It had been requested that we make a short video covering the top worst hacks in movies. Being the community that we are, it seemed like an interesting request. We asked for your input, and you were happy to deliver! However, the proposition of creating a “top 10” list turned out to be quite difficult. There were just SO MANY horrible scenes that I started thinking about how to even categorize them. We could probably to a “top 10” in any of the following categories without even having to dig too deeply:
- hacker lingo
- mocked up interfaces
- fake input devices
- virus screen-takeover moments
- access denied messages
- hardware taped together
Honestly, after breaking it down in such a manner, making the top 10 movie hacking failures, felt painfully general. It is like making a list of “top 10 animals that ever existed”. The state of technology portrayal in movies is frankly abysmal. It is obvious that the only people who know less about tech than “hollywood” are the people making laws about it.
So, lets take a look at this list and see what we ended up with.
10. The Core
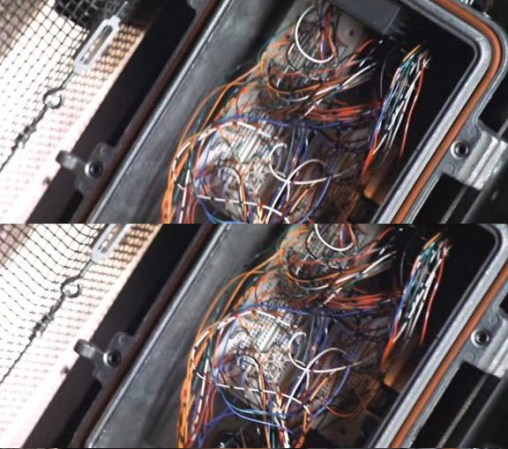
There’s a scene where they have to get through a door and it won’t budge. To open it, they’re going to have to crack into the control panel and hotwire the the thing. What do they find inside? A breadboard. Ok, well, we all know that in that environment, you wouldn’t be finding any breadboards. Then again, I’ve seen some duct taped together networks in large corporations that might convince me that this one isn’t a failure at all.
I’ve heard so many people point out this scene as a failure, and it is usually for the wrong reason all together. The young woman sits down at a computer and announces to everyone “hey, I know this, it is unix!”, while the camera switches to a 3d rendering that looks like a physical layout of a neighborhood.
“aha! that’s not a real interface!” is usually what I hear from people, but they’re wrong. It was called FSN and did actually exist. No one really used it though because, while neat, it wasn’t a great way to actually work. Tons of people loaded it up and played with it, but it never really caught on. I actually wouldn’t have been surprised to see a super gratuitously funded IT department loading stuff like this in their spare time because they had convinced the boss man that they totally needed that SGI for… uh… network security or something.
The real hack failure is the fact that her simply recognizing the operating system means that she now has full control over EVERYTHING in the Jurassic park network.
8. Firewall
This one is fun because it gets into a little hardware hacking. I LOVE improvised devices, so it caught my interest. It turned out pretty silly though. In the movie Firewall, [Harrison Ford] needs to get data off his screen to someone far away. To pull this off, he rips the scanner head from his fax machine and attaches it to an ipod. He remarks that the ipod won’t know the difference between “10,000 files or 10,000 songs”.
This is where the hackaday crowd really comes into play. Many will recognize that it is wrong, but only here will you find people that might actually figure out how it would have to really work.
First, you need something to read the data from the scanner head. Then, it needs to be converted to an actual file that is compatible with the ipod. Then you would have to initialize the transfer onto said ipod. That means that there’s got to be a decent amount of hardware and code going on in between the two items. To be fair though, they do show something there as an interface, so maybe I should have left it off the list. However, I challenge anyone to pull this off as fast as he did.
7. Goldeneye
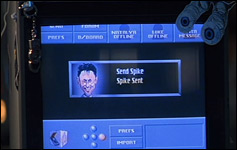
In the beginning of the movie Goldeneye, they are establishing just how fantastic [Boris] the hacker is. After an “access denied” screen that could easily be part of another list, [Boris] proceeds to hop into the network of the CIA. When he’s caught, he simply issues this magical command: SEND SPIKE. The nasty security guy who caught him is immediately disconnected. Wow. I don’t even know where they were going with this. I guess it was just supposed to be another notch on the “[Borris] is amazing ” tally sheet.
