Have you ever been looking for a screwdriver, USB stick, or your keys, only to find them right where you left them in plain sight? We have. As many prolific geocachers know, hiding things out in the open is a great way to make sure that people overlook them.
[Jacob Strieb] has been researching various ways to password protect and hide browser bookmarks in plain sight. He calls his latest technique “Bookmark Knocking” and he’s made a demonstration available on his Github account.
Why hide bookmarks to begin with? A browser’s bookmark collection can give away the habits, interests, and needs of the person who put them there. Bookmarks to gifts, domestic abuse support websites, and other private destinations might be best kept away from prying eyes.
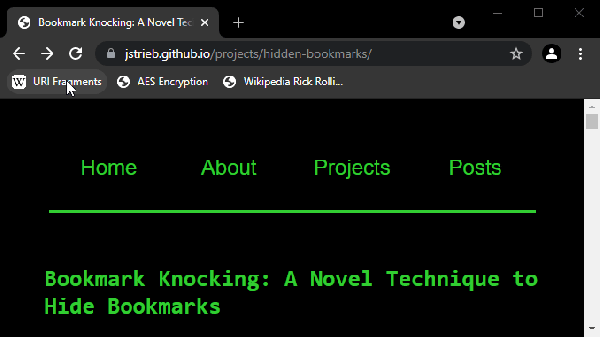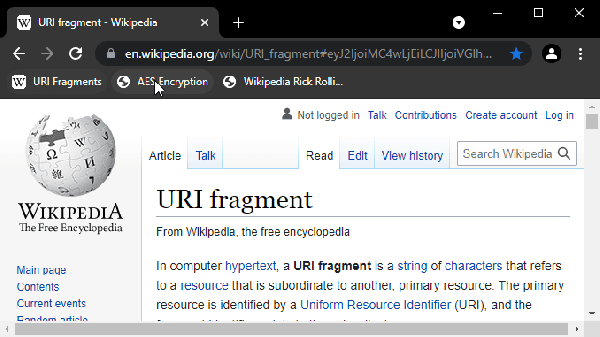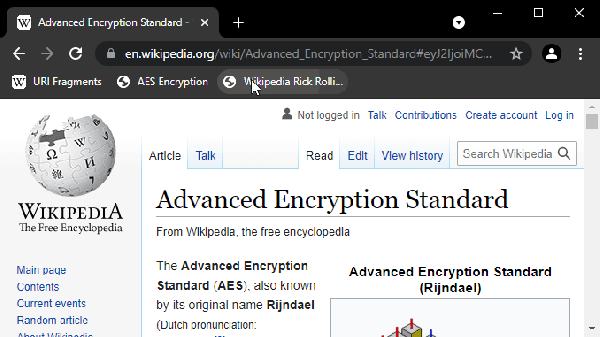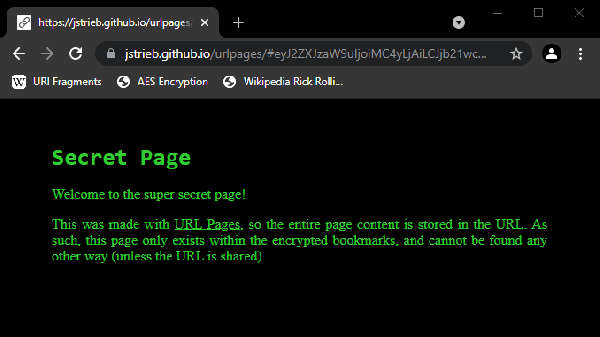
Inspired by port knocking — opening connections to specific network ports in sequence to gain access through a firewall — bookmark knocking requires clicking bookmarks in a specific order to open a link. When the bookmarks are accessed in the proper order, the third bookmark reveals a hidden site. It’s not only a novel approach to hiding things in plain sight, it’s very cool to use!
We especially appreciate [Jacob]’s motivation: Helping those who are vulnerable to protect themselves in any way possible. It’s a solid reminder that technology can be elevated to a higher stature when put to a noble use. Be sure to check out the demonstration so you can try it for yourself!
If camouflaging data flips your bits, you may want to look at a neat way to embed data right into bash scripts, or conceal a WiFi enabled microcontroller in a USB cable. Do you have your own favorite “hidden in plain sight” hack? Be sure to let us know through the Tip Line.