn, beat me to it. Almost every laptop used to come with one built in.
The power consumption of IRDA made it impractical for anything but a laptop (back before Li+ batteries were common!). IIRC, they required a 1A surge during transmit (or a really big capacitor, which adds cost).
Nah, my absurdly tiny cell phone had IrDA. That was the whole point to having it on the laptop, it was used for connecting to the Internet over GSM. Battery consumption on the phone was not more interesting than normal cell functions — I would often run it for hours a day, and the phone battery was only 650 mAh.
could just write the data to a cassette tape and read the tape on the receiving machine for all the difference this method provides.
From wikipedia: “The simplest form of a unidirectional network is a modified, fiber-optic network link, with send and receive transceivers removed or disconnected for one direction, and any link failure protection mechanisms disabled. Some commercial products rely on this basic design, but add other software functionality that provides applications with an interface which helps them pass data across the link.
All-optical data diodes can support very high channel capacities and are among the simplest. In 2019, Controlled Interfaces demonstrated its (now patented) one-way optical fiber link using 100G Commercial Off The Shelf transceivers in a pair of Arista network switch platforms. No specialized driver software is required.”
Wasn’t there an article or something about using incandescent overhead lights or something like that to send data? I don’t quite remember the details. There are many ways to air gap a computer. What about using ultrasonic transducers? There are many ham radio digital modes that could be used. Even high speed Morse code that’s too fast for a human to decode. Now with AI, computers can decode just about anything.
I did see a story where AI decoded a language in seconds that humans couldn’t. If you can turn something on and off, no matter how slow or fast, you can send a message. Blink your eyes, twitch a muscle, you can do anything to transfer data. While you may not be able to transfer huge games or large jpg files, for some text messages it’s good. A mad programmer back in the 1980’s wrote a program that would allow 7 300 baud modems inside an Apple //e to pass data between them. Whatever was typed on one modem would be repeated on all 7. You can see an example of this on http://www.ddial.com or magviz.ca a 21st century recreation of the chat system that started it all. For its time, it was fantastically advanced, but it paved the way for the internet we know today. almost 50 years later, I’m still chatting with people I knew back in the 80’s.
300 baud wasn’t fast, but for most with a Commodore 64 it didn’t have to be.
Blinking the overhead lights was a way to program price tags in supermarkets. Not sure if it ever got implemented anywhere.
You can do this better by blinking the keyboard lights. Use one LED as the clock & the other two as data bits.
I’m gonna put this out there, not because I don’t think this hack isn’t cool, but because it’s was superceded by existing technology before it was even thought of.
Use an external optical drive (or internal if it already has one) and session finalized CD-Rs/DVD-R. The compromised machine doesn’t even need to create a local copy of the contents just reads the program from the disk. Pretty sure this is the entire point of live disks for data recovery of damaged/compromised machines.