[Craig Heffner] recently found himself on the case of the Linksys WRT120N router. The router’s firmware was using some previously unknown form of obfuscation, causing headaches for those wishing to run their own software. The WRT120N, being a 2009 model is somewhat out of date at this point. That didn’t stop [Craig] though, as he dove into reverse engineering the firmware obfuscation.
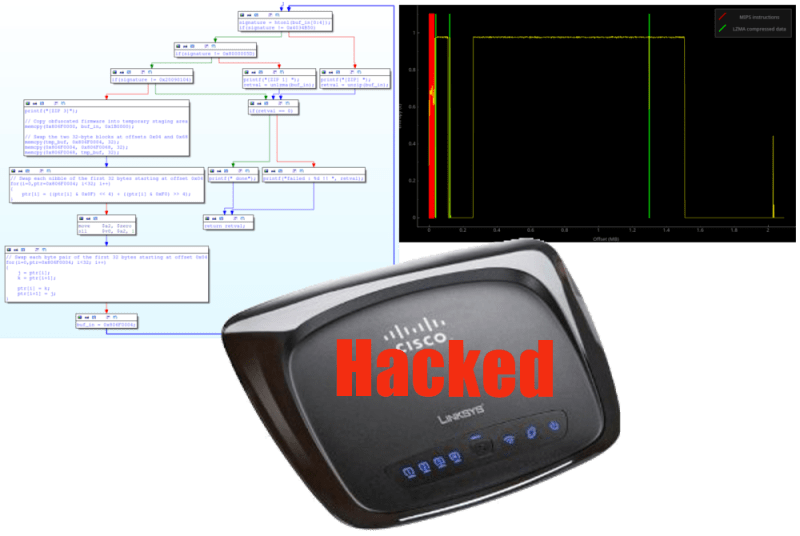
[Craig] started by running the firmware through his own Binwalk tool. Binwalk analyzes firmware files for known data, be it embedded filesystems, raw compression streams, or binary files. In this case Binwalk only found a small LZMA block which contained the compressed html files for the router’s web interface. The rest of the firmware was unknown data with a high level of entropy. [Craig] couldn’t do anything more with the firmware update file alone, so he ordered a router to attack from the hardware side. Inside he found typical low-end router components: An Atheros AR7240 SoC, a 2MB SPI flash chip, 32MB of RAM. He also found serial and JTAG headers.
[Craig] connected to the serial port and was greeted with a boot menu. This allowed him to run some commands on the router, but didn’t give him any way to dump memory. He had to go straight to the source – connecting directly to the router’s SPI flash with an FTDI C232HM cable. Using libmpsse, another of his open source tools, [Craig] was able to dump the flash. He now had the un-obfuscated bootloader code, albeit in MIPS assembly. [Craig] was then able to go after the bootloader with IDA Pro. After a bit of work, the obfuscation system was exposed. The system was simple – several byte and nibble swaps had been performed between the LZMA header block and the first few bytes of data. [Craig] finished out this part of his hack by writing a simple C program to de-obfuscate and decompress the firmware.















Reverse engineering obfuscated stuff is very cool. But forgive me for my lack of knowledge, what can you do with a hacked router?
Other routers have been hacked before, DAGS (Do A Google Search) on WRT54g hack. For instance, you can turn a wireless router into a WIFI extender, or into a TNC for Amateur Radio.
Also DAGS DD-WRT
Yeah, I have this router, and it’s running DDWRT… is this news?
How? It’s listed as a known incompatible device. http://www.dd-wrt.ca/wiki/index.php/Known_incompatible_devices
Yeah I have one that looks just like this, i need to check the model
how did you manage to do that @dj_doughy… Assist me
what did you use
Are you sure it’s a wrt120n
DADDGS (Do a Duck Duck Go Search)
I used a wrt150n with a custom firmware made by ddwrt and now i have a wifi repeater.
totaly awsome. easy as updating a bios.
pero usaste rauter WRT120N con un firmware WRT150N de dd-wrt?
If you know how the firmware update obfuscation works you can create and flash your own (modified) firmware just from the web GUI of the original firmware as “update”. If it is possible to let own code run on the device it is possible to re-purpose it for all kinds of stuff. This router has only 2MB flash, so I dont think openWRT will run on it, but the reasons for running “own” software on a router instead of the sw of the manufacturer are the same for every router.
2MB is too small for OpenWRT unless you do some serious pruning and then it still may not fit. But since this router has 32MB, it might be worth trying some of the other work arounds like replacing the 2MB flash with a pin compatible 4MB flash, use a couple GPIO lines to add a bit bang interface to a larger SPI flash, or possibly load OpenWRT off a USB flash drive if the router has USB. I have an old Netgear router I’ve considered doing the USB approach with.
Craigs tools allow him/you to reverse engineer the firmware, which allows you to check it for exploits. If you find exploits you can use your new found knowledge of the firmware to fix the exploits or rewrite the entire firmware image such as has been done with ddwrt. In other words, make that router your bitch! :-)
You can remove some of the software-based NSA backdoors,
But not all, and not the hardware ones.
You can replace the stock firmware and install OpenWRT as example, if the router has enough memory/flash. With that, you can extend the functionality of the router, say run a VPN, access its GPIO / serial ports / i2c / etc.
https://openwrt.org/
So, is this just Cisco being Cisco, or is there some reason that I’m missing for obfuscating the router firmware like that? It’s far weaker than a cryptographic signature check in the bootloader if you, for some ghastly reason, want to forbid 3rd party firmware; but I’m hard pressed to think of anything worth hiding in the firmware for a basic plastic-box home router.
Cisco doesn’t care about people loading their own firmware. They still push product out the door. They do care about security on their devices though. Don’t want a reputation loss when someone finds an exploit that puts millions of home networks at risk.
Cisco didn’t care about their own firmware. Stock firmware for the WRT120N (I have one) is crash prone and bug-ridden.
Every ‘Linksys by Cisco’ isn’t worth more than the box they come in. Reason #255 I’m still using my WRT54G v4.
He takes it a bit further patching the bootloader and OS to re-enable JTAG with OpenOCD.
http://www.devttys0.com/2014/02/re-enabling-jtag-and-debugging-the-wrt120n/
DD-WRT has been available on this router for 3 years now, so I don’t think the initial part of this story is correct. However this was an interesting way of being able to retrieve an unobfuscated copy of the original firmware.
No it’s not available for this model according to dd-wrt website.
Whats with all these people having copies of IDA Pro?
Rich people :P
I love the irony of the fact that IDA Pro’s copy protection was most likely cracked using IDA Pro. :P
Ida knew when you tried to open the Ida executable in itself and gave you a popup saying something along the lines of they know they can’t stop you, but you should feel bad.
The guy wrote binwalk, hes not interested in putting alt FW on it, or saying that this “hack” enables that:
“It was recently brought to my attention that the firmware updates for the Linksys WRT120N were employing some unknown obfuscation. I thought this sounded interesting and decided to take a look.”