 Most spy movies (at least the ones worth their salt) will include a few scenes that depict nerds in a van listening in on conversations remotely and causing the victims phones to do things like turn themselves or their cameras on. We have been made to believe that it takes an entire van of equipment and one or two MIT level hackers to pull this off. Turns out all it takes is about $2300, some know how, and an unsuspecting target with a set of microphone-equipped headphones attached to their phone.
Most spy movies (at least the ones worth their salt) will include a few scenes that depict nerds in a van listening in on conversations remotely and causing the victims phones to do things like turn themselves or their cameras on. We have been made to believe that it takes an entire van of equipment and one or two MIT level hackers to pull this off. Turns out all it takes is about $2300, some know how, and an unsuspecting target with a set of microphone-equipped headphones attached to their phone.
The French Government’s information security research group ANSSI has been investigating this and published a paper with their findings. Unfortunately that paper is behind a paywall. Wired has a pretty good summation of the findings, which use a transmitter to induce a current in the headphone wires. This in itself isn’t surprising. But they’re able to do it with such accuracy that it can both trigger, and successfully interact with the hands-free features provided by Siri and Google Now.
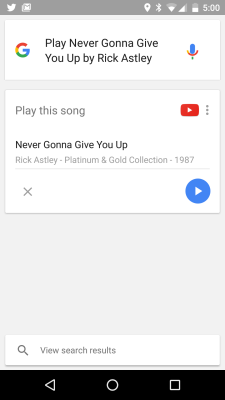
We think this is a really cool proof-of-concept. It’s mentioned that an attacker could potentially use this to make calls or do other things that cost the victim money. We think it’s more likely to be implemented by resourceful young engineers as a practical joke. Rick Rolling is a poplar go-to. But if you can make the phone “hear” audio, you should also be able to make someone wearing headphones hear ghosts. This has a lot of potential. The first one to make this happen really needs to let us know about it.