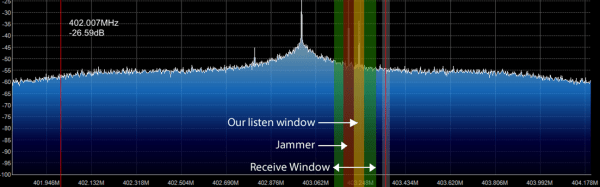
The RF signal transmitted from a modern key fob and received by the associated vehicle is only used once. If the vehicle sees the same code again it rejects the command, however there is a loophole in those carefully chosen words. The code must be received by the vehicle’s computer before it can be added to the list of spent codes. [AndrewMohawk] goes through the process of intercepting a code sent from a key fob transmitter and preventing the vehicle from receiving it in a thorough post to his blog. You can see this attack working in his studio quality reenactment video after the break.
[Andrew] uses the YARD Stick One (YS1) which is a sub-GHz wireless tool that is controlled from a computer. The YS1 uses RfCat firmware, which is an interactive python shell that acts as the controller for the wireless transceiver.
This system is not without its problems: different frequencies are often used for different commands, [Andrew]’s scripts are designed to work with On-Off keying (OOK) leaving it useless when attacking a system that uses Frequency-Shift Keying (FSK). There is also the issue of rendering a target key fob non-functional but you’ll have to pop over to [Andrew]’s blog to read more about that.