Whether it’s a game of D&D or encrypting top-secret information, a wide array of methods are available for generating the needed random numbers with high enough entropy for their use case. For a tabletop game this might be a single die but for more sensitive applications a more robust method of generating random numbers is needed. Programmers might reach for a rand() function of some sort, but these pseudorandom numbers don’t cut the mustard for encryption. For that you’ll need a true random number generator (RNG), and this open-source hardware RNG uses one of the better methods we’ve seen.
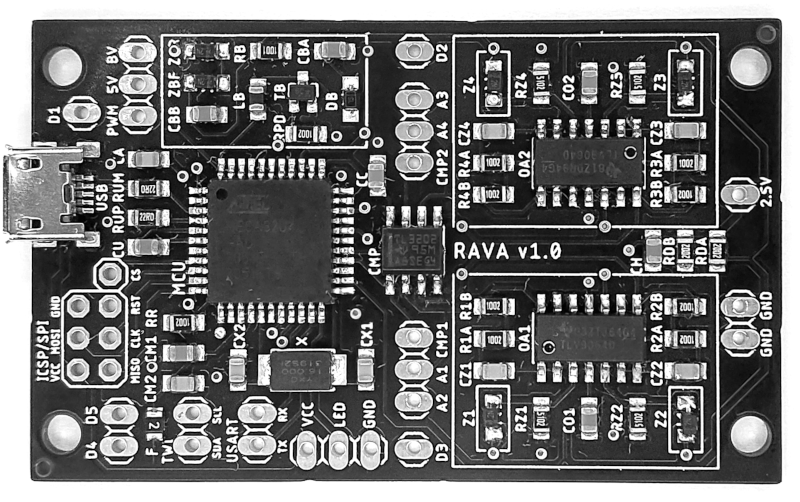
The device, called RAVA, is based on a property found in many electronic devices called avalanche breakdown. Avalanche breakdown occurs when a high voltage (in this case approximately 25V) is applied in the reverse bias direction, with this device using a pair of Zener diodes. When this high voltage is applied, an “avalanche” of electrons occurs which allows the diodes conduct in the opposite direction that they would when they are forward biased. This isn’t a constant current flow, though; there are slight variations over time which can be amplified and used as the random number generator. The noise is amplified over a series of op amps and then fed to an ATmega32U4 microcontroller which can provide the user with 136.0 Kbit/s of random data.
Unlike other random number generators, this device is based on a method generally accepted to be truly random. Not only that, but since it’s based on discrete hardware it can be accessed directly for monitoring and replacement in case of faults, unlike other methods which are more “black boxes” and are more opaque in their processes which are thus harder to audit. We also appreciate it’s open-source nature as well, and for some more information on it be sure to check out the paper on it in IEEE. If you’re looking for something to generate random numbers but will also bring some extra flair to the next game night, take a look at this radioactive dice replacement.















@Bryan Cockfield said: “Whether it’s a game of D&D or encrypting top-secret information, a wide array of methods are available for generating the needed random numbers with high enough entropy for their use case. For a tabletop game this might be a single die but for more sensitive applications a more robust method of generating random numbers is needed. Programmers might reach for a rand() function of some sort, but these pseudorandom numbers don’t cut the mustard for encryption. For that you’ll need a true random number generator (RNG)…”
A reliable pedant said: “RAVA is a True Random Number Generator (TRNG) – not an RNG.”
this looks well designed, health checks and all, but no results on the diehard tests? :(
I could be wrong, it has been a while since I last looked at diehard tests, I think that you need about 1GiB to 10GiB of random goodness for a full set of tests. At 136.0 Kbit/s that would take about 749 days to around 21 years for one RAVA device to generate.
I get wildly different numbers to you. 1Gigabyte is 8.59 Million kilobits. At 136kilobits per second that takes 63162 seconds. So 1GiB of random data from this device takes less than 18 hours, but 10GiB takes just over a week.
You are totally right I must have multiplied by an extra 1024 and screwed up my calculations.
For 1 GiB I get approximately 17.5 hours, so for 10 GIB that would be about 7.3 days.
Hardware randomness rules. The deep dive i did on PRNGs ultimately made me more interested in circuits and other novel approsches to true random. However the cyclic nature of PRNG is rather appealing, I see the chain of a state space as something like a musical part.
One advantage to PRNG is that you can rerun a deterministic program with the same seed it’ll generate the same sequence of random numbers.
This is an advantage in, for example, debugging where you want to reproduce the sequence of events exactly.
Also games where the level or puzzle is generated. the game/map/level number is just a seed
no need to go to a separate board – you can use a esp32 to generate real random numbers (based on the noise of the WiFi / Bluetooth RF subsystem – so genuinely random) that would be goo enough for any use I can think of..
I have one permanently set up that spits random bytes up the usb when I plug it in, in 0x format that I can use in anything.. Great for password creation…
I don’t know if it matters practically, but this is “even more random” than that. Avalanche noise if captured correctly is a quantum effect. 100% unpredictable.
