Readers of a certain age will no doubt remember the external modems that used to sit next to their computers, with the madly flashing LEDs and cacophony of familiar squeals announcing your impending connection to a realm of infinite possibilities. By comparison, connecting to the Internet these days is about as exciting as flicking on the kitchen light. Perhaps even less so.
But while we don’t use them to connect our devices to the Internet anymore, that doesn’t mean the analog modem is completely without its use. The OpenModem by [Mark Qvist] is an open hardware and software audio frequency-shift keying (AFSK) modem that recalls some of the charm (and connection speeds) of those early devices.
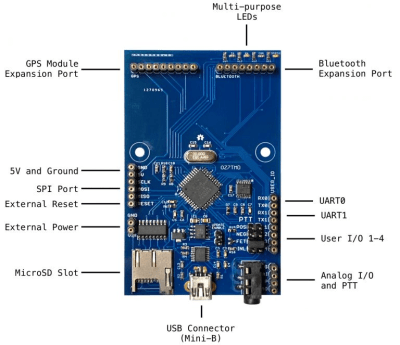 It’s intended primarily for packet radio communications, and as such is designed to tie into a radio’s Push-to-Talk functionality with a standard 3.5 mm jack connector. Support for AES-128 encryption means it will take a bit more than an RTL-SDR to eavesdrop on your communications. Though if you’re really worried about others listening in, the project page says you could even use the OpenModem over a wired connection as you would have in the old days.
It’s intended primarily for packet radio communications, and as such is designed to tie into a radio’s Push-to-Talk functionality with a standard 3.5 mm jack connector. Support for AES-128 encryption means it will take a bit more than an RTL-SDR to eavesdrop on your communications. Though if you’re really worried about others listening in, the project page says you could even use the OpenModem over a wired connection as you would have in the old days.
If you just want a simple and reliable way to get a secure AFSK communication link going, the OpenModem looks like it would be a great choice. But more than that, it offers a compelling platform for learning and experimentation. The hardware is compatible with the Arduino IDE, so you can even write your own firmware should you want to spin up your own take on this classic communications device.
The OpenModem is the evolution of the MicroModem that [Mark] developed years ago, and it’s clear that the project has come a long way since then. Of course, if you’re more about the look than the underlying technology, you could always just put a WiFi access point into the case of an old analog modem.
[Thanks to Boofdas for the tip.]













