The old saying that the best way to learn is by doing holds as true for penetration testing as for anything else, which is why intentionally vulnerable systems like the Damn Vulnerable Web Application are so useful. Until now, however, there hasn’t been a practice system for penetration testing with drones.
The Damn Vulnerable Drone (DVD, a slightly confusing acronym) simulates a drone which flies in a virtual environment under the command of of an Ardupilot flight controller. A companion computer on the drone gives directions to the flight controller and communicates with a simulated ground station over its own WiFi network using the Mavlink protocol. The companion computer, in addition to running WiFi, also streams video to the ground station, sends telemetry information, and manages autonomous navigation, all of which means that the penetration tester has a broad yet realistic attack surface.
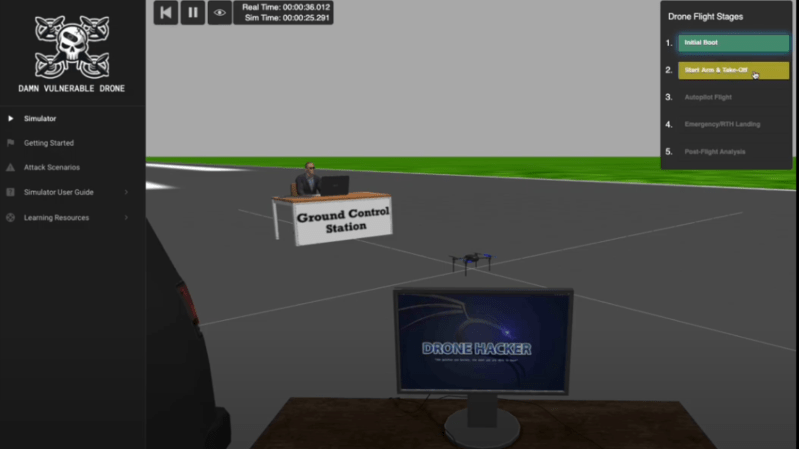
The Damn Vulnerable Drone uses Docker for virtualization. The drone’s virtual environment relies on the Gazebo robotics simulation software, which provides a full 3D environment complete with a physics engine, but does make the system requirements fairly hefty. The system can simulate a full flight routine, from motor startup through a full flight, all the way to post-flight data analysis. The video below shows one such flight, without any interference by an attacker. The DVD currently provides 39 different hacking exercises categorized by type, from reconnaissance to firmware attacks. Each exercise has a detailed guide and walk-through available (hidden by default, so as not to spoil the challenge).
This seems to be the first educational tool for drone hacking we’ve seen, but we have seen several vulnerabilities found in drones. Of course, it goes both ways, and we’ve also seen drones used as flying security attack platforms.















I would like to bring to attention that Ardupilot, the beloved quadcopter/boat software is being used in actual warfare as we speak.
Its truly a shame, something made for enjoyment of students and hobbyists alike is now in the hands of soldiers and state actors, being used for violence
most FPV drones that are being used in various conflicts around the world are still using the same open source software that hobbyists have been using for years.
Most of them are literally just an FPV that’s on the bigger side (like 8-10 inch props), with some redneck engineered system to hold a 1kg explosive, that is detonated by two pieces of metal usually in the form of a straight pole and a coil surrounding it designed so when the drone impacts something it would cause the metal wires to touch and complete the circuit.
This is something that anyone with a soldering station and basic knowledge of building and programming FPVs can make for only around $200-$400.
Most software used in these are no different. it’s gonna be controlled using a controller running EdgeTX, it’s probably going to be programmed using software like Betaflight, etc. This doesn’t mean that all of these amazing OSS projects are designed to be used for war or that the maintainers support war.
Shame is that violence, once used only to gather the feed, is used on other people. If someone is coming with intention to kill me, i will defend myself even with children scissors, intended to cut nice origamis. Ouch, the word shame is calling strange atavistic responses in me. And the wheels on armoured vehicles….
If you build stuff for aerospace you need to factor in this possibility I’m afraid.
This is great, so long as it remains White-Hat…
White hat for which side?
I’m glad they didn’t call it DVDA ( ͡° ͜ʖ ͡°)