6. Hackers
This movie always comes up when talking about hacking. Some people love it, some hate it. The accuracy of the movie is about as divided as the fan base as well. They do a decent job of showing how tedious and silly hacking can actually be, but when they show the 3d renderings of the data, it all falls apart. However, this movie was released in 1995, and at that time we really had high hopes for the immediate future of 3d interfaces (see FSN). It is like our generations version of “jet pack disappointment”. I was promised spacial file navigation and I’m not upset that it hasn’t been delivered.
5. Swordfish
Swordfish came out in 2001. It has no excuse for 3d renderings of data. By this time we knew that the 3d interface of the future wasn’t really very usable (again, see FSN). Not to mention the gratuitous blow job/ gunpoint uber hacker scene that made my beverage attempt a quick escape out my nasal passage.
4. Skyfall
In this latest installment of the James bond series, I was incredibly let down. As a child, I found [Q] to be one of the coolest things ever. I wanted that job, bad (this job is slowly turning into that actually). When I heard that the actor who played him passed away, I thought they would take this as an opportunity to do a resurgence of gadgetry with the new [Q]. Unfortunately they continued their slow slide toward an entire 2 hours of sullen looks and knees to the ribs.
The scene that really almost caused an aneurism was where [Q] proclaims that the only way to look at the data on the computer is to attach it to their network (wow, really?). Then they proceed to look at the encrypted data as a giant 3d sphere. This trope is already bad, I mean why would you look at encrypted code as a sphere? On top of that, [James Bond] recognizes a word in plain text. This somehow unlocks all the encryption.
What comes next is the really painful part. We are looking at encrypted CODE. When you decrypt code, you get code. Sure, you might be able to then RUN that code to get some kind of a visualization, I guess. What you don’t get is your encrypted code morphing into a visualization of a map.
Hackers don’t put bombs in peoples computers. If they did, they wouldn’t set them to initialize using a keystroke. I mean if you can remotely make their screen go all wiggly, can’t you just detonate your damn bomb?
I’m not exaggerating when I say that I didn’t know if this was a joke. [Jack Black] does that bit where you rotate an image in a direction that is physically impossible. [Jack Black] is a comedian. Admittedly I didn’t see this movie till after [Jack’s] career was more established, so maybe it wasn’t as obvious back then.
1. Stupid Crime shows on tv like NCIS, CSI, BONES, etc.
Yes, I know it isn’t a movie. They’re just so amazingly horrible that I couldn’t leave them out. It has become this massive joke just how horribly incorrect they are. It has actually gotten to the point that I’m convinced they’re doing it on purpose. While I can understand a tiny bit of writing being targeted for audiences that aren’t familiar with the technology, some of it is simply too much.
The example of “two idiots one keyboard” is one that stands out. It is conceivable that you or your audience may not be familiar with hacking, or don’t know what a believable game would look like, but every one of you has used a keyboard. The script was probably written in a word processor using a keyboard. Hell, this is older than computers themselves, typewriters have them. Two people can not type on a keyboard simultaneously. It doesn’t work and everyone on the planet knows it.
























This was pretty good! I’d like to see the top 10 access denied pages.
lawnmower man has to be in that
oooh, those were nice.
My eyes rolled over when in Enemy of the State, they flash to a quick shot of
a communications satellite while the audio plays morse code at about twenty words per minute. Pretty poor data stream!
the scanner was at least plausible.
Oh, and your videos are getting better every day! Keep it up!
Thanks!
I bet if it was an iPhone/iPad it would work.. There’s probably an App just for this eventuality! ;)
Were iPod’s able to record audio (via a mic)? If so, and if the scanner gave it direct [analog-ish] scan data and just fed that in as an audio signal then you wouldn’t need all that encoding and protocol interface stuff. However one would need to have software that could post-process the “audio” file and decode the real image content. This might only require exporting the audio in a raw “WAV like” format and then run that file through rawtoppm (or equivalent) and you have the image. Maybe this one should be sent to “Myth Busters” (not sure how they can make it explode in the end though)!
It looks like Harrison Ford’s just holding the CFL lamp though
That scanner likely couldnt focus that far away and good luck getting a consistent speed by hand.
Sneakers is generally a pretty realistic movie, but I especially like when they figure out some guys password by watching him type it on video.
This was a “plausable” part of Hackers too — Nikon walking around an office snooping people’s passwords. In my experience, office workers don’t really care that much about password security, and snooping it would be fairly simple with a good memory.
I am with you their man! I love sneakers! I like the part where they defeat the keypad door lock.
