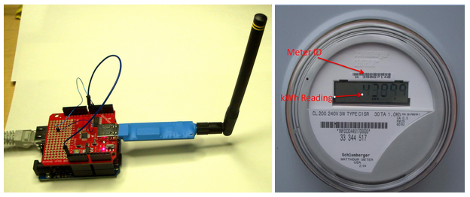
Both our electrical meter and our gas meter are located in the basement of our house (we recently had the gas meter moved outside though). When people see this they always ask if the meter readers have to come inside once a month. The answer is no, these meters broadcast usage data which is picked up once a month when a utility company vehicle drives down the street. If you have wireless meters in your house, here’s a way to harvest and graph the wireless data so that you can analyze your usage patterns.
The hardware used here is a special USB dongle. This has a 900 MHz radio which picks out the packets from a reasonably large list of meter types, and pushes them through the USB interface. In the image above you can see that an Arduino with a USB host shield is used, but there are also drivers if you want to connect this directly to your computer.
We looked around and didn’t find any specifics on the hardware used on that board. But it can’t be all that hard to make one of these at home… the populated board seems to have just two ICs and a few passive components. Anyone up to the challenge of hacking together their own packet sniffer? We wonder if the Next HOPE badge could pull down the data?
[Thanks Chris]















What about modifying this data (injecting packets) on the fly when readers pass along the street, making it look like you used less electricity? XD
That would be illegal and not allowed to be discussed here.
> and not allowed to be discussed here
lol no
DeadlyFoez: I’m sorry, really came out wrong. I meant it *for the sake of hacking*. I’m pretty sure this data is encrypted or scrambled and understanding and relaying it would be some awesome feat. Rephrasing: A ‘milestone’ would be you modifying your own packets and adding 1 dollar to your bill, in a way you could detect later (that would be awesome like…. 63″1337″ kwH)
I hope this clears out any misunderstanding!
I wonder if the police need to get records from the utility companies or if they could just drive down the street with a device like this to monitor people’s energy usage. Easy way to catch people growing pot, for example.
On the other hand, any schmo could spy on neighbors’ energy usage to use for fun or evil. Plan a robbery by nailing down the inhabitant’s schedule through power readings? Or maybe put it in your car and log the power along with the time and location, so a map could be built up.
To the best of my knowledge power usage seems to be public information (at least here in Canada) Anytime I move and get hydro the hydro company always freely gives me average balances for each season as well as the last total amount. So the cops probably dont need a warrant. But any good grow op will steal the power anyways. Cops driving down the road scooping this info is a good way to stop the dumb growers quickly though.
The authorities can scoop this data through the same avenues they scoop data from ISP’s. If a typical home has a grow operation it is easily spotted by the utility. The average load factor compared to other homes around it is WAY to high. Anything approaching 80% is suspect because the load too flat over time. Plus these bills are paid timely and the utility likes that. It’s like Crack —> Pagers —-> Pay Phones. Telecom took all those quarters & pager subscriptions to the bank.
Since use data can be read so easily, what keeps crooks from driving around looking for low usage times/homes to burgle?
Its true that for the most part the data could be found by hopping a wall or using binoculars, but its so much less intrusive to check stats via parked car or nearby apartment.
I think projects like this show why there need to be passwords/encryption, but i for one am going to look into an adapter to read my gas/water usage (my area is not doing wireless power meters yet)
The only information you get is the meter’s serial number and the current KWh. You’d need a way to find which house that corresponds to. In a rural area, you may be able to guess from the low numbers, but in an apartment block or city, without having access to the power company’s records there’s no way.
Current KWh is all a burglar needs. Drive around at dusk until you find a house with a low power usage (very unusual during dinner time), and then look out the window and find the house with all the lights off. Come back 3 nights in a row to check that house for power usage and lights. Chances are the occupants are on vacation.
I can’t reply directly to the Anonymous reply saying current kWh is all that’s needed, but I think there’s a confusion between kWh and kW. The kWh is analogous to a car’s odometer reading, while the kW is analogous to the speedometer reading.
With a one-time kWh reading only, you have no way of knowing which houses have low power usage, just as a car’s odometer reading doesn’t tell you how fast it’s going. If you kept records and repeatedly surveyed kWh readings, watching how they’re changing from one day to the next, you could eventually figure out average power usage.
This isn’t directly related to adric’s suggestion but looks like hacking power meters is an issue. Yet another industry that’s going to learn to incorporate security in the initial design.
http://krebsonsecurity.com/2012/04/fbi-smart-meter-hacks-likely-to-spread/
Thanks for the link. It was interesting. I am sure that the losses incurred by hacked smart meters is less than the increased revenue from replacing the mechanical meters which *supposedly* under-reported power consumption.