It’s hard to test for randomness, but the esp32 one went through quite a few of the available tests, and was the subject of a number of papers.. I can’t see why anyone would need more random than that – ie it was certainly beyond what almost anyone would need for either simulation or encryption..
Yeah for anyone who is nervous, just in case there is some unseen bias in the raw hardware bits you can pass it through a hash function.
The Intel RNG is like that. The hardware portion itself is non-random in that the gambler’s fallacy isn’t a fallacy for those bits. But Intel then hashes it (sha256?) before the bits reach a user-visible register.
ie it past the NIST tests.
There’s also the open source ‘Infinite noise’ TRNG.
https://github.com/waywardgeek/infnoise
Not a dead project. You can still buy them on crowdsupply and there’s linux drivers.
I think it’s a poor design.
Everything depends on the quality of USB power provided by host.
And if You ever delt with it You know it’s a crap and will vary a lot.
And everything in the design will vary (can be modulated by changing 5V from USB host).
2.5 Vref will change (TL431 could fix it), “high voltage” BV will change. This is far from random.
Yeah, and probably could be affected from far away using high power RF source. Of course this is irrelevant for the hobbyist purposes this is meant for, but for those PC built-in randomness sources are good enough.
That’s why a differential design is used: the avalanche noise from two similar Zener diodes is compared (subtracted) to generate random pulses. This ensures that any variations in the circuit affect both channels equally. Studies have shown that this design also mitigates electromagnetic noise; see Section IV.B of the IEEE publication for details.
Indeed, I think V5 would be better to have an LDO on it to knock it down to, say, 4.5V.
Also the bias voltage for the zeners has a massive decoupling (Cbb) – feeding the zeners themselves. This probably reduces the bandwidth of the noise significantly. Better off adding some inductors in series, to increase the noise frequency distribution, then you can get more bits per second out of it.
Thanks for the helpful comments. Regarding the bandwidth, I’d like to understand how the circuit would look after your proposed changes. Do you mean removing Cbb or keeping it? Also, where should the inductors be placed, and what values do you recommend? Currently, the CMPs operate at ~3 MHz. With your suggestion, can this be improved?
So.. use a separate, stable power supply and put the whole thing in a grounded metal case.
Very nice I still have my truerng V2 somewhere but randomness is much more available these days.
The easiest true RNG I ever built was a webcam and a smoke detectors ionisation source. It seemed to work nicely for several years before I ditched it. It’s supply was fairly limited and could be patchy(only emitted when it was certain there was multiple events).
I am sure it’s been featured in had before.
I’ve built something quite similar, using an MC34063 to boost the USB voltage to ~15V for 12V zeners. I used 16 of them and 8 comparators, so the µC can fetch a whole byte at once and spit it out via RS232-to-USB. It manages around 70 kB/s at 921600 baud (that’s kilobytes, not kilobit).
Similar approach: http://jtxp.org/tech/xr232web.htm
You could use a bit of radioactive material to generate random numbers
Get an old smoke detector and a Geiger tube, or solar panel, and use the radioactive source as a way to generate random noise, which would be a seed for a random number generator
Use like 128bits and get a really large and random number
Then Use that as a seed for a keypair
I’ve seen documentation that Avalanche break down has been used as a noise source for wideband RF jamming.
Random number generator output should be tested to see if tests passed?
NSA cryptographer Brian Snow described a hardware crypto device failure releasing plain text, in a lecture in ~1983 to some of us at Sandia labs.
What aare the advantages of usig pseudoradom numbers over a
hardware reandom number generator?
AI Overview
Pseudorandom number generators (PRNGs) offer several advantages over
hardware random number generators (HRNGs), including speed, reproducibility,
and ease of implementation. PRNGs are deterministic, meaning they generate a
sequence based on a starting value (seed), allowing for the same sequence to be
reproduced consistently. This is beneficial for simulations, debugging, and scenarios
where predictable sequences are required. While HRNGs provide truly random
numbers, they can be slower and more resource-intensive to implement.
Here’s a more detailed breakdown:
Hello.
Are there any alternatives with higher data rates?
Gabriel Guerrer comes from the field of “consciousness research” in physics.
This is a “reframing” for the “gritty” psychokinesis research.
For experiments with individuals, 1 to 200 bits/s (Dr. Helmut Schmidt, PEAR [Princeton]) is sufficient, with a maximum of perhaps 1000 bits/s (Schmidt).
But if you want to offer it as a self-test on a website, as the University of Amsterdam etc. did in the past, you need a higher data rate for many simultaneous accesses.
Or for a livestream scenario on Twitch, TikTok, YouTube, where viewers focus on a common goal.
That’s hundreds, possibly thousands, tens of thousands, hundreds of thousands…
If you focus the influence of so many people on just 136 kbit/s, the deviation could of course be very high.
But higher data rates mean higher accumulation, and that can increase the probability (p-value…).
In addition, such live streams with many participating viewers offer further possibilities.
For example, images, moving images, and audio from white noise.