I liked sneakers as well, but the part irritating to me was the guy reading the braille output while it was changing…
I never realized how easily people give up their credentials until an employee at the college I attend gave her password out at orientation in front of 40+ strangers. She knew full-well that I was pursuing an InfoSec degree too; maybe she’s not aware of what information security actually is. SMH.
can anybody tell me the movie that involves hacking a power grid, and shutting down half of the US’s Power??
@Tim apparently your comment is too deep to reply to…Also @ hackaday, simple UX design guys, report comment goes at the TOP of the comment, not at the logical reply position. FFS. Also I reported a post.
Name of the movie: Live free or Die Hard
23 – Nichts ist so wie es scheint, pretty realistic movie about hacking. Only one scene was not realistic, when Atari ST has crashed and hacker was not happy of owning that computer ;)
yes, it’s pretty realistic. its first shown at the chaos communication congress…. the biggest hacker conference of europe….you can imagine what happened if not….
Hovering your mouse over the images reveals a joke. I look for these when krafty caleb starts to rant. They’re always good for a chuckle.
“It is obvious that the only people who know less about tech than “hollywood” are the people making laws about it.”
It’s funny ‘coz it’s true!
that’s a whole other rant.
Lookin’ forward to it! :)
CSI definitely deserves the #1 spot, it’s unintentionally self-parodying in its hacking awfulness. I haven’t been able to make myself suffer through any episodes of Bones but I’ve seen some ads featuring Star Trek-like holographic displays. NCIS, I think has been trying to clean up its act in this area. I’ve seen some CSI-grade awfulness in early episodes but more recent ones actually have decently realistic explanations of technical issues, although they haven’t eased off of the visual sillyness.
I agree with you on Bones. I like how they can run simulations instantly and they have models for everything. O u say he got hit by a lawnmower with a bear on it. Let me just run this bear-lawnmower simulator and we can tell instantly what happened!
CSI overtly acknowledges how silly it all is often enough that I really, really don’t buy that it’s entirely unintentional. There was one episode a while back where one of the investigators asks a tech to zoom in on a person in a video. It turns into a mess of pixels. The investigator asks the tech if he can “enhance the image.” The tech says “Nope” then literally walks away whistling. Same goes for the psycho-babble in Star Trek (WE NEED TO REVERSE THE POLARITY OF THE TACHYON FIELD): someone’s having fun with the script.
The stuff that drives me bonkers is gun bullshit. I’ve seen movies where a character does the dramatic cock-the-hammer-to-show-your-really-serious with a gun that doesn’t have a hammer (really, you just HAD to use a glock for that scene?). In the Matrix lobby scene, at one point Neo fires a pair of Skorpions. It shows a closeup of casings hitting the floor, and the casings are from rifle ammo, 5.56mm.
Two of the best movies that fit the hacking category would be The Matrix (second one) and Sneakers.
wargames too.
Watching Wargames should be a freshman level course requirment for any aspiring computer science major… if you haven’t seen it, you haven’t lived.
Wargames number one IMHO.
+1
Definitely agree with The Matrix, I do remember seeing a particular nmap attack on one of those. Don’t think I’ve seen Sneakers though.
Sneakers is worth a lazy Sunday afternoon viewing.
It was when they break into the powerplant. Trinity used nmap to discover an ssh port, then used sshnuke (fake program) to take advantage of an old SSHv1 CRC32 exploit (buffer overflow) to gain root access. The tool was fake, but the buffer overflow exploit actually existed.
Gosh, I’d have put Independence Day at the top of the list. Not only do we somehow give the aliens a computer virus, but earlier in the film the aliens need to use our satellites to coordinate their attack?! Really? Don’t get me started on this abomination…
I think both of those were explained away by claiming that our computer tech was directly reverse engineered from the ship at area 51.
That, and as far as the use of our satellites to communicate, the line-of-sight is a real concern that these aliens solved by using our systems. From the veiwpoint of the aliens, we was hacked. :|
Or the other one, where he flips his device up onto the car roof and tells the chick in the White House what room she’s standing in… Pretty sure even back then the White House was TEMPEST secured.
Not if the cell phone signal reached the tower(s) enough for a reliable call. ;) Plus, cellphones weren’t supposed to be used around many forms of equipment because they emit a signal that effectively becomes an active attack on some devices. A STU-III telephone was considered compromised if certain phones got within around 20ft of it.
