
[via Neatorama]

[via Neatorama]

Wired’s Threat Level takes us on a photo tour of the Defcon Network Operations Center, giving a unique behind-the-scenes perspective of one of the largest computer security conventions. The Defcon Network Operations Center is run by a volunteer group named the “Goons”. They keep operations running smoothly and securely with both high and low-tech resources, like a Cisco fiber switch and an armed guard, to protect the router and firewall.
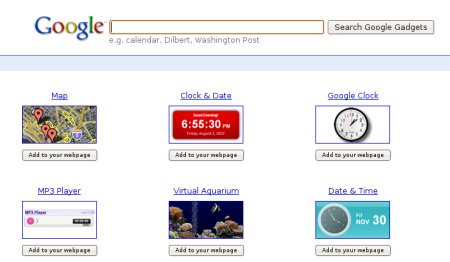
Black Hat presenters [Robert “RSnake” Hansen], CEO of SecTheory, and [Tom Stracener], security analyst at Cenzic, criticized Google in their presentation “Xploiting Google Gadgets”. [Hansen] and [Stracener] say that there’s currently no way for Google to confirm whether Google Gadget creations contain malicious content or not; this leaves the application vulnerable to a wide range of hacking ugliness such as data poisoning, worms, and theft of data. [Hansen] himself isn’t exactly on the friendliest terms with Google. He’s got a bit of a contentious history and he claims that Google has threatened legal action against him. Nevertheless, if what was presented is true and accurate, then Google has a huge security issue that needs to be addressed sooner rather than later. Google has not yet commented on the situation.


[pdp] provides some perspective on the news regarding the GIFAR attack developed by researchers at NGS Software. As he explains, the idea behind the attack, which basically relies on combining a JAR with other files is not new. Combining JAR/ZIP files with GIF/JPG files will create hybrid files with headers at both the top and bottom of the file and allow them to bypass any image manipulation library as valid files. While tightened security and more stringent file validation practices are advisable, the problem is larger than just a vulnerability in browser security. ZIP is an incredibly generic packing technology used everywhere, from Microsoft files to Open Office documents, and of course, in JAR files. He closes with, “any file format that is based on ZIP, you allow your users to upload on your server, can be used in an attack”
[photo: Jon Jacobsen]
[via Digg]
[via Digg]