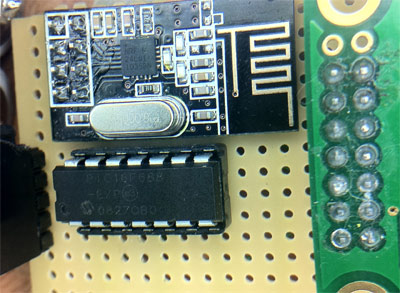
The Nike+ hardware is obviously an interesting device. We haven’t heard a whole lot about hacking one until now, but [Dimitry] has decided to change that. Many would assume that the data transmitted off of these sensors is quite simple, however there’s a bit more than meets the eye. Amongst other challenges, all the data packets coming out of the transceiver are encrypted. [Dimitry] claims to have decoded this data stream and made use of it.
This hack also outlines how one can use this without the stock iPod receiver using a 2.4 GHz chip from Sparkfun. A lot of work has been done to figure out how these packets are decoded and the process one goes through to do this is well outlined in this post. This could serve as a good example for those wanting to figure out similar devices.
One thing [Dimitry] hasn’t done yet is release the source code for this hack. He cites some ethical issues that might not seem obvious on first glance, including the ability to follow someone in a crowd or simply jamming their data. He does add though that if you have a good reason for wanting it, to simply email him. We’re looking forward to what [Dimitry] comes up with in the future using this setup!