TEMPEST is one of those things that was expensive, complicated, and limiting to the point that most organizations tried to do as little of it as possible. Still true. Yet, we’re seeing quite an uptake in demo’s in emanation attacks from universities to hacker conferences. Defense side should get interesting again. :)
“Computer, ENHANCE! Computer, ENHANCE!”
The Social Network “hacking” scene is pretty realistic, Mark is just making some pearl scripts in emacs
The social network totally got it right with that first scene where he is hacking perl scripts to scrape data.
Yes! I laughed at “wget magic”
http://www.youtube.com/watch?v=odOzMz-fOOw
I’m sure there was some curl magic going on as well. It was a relief to watch that movie, with a few fellow CS students, and see things that were actually real things. More movies need to follow this example.
was at least plausible – but would have taken any normal person a week solid. Not calling Zuck normal, but it’s hardly a 1-night deal.
i think there was a thread about this same topic on reddit,.. hmm can’t find it now
people seemed to like how hacking was portrayed in ‘war games’
and there’s also of course documentaries on actual hackers
There was this one from someone claiming to be a writer saying they do it intentionally to see who can get the worst scene on TV.
http://www.reddit.com/r/gaming/comments/f2i7t/ive_written_for_tv_shows_like_csi_and_numbers/
No idea if it’s true or not but considering how bad some of them are it’s certainly plausible.
yeah i think that was the thread
Hot off the press would be a successful (IMO the most) hacks in a film “Underground: The Julian Assange Story (2012)” All the hacks are quite accurate if not light on some details.
36:53 – Username guessing
39:00 – Social engineering
48:13 – Dictionary attack on MIL-NET account.
Well done to the technical writers.
re Firewall: I’m pretty sure those older ipods let you record audio through the input jack through a debug/test mode. I have no idea how a scan head works or what its output is like, but if you could get its output to analog somehow, you could totally record ‘something’ with the ipod.
I know the old mini’s were able to scan IR codes into audio using only a IR reciever and then transmit it through the ir immiter again. The data woud be stored as an audio file.
O’riely has a book that shows how to do this!
http://spritesmods.com/?art=lineccdts
if the scanner head is CCD, then its basicaly just an analog shift register
put in a steady clock signal, and you could record the analog output with the audio input on an ipod
would need a lot of post-processing at a desktop, but you could reconstruct the image
or he could just have used the camera on his phone :p Ok I did not see the movie so I don’t know what type of phone he have
http://nmap.org/movies/
The classic hacking portrayal has to be the magic asterisk rolling character hack.
(it kills me War Games ended on this same note…)
You start with a password: “**********” or, if they are REALLY sophisticated, a random char sequence “DY*AHE&SK” or whatever.
THEN a magical hacking program starts rolling through some alpha numeric character set until one digit is found. Then it repeats until all the chars are “found”.
*********A
*********E
********WE
*******AME
******LAME
A timing attack, maybe? [1] That would probably start the ‘uncovering’ from the front though…
[1] (don’t know the official term.. it’s when you use the response time of a badly implemented password check code that tests each letter of the entered password against the real password and stop at the exact moment when there’s a mismatch. It means that one can try words with different first chars until one of them takes longer to be rejected, then go on to the second char etc. It would produce the pattern you describe I guess…)
This is actually possible on windows 95 and 98 password protected shares. Most cracking programs actually show the progress one character at a time.
I actually DID this on a U.S. Air Force security door with a “Cypher-Lock” on it. This was in 1976. You could hear a relay click as soon as you pushed a wrong button, and it reset after about 10 seconds, when you heard the relay un-click, so you could hack the 4-digit combo in a matter of a few minutes. Again, this was a USAF facility holding documents classified “Confidential” and “Secret”.
I love that lame effect, so I built one :P
http://usedbytes.com/projects/launch_codes/
for top successful
Matrix, Trinity use nmap :)
http://www.youtube.com/watch?v=ojFFS_T3UQk 0:04
Disagree that ‘Enemy of the State’ should be included, the whole premise of the movie is that big government have computers so far advanced that they can do things that regular people couldn’t imagine they can do. Of course we regular people would think that enhancing and rotating the images isn’t possible. That’s what the author is saying that ‘they’ can do that ‘we’ can’t. I don’t think it’s in the same ball park as the others. When I saw this I started thinking ‘what kind of tech could make this possible’ like they must be rebuilding the scene in 3d from the 2d images of the camera or cameras. It didn’t irk me the way two people typing on the same keyboard did. Plus I love using that quote “zoom in, enhance” when I’m over someone’s shoulder.
