We love seeing hard-core firmware reverse engineering projects, but the number of hackers who can pull those off is relatively small. It’s possible to grow the ranks of the hacker elite though. A hackerspace is a great place to have a little challenge like this one. [Nicolas Oberli] put together a capture the flag game that requires the contestants to reverse engineer Teensy 3.0 firmware.
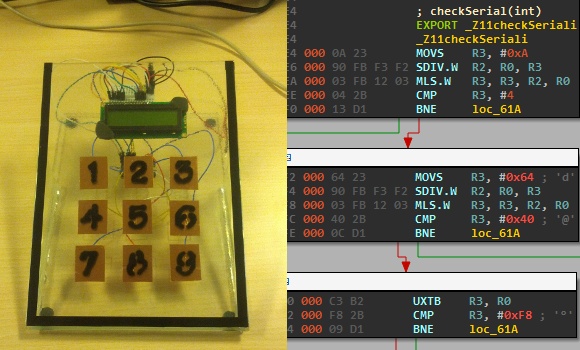
He developed this piece of hardware for the Insomni’hack 2013 event. It uses the Teensy 3.0 capacitive touch capabilities to form a nine-digit keypad with a character LCD screen for feedback. When the correct code is entered the screen will display instructions on how to retrieve the ‘flag’.
To the right you can see the disassembly of the .elf file generated by the Arduino IDE. This is what [Nicolas] gave to the contestants, which gets them past the barrier of figuring out how to dump the code from the chip itself. But it does get them thinking in assembly and eventually leads to figuring out what the secret code is for the device. This may be just enough of a shove in the right direction that one needs to get elbow deep into picking apart embedded hardware as a hobby.
Continue reading “Reverse Engineering Challenge Starts Off Simple”