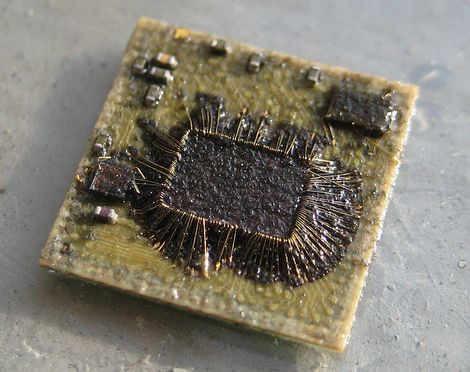
[Travis Goodspeed] recently tore down the Freescale MC13224 wireless radio chip in an effort to demonstrate how the device’s firmware could be read, even when locked down in “secure” mode. While you might not recognize the Freescale MC13224 radio by name alone, you are certainly familiar with some of its practical applications. Found in the QuahogCon and Ninja Party badges among other consumer goods, the popular Zigbee radio turned out to be a fairly easy conquest.
[Travis] first used acid to decap one of the microcontrollers to see what was going on under the plastic casing. Inside, he discovered a discrete flash memory chip, which he removed and repackaged using a wedge wire bonder. He was easily able to extract the firmware, however decapping and repackaging a flash chip isn’t necessarily the most user-friendly process.
After digging further, he discovered that holding one of the chip’s pins low during boot would allow him to run custom code that recovers the firmware image once the pin is pulled high once again. This far more practical means of firmware recovery can be easily facilitated via a circuit board revision, as [Travis] mentions in his blog.















That’s hardcore, one warranty definitely voided.
It’s also awesome.
That is some industrial-espionage grade hacking right there.
>The first method for recovery requires access to some rather–but not terribly–expensive equipment…
>Then use a wedge wire-bonder to place the chip into a new package.
I’ve looked into wedge/ball bonding before but have given up once searching for hardware. Anyone have any experience with any manufactures that have ‘easy’ to maintain equipment for similar experimentation?
Travis, rawks, he is very neighborly :)
Funny how they write “He was easily able to extract the firmware”, under an image which doesn’t look easy at all!!
Two Snake Dogs for Travis!
That picture screams “easy”.
Ok, so popping caps is dumb and can be done by a 3 years old kid with no skills whatsoever, but on the other hand, THAT is a hell of a hack. Well beyond my skills, but very well done.
Sorry, I’m still p*ssed off at the fact that a Youtube video of a cretin popping caps (skills needed: ignore that red is +) made it on HAD not long ago, and more appalling, that many readers found it awesome. I started taking medications and booked a hypnotist for tomorrow, so hopefully I’ll get over it soon.
Cricri,
All work and no play makes Cricri a dull boy.
Lighten up and live a little. Blowing up caps and showing the resultant video isn’t any less productive than watching TV for an hour.
Sometimes stupid things like that are a nice distraction.
Sooo…what am I looking at in this pic?
@GameboyRMH:
The innards of a Freescale MC13224 ARM7TDMI-and-Zigbee SoC
What is the benefit of doing this?
Its interesting to see how he goes about it, but what is the end result?
that’s sick.
The end results are that he managed to get out all the secrets in the on-board storage without releasing the magic smoke. This chip still works (unless I’m misunderstanding what’s happening in this hack).
This reminds me of that hack from a year or two ago where they russian guy dissected and gained access to an Infineon encryption IC.
All we need now is the ability to errode the lids off ICs using regular household chemicals (toothpaste and bug spray perhaps?)
Didn’t he violate the DMCA by doing this? Uh Oh… Now they’re going to come for him. Or maybe they’ll just stick a GPS tracker on his car or feel up his private parts for awhile.
Money well spent…
I love it !!!