The writeup says one of the two chips is a PIC. I would have guessed that the other was a CC1110 or similar as used in the IM-ME, but the chip package looks different (the CC1110 and the nRF chips uses a QFN package). Note that the NextHope badge uses a Bluetooth chip and wouldn’t operate in the 902-928 MHz band this dongle does.
As for making one at home, it could be tricky. The CC1110 is sensitive to the quality of the layout and 0402 sized parts are used. Whatever chip is used here would likely have similar issues.
Speaking of the CC1110, I blogged yesterday on how to use an IM-ME to sniff the packets from my Davis Weather Station.
http://madscientistlabs.blogspot.ca/2012/04/achievement-unlocked-im-me-weather.html
This post has me wondering if I could sniff my water meter as well???
Greg H. of Grid Insight here. Yes, the Grid Insight AMRUSB-1 will receive and decode signals from Itron 60W and 100W water meter transmitters — the 60W is respecially common — and several Itron natural gas transmitters. We also have a design (not yet in production) for a similar receiver dongle that will work with Badger ORION water and gas transmitters. Signals from Neptune R900 water transmitters can also be received, but not decoded without infringing a Neptune-owned patent (AFAIK).
looks like you typed in your web address incorrectly. I think you meant to send people here: http://www.gridinsight.com/
Hi Greg H. I saw some of your posts here. Interesting stuff.
http://davestech.blogspot.ca/2008/02/itron-remote-read-electric-meter.html
Do you mind me asking what chip you use to receive the RF signal?
The TNH badge is not bluetooth, it’s 2.4ghz nRF.
Since the article says it talks 900mhz, it would not be possible to use a TNH badge directly. However, using the generic goodfet firmware, it would in theory be possible to talk to a radio chip over SPI which could decode it.
As I understand it from our utility; They send a request to local substation (or from) to start reading meters. The substation sends out a request to each of the meters on the downstream lines, then sends that data back up-line to HQ (like internet over power-line). No drive-by’s required in our neighborhood. (We live in a rural area, driveways a half mile long.) What’s the estimated range on your dongle?
This is probably being conducted over a AT&T mesh/self-healing network. In neighborhoods with poles and wires you can see the wireless nodes/antennas on top of the crossbars spread out around the neighborhood and the nearest substation. You can also spot the power-line units which have a clamp around a power wire using the magnetic field for current.
The receiver in this writeup is the Grid Insight AMRUSB-1. I designed it. I’m working on an inexpensive Ethernet version (AMRETH-1) which will make all the extra Arduino glue hardware unnecessary. If you’d like to stay informed, sign up for the mailing list at GridInsight.com.
Great work Greg! I look forward to your new ethernet device. Now if I could just get my utility to use a newer meter with more resolution :-) I also need to work on a Pachube app that calculates rate of usage over time instead of just displaying the total kWh
It looks like these type of meters have already been hacked. I don’t know if it’s this particular model or not.
That particular hack requires physical access to the meter. Physic security can block this type of attacks.
A wireless attack would be much more fatal.
Ooops.. it’s not your meter :) Not sure how it is in other areas but here we have to purchase, thus own the meter box, but the meter itself is the property of the power company. No doubt the power company is the legal owner of any data the meter generates. I’d go as far as to guess they could block our viewing of the meter read out. In that we own the line from the meter to our service panel we would be free to install or own meter if we wish.
I don’t want to hack the meter. I just want to compare the kwh the utility posts a day later to see if the on-peak/off-peak tariffed hours match or sync up.
I wonder what subset of meters this works on. The local smartmeters are encrypted and I’m not having any luck getting the utility to give me access to my own meter.
The AMRUSB-1 data sheet lists the compatible radio-equipped meters: http://www.gridinsight.com/amr/Grid_Insight_AMRUSB-1_Data_Sheet.pdf
http://forums.hackaday.com/viewtopic.php?f=8&t=2118
it will do the itron meters. i posted board pics @ link above. i was going to start working on the exact same thing but hell. im gonna get one of these now.
The Itron uses Cisco’s OpenWay network. You can jump on that network with a 900MHz radio.
http://it.slashdot.org/story/12/04/09/1655259/fbi-says-smart-meter-hacks-are-likely-to-spread
There we have it. This type of talk leads to illegal activity.
hmm. I’m not sure that there is any evidence to indicate that discussing pulling usage data from a power meter in your own home (and security or lack of security on the device) leads to theft.
There is nothing wrong with learning. It’s the applications of the learned skills or information that people need to keep straight. It’s not a problem for most of us.
