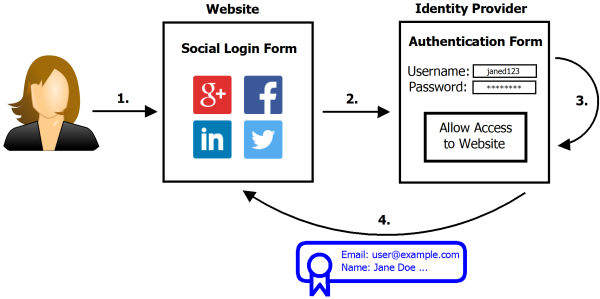
We’ve all seen the social logon pop up boxes. You try to log into some website only to be presented with that pop up box that says, “Log in with Facebook/Twitter/Google”. It’s a nice idea in theory. You can log into many websites by using just one credential. It sounds convenient, but IBM X-Force researchers have recently shown how this can be bad for the security of your accounts. And what’s worse is you are more vulnerable if the service is offered and you are NOT using it. The researcher’s have called their new exploit SpoofedMe. It’s aptly named, considering it allows an attacker to spoof a user of a vulnerable website and log in under that user’s account.
So how does it work? The exploit relies on vulnerabilities in both the identity provider (Facebook/Twitter/etc) and the “relying website”. The relying website is whatever website the user is trying to log into using their social media account. The easiest way to describe the vulnerability is to walk through an example. Here we go.
Let’s imagine you are an attacker and you want to get into some victim’s Slashdot account. Slashdot allows you to create a local account within their system if you like, or you can log in using your LinkedIn account. Your victim doesn’t actually have a LinkedIn account, they use a local Slashdot account.
The first step of your attack would be to create a LinkedIn account using your victim’s email address. This needs to be the same address the victim is using for their local Slashdot account. This is where the first vulnerability comes in. LinkedIn needs to allow the creation of the account without verifying that the email address belongs to you.
The second step of the attack is now to attempt to log into Slashdot using your newly created LinkedIn account. This is where the second vulnerability comes in. Some social media services will authenticate you to websites like Slashdot by sending Slashdot your user information. In this case, the key piece of information is your email address. Here’s the third vulnerability. Slashdot sees that your LinkedIn account has the same email address as one of their local users. Slashdot assumes that LinkedIn has verified the account and permits you, the attacker, to log in as that user. You now have access to your victim’s Slashdot account. In another scenario, Slashdot might actually merge the two credentials together into one account.
What’s really interesting about this hack is that it isn’t even very technical. Anyone can do this. All you need is the victim’s email address and you can try this on various social media sites to see if it works. It’s even more interesting that you are actually more vulnerable if you are not using the social logons. Some real world examples of this vulnerability are with LinkedIn’s social logon service, Amazon’s service, and MYDIGIPASS.com’s service. Check out the demonstration video below. Continue reading “SpoofedMe Attack Steals Accounts By Exploiting Social Login Mechanisms”