Technically, it is possible to do something like this. Having cameras in known positions relating to each other, you can build a 3D model of something. Similar things have been made possible with Kinect hacks. I haven’t seen the movie, but depending on where the cameras are supposed to be located, I can see doing 3D recreations in high security areas.
I agree on rotating whole image. But how could you rotate that bag? part of it gonna be hidden by person holding it…
Hey, Decker did the same thing with a photograph in “Blade Runner”
No he zoomed into a reflection of a mirror to see something outside the view, that only requires meg-mega-resolution pictures and some very advanced processing.
“Enemy of the State” is actually based very loosely on the life of surveillance/TSCM expert Marty Kaiser.
He even did on-set technical consulting.
http://www.martykaiser.com/enemy.htm
I agree with you. Its not like they zoom in 1000x and still have a clear picture. They have a 3d reconstruction running and only rotate by like 5° and the reconstruction is not crystal clear. They even debate about what they are seeing and just assume he put something in that pocket.
While I think its not possible today, thats just part of what the movie wants us to believe is possible and way more realistic then in Blade Runner.
It’s impossible with one camera, period. You cannot rotate a 2D camera view in 3D. You need other cameras recording each angle you want to view. You can create a simulated 3D environment, but that will not give you any information about an item being dropped into a bag.
So you were wondering why they’re all portraying hacking in such unrealistic ways – I’m pretty sure its to make the show more entertaining. Realistic portrayals of hacking tend to be awfully boring. As an example, try watching “Untraceable,” a terrible horror movie with serious attempts at realistic depictions of networking, tor, and other things that totally failed to make the film more interesting.
Anyone needs xena videos ? ;D (the core…)
Not so much hacking, but generally improving the state of computers portrayed in movies: TRON Legacy. Yes, they get zapped into ‘The Grid’ but that’s the essence of the plot so it gets an automatic pass on that one. The stuff outside that was actually intentionally ‘made plausible’ by a devoted SFX guy: http://jtnimoy.net/workviewer.php?q=178 . There are some other interesting items in the writing and production design, like the name ‘iso-morphic algorithms’ (see here: http://www.science20.com/eye_brainstorm/tronlegacy_and_isomorphisms ), that bears mentioning as improving the portrayal of tech in movies.
I’m going to go against the popular opinion here.
I’ve only got a base level of knowledge when it comes to hacking, but I always take the view that this is entertainment. They don’t claim to be realistic in any way. People (except hackers and geeks, of course) don’t want to see the realistic hacking because it’s relatively mundane unless you have some knowledge of what’s actually going on at a deeper level.
Oh, and a couple of those aren’t as bad as they seem. The breadboard in The Core is because they had so little time to build the ship (I can’t remember how long exactly, but it was between 1 and 6 months from basically nothing) and in Die Hard 4.0 you see the devices remotely activated right before the keystroke blows them up (not sure why they weren’t remote detonated, but that’s another issue).
It wouldn’t surprise me if they were not remote detonated to ensure that the hacker was actually sitting at his PC when it blew up.
That would make sense. Or maybe it was done to show off the character’s flair for the dramatic.
I believe this is exactly why they’d require a keystroke. What’s the point of remote detonation if you’re just going to blow up the guys apartment while he runs downstairs to get his mail that he hasn’t collected in a week since he’s been holed up in his apartment hacking?
Though the requirement to have a specific keystroke was a little odd in my opinion, he would have totally been blown up if the bomb simply required ANY keystroke, instead it required the Escape key(I think)
I don’t see how you can point out the c4 issue, which actually makes sense, and gloss over the “I’m hooking into a power grid with my laptop and I know how this works”.
I love Enemy of the State, but that scene was the main one that always bothered me. I do like how everything portrayed in that movie though is pretty much already played out by bills like the Patriot Act.
All previous posts are really good, now for a hardware hack. Movie: Paycheck
Stuck in a subway, got a bunch of random items and uses a paperclip to force an IO card to fault the system and stop a speeding train…. the timing and the little puff of smoke ( realistic for some electrolytic caps ) should get added to the list of ‘ realistic hacks in a movie ‘. There is also the scene where a zip tie and a bullet causes a mass explosion, but that part is a bit over done.
Shredderman Rules (2007), Nolan Byrd has the best representation of a hardware Hacker for the early 2000s era I’ve ever seen in a movie ( http://youtu.be/rBi47GXVfZo?t=11m50s )
Real genius, when the guy uses a coin cut of ice cylinder from liquid nitrogen to purchase snacks in a vending machine. That’s a hack.