They really read these meters every month? This sounds ridiculous. Where I live, we have to pay an advance every month and the meter is read and finally billed every year or when you move out.
How does this work. I have the iCon smart meter (http://www.sensus.com/documents/10157/32597/iCon_A-datasheet.pdf) [PDF], which says it uses “ZigBee with PKI authentication”. Does this Grid Insight work with the smart meter companies? It does say on their website they don’t sell them to just anyone so that leads me to believe it is a partnership. Can you clarify Greg H?
The AMRUSB-1 receiver doesn’t speak ZigBee. Entirely different radio protocol.
It looks like my Smart Meter is listed in you list of compatible devices (http://www.gridinsight.com/amr/Grid_Insight_AMRUSB-1_Data_Sheet.pdf) unless I am confusing models.
Also, do the meters in this doc encrypt the data?
Cool build.
I have one of these meters and now I know what has been screwing up my 900mhz comms for my thermometers I have around my home and workshop.
hmm i heard one unlucky guy got charged over a million dollars in one month and they tried to convince him it was his usage roflmao!
first of all, that meter cant physcally measure that much. it will catch fire first. PhotonicInduction (from youtube) tried that and the meter under test caught fire at around 300 amps (it was a small 100A unit).
and second, you couldnt “fit” that much electricity through those cables leading up to that house, without them melting and disintegrating.
must have been a digital meter,,,
it was probably a driveby theft,
and deposit into an “empty, and deactivated” meter.
aka they cloned the serial number.
its a new electronic twist on the oldest trick in the book.
it used to be that you could protect your house with a shotgun or a baseball bat, now weapons are useless and people will rob you from several blocks away.
or from around the world.
I’m trying to make some sense of your post.
I agree you’re not going to fit $1M worth of electricity into a house in a month, but after that I disagree strongly.
You are surmising that there was a drive-by theft… and that the serial number was the item stolen and that someone then somehow hacked another meter to send out the serial number not belonging to it?
Seems to me that:
a) This type of theft is possible but highly unlikely in this case. While it may be easy to read the data from the meter it requires another level of technical sophistication to modify the data that is sent. Individuals intelligent enough to do that are probably smart enough to not get caught by neglecting to match the kw reading on their meter with the meter they are “stealing from” (see (b) and (c), below). (Neglecting to do so is the only way I can think of to accumulate a $1M bill in one payment period without simply waiting to be caught.)
b) It would be rather easy for the utility company to track down the offending meter based on the range within which the transmission would be received (assuming the meter wasn’t transmitting over the power line, though it also wouldn’t be too difficult in that case), so this type of theft would perhaps be not the smartest thing to do?
c) It would be even more trivial for the homeowner to go look at the numbers on the front of his meter and confirm for the utility company that they don’t match the usage numbers on the bill.
d) It seems much more likely (to me) that a technical glitch in the meter caused an inaccurate reading, or that the utility company billing department simply screwed up.
in my area, all the power meters are read over the utility company’s network-over-power infrastructure, they dont even read the meters from the same city!
and by drive-by i meant drive upto and plug into house’s front porch outlet,,, to gain access to the whole neghbourhood’s data-over-power-network.
EDIT: drive-by was only something to joke over.
they would have done it from accross the city, or state
EDITEDIT: they still need to drive-by to get the serial number, unless random attack/theft.
the perpetrator of this 1M theft was never caught, in fact, the newspaper never mentioned a perp… they only stressed that it was the customers actual usage, lol
PS: but i still agree it was probably only a hacker’s joke. i mean make him owe one million, rofl HOW MANY DIGITS CAN I ENTER IN? 999999999999999999.99 ?!?!?!?!?
hahahahahahahha XDXDXD
Maybe a job for the GirlTech IMMe?
AFAIK the itron 60s used by national grid in new england and the attached amr units are set to only push data for a set four day period. The electricity used to operate the meter display and amr unit come from the power companies side of the meter and not yours, so this would make sense as a money saving measure if I am correct. I also believe that the amr serial number is different from the meter serial number, and not displayed on the meter anywhere, so it would be difficult to use this to measure usage on meters in close proximity and know what specific residence you were looking at.
Large variety of organizations looks for this material but they cannot get efficient one. I really thank you for talking about it
https://www.accounting-guru.net
on this page the last comment was in 2013 is this still active
was anyone able to get an AMR-USB-1? I was exchanging emails with Grid Insight a couple of years ago, and never bought one from them. Now they don’t answer emails. I’d like to get one if someone has one, or even an alternative device that does the same thing.
Me too! These were great products but seems like they or anything like them are no longer available.