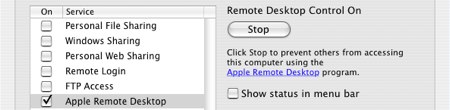
Yesterday, Slashdot reported a privilege escalation vulnerability in OSX. Using AppleScript you can tell the ARDAgent to execute arbitrary shell script. Since, ARDAgent is running as root, all child processes inherit root privleges. Intego points out that if the user has activated Apple Remote Desktop sharing the ARDAgent can’t be exploited in this fashion. So, the short term solution is to turn on ARD, which you can do without giving any accounts access privileges. TUAW has an illustrated guide to doing this in 10.4 and 10.5.