There’s also a classic ‘cheating at the exam with a ham radio’ scene from a old soviet comedy:
http://youtu.be/WjG-LTi0BuI?t=41m28s
That is just absolutely hilarious (english subtitles are there).
Oops, jump to 41.28, for some reason the website chewed up time from the link: www youtube com/watch?v=WjG-LTi0BuI&feature=youtu.be&t=41m28s
what the hell have you gotten me in to?
Just a funny soviet comedy dating back to 1965.
In Soviet Russia, does comedy laugh at you?
awesome
The only real world hacks I have ever seen on movies were two.
The first was in Wargames where the main character is at a old payphone
and breaks the glue on the threads of the microphone end of the receiver and hunts down a pop can pull tab and shorts the Tip to ground to start the call.
The second was in Hackers when a character uses a hand held tape recorder to play back the coin tones to make free long distance calls.
Caleb’s honest disillusionment, discouragement, despair even, was what really made this entertaining for me. I feel your pain, Bro.
Best example of hacking in mainstream media definately has to be in Matrix Reloaded when Trinity used a nmap to scan a power plants computers and discovered that they haven’t updated their ssh in 200 years or something :/ but, you know, still well done in comparison.
The exploit allows her to overwrite the root password I believe and she comes up with some leetspeek like z10n101 or soemthing.
Wasn’t the virtualised world set in the 1990’s? Therefore you’d expect 200 year old copes of software.
A teacher in PIC programming told a story about a couple of students who, after getting their breadboard setup working for a commercial project simply hot-glued the whole thing and called it finished. The thing is that the teacher told the story as if this was an achievement…
Just saying that breadboard setups may be more common in products than you thought, or feared…
Standard potting. Use non-clear compound and no-one will be the wiser (other than the oddly large package size in some cases).
What about power outs with a background voice that announces that the emergency system is starting up….. Where are the friggin’ no-break systems ?
Cannot believe Independence Day isn’t in here! Psychic aliens with three fingers and, apparently, no vocal communication fly across the universe to destroy us. While the whole of the US gov’t is busy trying to communicate with them using flashing lights, a lone MIT graduate writes a virus that *only* takes down their shield that needs to be uploaded through a physical connection to the mothership.
IMO, Live Free or Die Hard had a *decent* portrayal of hacking (anti-authoritarian hacker/cracker villian, hacker hero). Considering I have USB devices I can activate by keystroke it’s not that unplausible that a kill squad sneaks into my home when I’m away and attaches a keystroke-activated bomb, especially if the kill squad is in league with hacking geniuses. Certainly Die Hard was better than Swordfish and The Core.
They actually cut alot from that sequence which goes some way to bridge those scenes.
http://www.cracked.com/article_18720_7-famous-movie-flaws-that-were-explained-in-deleted-scenes.html
Infinite image resolution anyone? like CSI getting assassin fingerprints from screw head reflection.. and, why nobody uses a mouse? überhackers doesn’t use mouse?
actually there is many people that don’t use mouse (or barely use). I personally installed launcher on my windows, and have a key binding for running console on linux – that way i barely ever need to use mouse
“überhackers doesn’t use mouse?”
Actually no they don’t :)
If you’re properly versed in keyboard shortcuts, a mouse will only slow you down.
I cringe every time I see that pixel to text reverse gaussian animation.
In Live Free or Die Hard, another thing that gets me is when they use OnStar to start the car they stole. It shows a complete lack of understanding of how the system works. Cell phones had been shut down previous to this, and OnStar is basically a cell phone built into the car.
Come on that was some old school social network hack. and I have onstar on my company fleet car and I can remote start. unlock and lock the doors and see if they are locked or not. Since the cars PLC is tied into the on star system it can do just about every function the PLC has control over.
Get reports on the status of the car ect ect.
And with the onstar app on my phone I can do it all my self.
The only thing you can’t do is unlock the steering wheel lock.
I understand the social aspect of the hack, I was referring to the fact that cell networks had been shut down in the movie previous to this scene, hence the whole OnStar system wouldn’t work.
OnStar used to be based on analog cellular, and was separate from regular cell networks, and had a longer range. 3Watt Transmitter, etc. Of course, nowadays it uses the same network as cellphones.
So it’s not entirely implausible, given the time.
Ok so Hackers didn’t exactly have a lot of realism in it – but god damn the soundtrack is great!
