[Thice] discovered a vulnerability in encrypted portable storage a few years ago. He’s just pointing about the exploit now. He mentions that he notified manufacturers long ago and we’d guess the wait to publish is to give them a chance to patch the exploit.
He calls it the Plug-Over Attack and for those who were involved with original Xbox hacking, this technique will sound very familiar. The Xbox used hard drive keys to lock the device when not in use. When you booted up the console it checked the hardware signature to make sure it was talking to the right motherboard. But if you booted up the device, then swapped the IDE cable over to a computer without cutting the power you could access the drive without having the password.
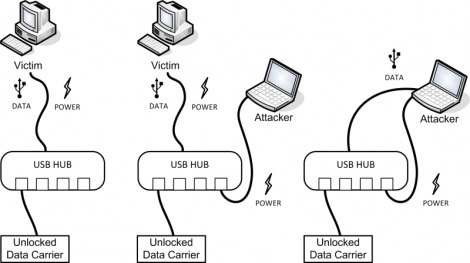
This attack is pretty much the same thing. Plug in a drive, unlock it on the victim system the normal way, then replug into the attacking system. In the image above you can see that a USB hub will work for this, but you can also use a hacked USB cable that patches a second jack into the power rail. For some reason the encryption system isn’t able to lock itself when the USB enumerates on the new system, only when power is cycled. Some of them have a timer which watches for drive idle but that still doesn’t protect from this exploit.















Yeah, the hotswap technique was pretty popular as an exploit for the XBox1. I hotswapped mine the other day, and was kinda scared that this could be done, especially with half my drives encrypted. But still, nothing new here. Exploits are always found, hackers find a way
Heck some of those old portable HDs (the little 2.5 non-ssd fully powered from USB ones) came with a cable that had a second power only USB plug on it. I guess it was designed so that you could pull power from two ports so you could get more than the USB spec’s 500mA. With computers these days supplying more than that regularly with no need for the second head, a cable like that this hack would be trivial.
Plug full head (with data) into victim machine. Plug power head into attacker/external high power supply. Then swap the data cable over and you are set. No crazy splicing required. Heck the victim might be using THAT CABLE right now on his computer (were lazy like that [looks at his ext hd]).
Might be time to chop that power head off.
this only applies to locked storage, not encrypted. encrypted storage passes all reads/writes through an encryption layer.
the use of the term ‘crypto’ in the target article refers to the use of cryptographic algorithms in the password step.
no-one with a hardware or software encrypted drive need worry about this attack vector.
I believe the article is discussing encrypted external disks that have on-board crypto hardware. The data channel between the storage device and the computer is not encrypted, after the correct keys have been provided.
I am sorry to tell you, but you are wrong. Yes this does not work on software encryption (which also is not mentioned in the article at all), but this does work on hardware level encryption. It is not just locked drives, it is encrypted drives.
Buy a drive and test it yourself.
Why would anyone use such encryption anyway? If the enclosure board fails you lose everything…not so with Truecrypt.
the average computer user wants “security”
Also i have done the xbox drive swapping in the past. Much easier to do a softmod or modchip, though.
Same exact reason that microsoft used it.
To prevent people from upgrading, modifying, and swaping out hardware.
When it breaks, they don’t want it to be fixed by some guy with cheap hardware. They want you to buy a new console
I call useless on this.
I do understand the “why it works” reasoning (and it does work), but why would you need this “attack” in the first place.
Any real security person knows the moment you can gain PHYSICAL ACCESS to the secured device (computer or drive), it can and will be hacked.
My reasoning? If you get this close to the ‘victim’ to execute the ‘attack’ you might as well just do everything ON the victim’s computer.
In the case of the xbox it might make more sence, but USB storage devices? Really?
Lolz
Since the exploit to extract RSA keys, is this attack obsolete? http://arstechnica.com/security/2012/06/securid-crypto-attack-steals-keys/
(I’m not offering this suggestion, I’m asking a question here; I’m uneducated in this subject, and these are both recent developments. Anyone with the right knowledge, please let me know!)