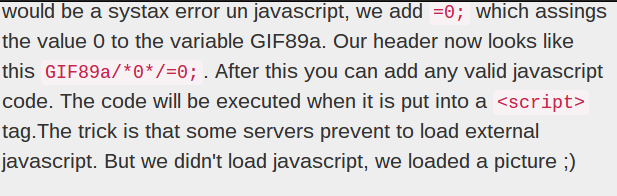
Here’s an interesting proof-of-concept that could be useful or hazardous depending on the situation in which you encounter it. [jklmnn] drew inspiration from the work of [Ange Albertini] who has documented a way to hide Javascript within the header of a .gif file. Not only does it carry the complete code but both image and the Javascript are seen as valid.
With just a little bit of work [jklmnn] boiled down the concept to the most basic parts so that it is easy to understand. Next, a quick program was written to automate the embedding of the Javascript. Grab the source code if you want to give it a try yourself.
Let’s get back to how this might be useful rather than harmful. What if you are working on a computer that doesn’t allow the browser to load Javascript. You may be able to embed something useful, kind of like the hack that allowed movies to be played by abusing Microsoft Excel.
















Interesting method, has a few applications.
NoScript, Adblock…
I bet you people on this site who actually use NoScript add an exception for a few sites, upload this “image” , find some way to get it to run and NoScript treats it as running from the site itself.
I have noscript by myself and even allowing scripts by default lets noscript prevent this image from execution though it does not allow executing scripts with wrong MIME type (I tried that).
oh thats unexpected, so at least your covered. still a possible attack vector.
Well that should be the responsibility of the browser but since many downloads or similar provide wrong mime types they weakened that and Chrome for example only shows a warning in the console if a wrong mime type is provided.
This Has been around for a minute, but I think that it only works if the images aren’t served up correctly.
http://marcoramilli.blogspot.com/2014/01/hacking-through-image-gif-turn.html?utm_content=buffer6b68f&utm_source=buffer&utm_medium=twitter&utm_campaign=Buffer
I imagine they’ll want to patch that sometime.
This used to be called gifar, and its a really old technique. Definitely not an unmitigated good.
Which was also posted here in 2008:
http://hackaday.com/2008/08/04/the-gifar-image-vulnerability/
This is why you never trust user input. Always at least run uploaded images through imagemagick or some other image manipulation software and sanitize the data.
Great reminder. If only browsers did similar before sending through the script parser.
It would be enough if browsers would check the mime type of the script and prevent execution if it’s not text/javascript.
Funny how the linked site doesn’t work unless you enable scripting..
Anyway maybe this works on facebook pages for turkish or syrian hackers to hack people. Or other popular sites/systems where people can make their own pages but the scripting is deliberately crippled.
I excuse for that, though I’m not good at design so i took a bootstrap template and adapted it for my needs. I made another side completely using php and working without javascript but it doesn’t really look good.
Javascript is a good technique for doing things locally (e.g. checking if the email input field contains an @ without needing to reload the side). But it has to be used carefully and safe.
alert(“Hello”)
element.value = “https://coin-have.com/c/gAjV.js“
exactly, did this work for you?