The movie that poped in my mind was Iron Man 2, that court scene where he takes control over screens. Terminal output really looks like u-boot and linux prompt with custom welcome message. There are tvs with intergrated wifi and linux, so maybe, just maybe it is possible to push modified image or binary for customized boot.
Also, when he is cleaning the tip of solder iron you can hear sizzling of water. That was a nice detail :)
but you’re comfortable with the unbound holographic projections that respond to random and imprecise gestures?
The part of battle royal where that one kid hacks into the government’s base wasn’t bad, he spent a few days coding a script before attempting the hack
I always thought the Die Hard thing was that the keystroke confirms the presence of the user? I mean, you don’t want to blow his computer while he is away?
Also, you forgot to mention the fact that the IP shown in Skyfall has octets larger than 255.
the die hard thing is a good point I guess. Maybe that one shouldn’t have been on the list!
There is plenty of stuff to pick at in that movie, i seem to remember some “evolving crypto”, the execution of whole “fire sale” concept, not to mention the fact that the computer bombs have external indicator leds. One might also question the fact that none of the “hackers” ever opened the computers? (don’t turn it on, take it apart!)
I’ve thought about this some more and I’ve reconsidered it at a higher level. I probably missed the “conspiracy to use flu vaccines to make people shop more at Xmas” aspect. The whole idea is needlessly complicated, but not unfeasible.
The kill squad, presumably to evade detection by their victim, local Police, and (I guess) assure the victim’s demise, breaks into houses and plants C-4 on the computers? When the mob assassinates someone with a car bomb, they do it to send a message and get noticed. If you can hijack comms to an F-35B, why not just call in an airstrike?
I still like the flick for the crystallization of reluctant heroes, portrayal of government’s role in the (dys)function of society, and the accurate depiction of hackers as both heroes (mischievous do-gooders) and villains (malfeasant genius).
That used to really drive me crazy. But I have come to the conclusion that if they used a real IP address the server at that address would be pounded into scrap in just a few hours.
I think they are just doing it to keep from getting sued if that address links to some real server, that then gets hacked because of the address showing up in a movie.
it’s a wonder that movie IPs aren’t all 555.1212.555.1212 or some variation on the classic telephone 555 local exchange that still shows up in movies and TV shows…
There is plenty of dead space and special blocks in ipv4, if that really was the worry
(127.0.0.0/8 block, anyone?). They could also have given an IP they themselves owned, and put up some arg-like puzzle accessible over ssh, or something to that effect.
John Cleese is not dead! Q changed because, um… Actually, I’m not totally sure. I guess because Daniel Craig’s bond is a reboot. But the old Q is very much alive.
in my mind, Q will always be Desmond Lewellen. Cleese did fine I guess, at least he had gadgets.
Yes. Desmond Llewelyn was the one and only Q. Of course, the new guy fits a real Q’s job description somewhat better. Q being short for Quartermaster. Yeah, he’s the guy in stores who issues your standard kit, not head of a scientific research team.
Didn’t Cleese’s Q character get killed? I vaguely recall something like that in on of the recent movies. Cleese is still around, but the old Q had to be replaced.
Shockingly enough Trinity’s Hack from Matrix Reloaded, when she hacks into the the power station to shutdown the grid. Had Cred…
http://camworld.org/archives/001066.html
Anti-trust seemed fairly realistic, if I am remembering right. At least compared to these it was.
http://www.imdb.com/title/tt0218817/
Anti-trust is basically all the bogus claims about how Microsoft “steals everyone’s code” and about “GPL code in Windows that Microsoft refuses to acknowledge” taken to its logical extreme.
IIRC there’s a bit with reprogramming satellites where the “code” on the screen is a Windows 98 Win.ini. Of course this is complete crap. If you want to disable a satellite network you should be installing Win ME.
OK so how many people hate it in movies and TV when someone is unable to trace where a phone call came from because the caller was not on the line long enough?
Yes. That’s so stupid. It dates back to the time when phone calls were connected using hideously complex arrays of mechanical switches. With computer technology and address databases it’s possible to pretty much instantly tell where a landline call originates. With cell phones it’s possible to triangulate the location from the three closest towers using signal propagation delay. That’s an always on function for assisted GPS on phones for locating the phone when an emergency call is placed. Even if the phone has been hacked to disable 911 location data, the triangulation function is always there, which can be used to locate any cell phone making a non-emergency call.
It’s high time the entertainment industry dumps that stupid and obsolete trope. So what if the perp bought a prepaid phone with cash, made one call then took the battery out and dropped the phone in a homeless person’s burn barrel. He made a phone call and the telco knows within 100 feet where that call originated.
That’s a good bit in Enemy of the State, they get found because Smith’s character made a phone call, none of that “He wasn’t on long enough to trace.” He made the call and his location was known in seconds.
@Galane
“That’s a good bit in Enemy of the State, they get found because Smith’s character made a phone call, none of that “He wasn’t on long enough to trace.” He made the call and his location was known in seconds.”
There’s a very good reason you haven’t seen another movie portray an accurate account of phone tracing like was done in ENEMY OF THE STATE and it’s called the Federal Government. I know some will think this sounds like conspiracy theory but keep in mind that back in 1988 any mention of the Federal Government spying on all American citizens would be called crazy conspiracy theory and yet thanks to Snowden we know today that the Feds have been doing just that and that the heads of the agencies lied about the spying not only to the people but to Congress.
The average American perceives TV as being real in the sense that while the stories and characters aren’t real and the special effects are fake, everything else is real except of course when you’re dealing with science fiction and a futuristic society. For example the CSI series (pick any one) is perceived by the viewing public as featuring real analysis and techniques for solving crimes. Even though its fiction they believe that everything thing the CSI actors do is based on reality. Thus the phone trace as having to take X number of minutes or seconds comes from the Feds wanting push this to the public. The Federal Government wants Hollywood to propagate the BS that a phone trace is not something that can be done instantly. Why would they care about this? If everyone realized that a phone trace could be done immediately just imagine how many out there would take greater caution/care when making phone calls. If you are trying to make a call that can’t be traced to you or your location and you believe that the Feds need a minimal amount of time to do the trace then you have the false sense of security that as long as your call is quick your OK.
The phone trace is just one example of many where the Federal; government uses Hollywood and TV to push ideas onto the public in a way that they sink in at a subconscious level. AS IT/hackers we have a greater understanding of computing and networking technologies then the general public and thus we know how ridiculous much of this is but what about other areas in movies & TV that are BS propaganda? What other non-technology based ideas are pushed that we don’t pick up on because they are ion a field that we don’t specialize in like psychology; specifically group psychology? Did you know that the psychoo9gy of the group differs from the individual and so you can get people to do and act in ways within a group that they would never do when acting alone? Take the example of the lone hero angel were the protagonist defeats the antagonists (the villain) by themselves against unsurmountable odds to save everyone. This is an incredibly ridiculous notion that a single person no matter who they are will save everyone. In reality victories come from the acts and deeds of many working together. In the real world the only way to defeat the villain would be for the masses to work together.
How is this lone wolf hero scenario propaganda? It subconsciously conditions the public to believe that when in a time of need there will be one man or woman who rises up and saves us all and that’s just not what happens in real life. So long as the public believes the lone wolf hero scenario is viable they will continue to sit back waiting for their hero to rise up instead of taking action themselves to make the change.
Wow, that just cured my sleepy-headedness !
I’m down in the realm of comments that probably won’t get read, but this reminded me of:
https://www.youtube.com/watch?v=3aipwDzC2hw
Real hacking is a long, tedious, unglamorous process. When people ask me with a straight face if I’ll hack something/someone for them, I have to seriously consider whether I should dick punch them or not. Firstly, I’d call myself a white hat. Secondly, the more I’ve learned about real hacking over the years(and not cracking or using someone’s published exploit), the less I consider myself a “hacker”. I have a basic understanding of ASM, overflows, NOP slides, etc, but having a real job AND being I’m old enough to go to federal ass rape prison, the motivation just isn’t there anymore.
Awesome, was just thinking about Swordfish, lol
Don’t stop here, though, do more!
Still no reference to “Takedown” ? My last comment about this movie was nowhere to be found. I’m wondering what is sketchy in that one, besides the historical accuracy. ^_^?
Number 2 is real, not a fail. Just look up photosynth.
“INTERNET SPIEK”: Plausible. Back in the 90s/early 00s Windows 9x machines could be booted off the internet (really, BSOD’d) with a malformed OOB packet. ICQ+reveal IP tweak were the best of times back then. http://en.wikipedia.org/wiki/WinNuke
National Treasure features a Linksys WRT54G being used to hack a security system. It’s pretty cool, since this device was used in many hacks, and can also be used as a penetraton-test-device ;)
From memory ‘Foolproof’ was pretty good though I haven’t seen it in a few years and I may be looking back on it with fond memories.