[Dark Purple] recently heard a story about how someone stole a flash drive from a passenger on the subway. The thief plugged the flash drive into his computer and discovered that instead of containing any valuable data, it completely fried his computer. The fake flash drive apparently contained circuitry designed to break whatever computer it was plugged into. Since the concept sounded pretty amazing, [Dark Purple] set out to make his own computer-frying USB drive.
While any electrical port on a computer is a great entry point for potentially hazardous signals, USB is pretty well protected. If you short power and ground together, the port simply shuts off. Pass through a few kV of static electricity and TVS diodes safely shunt the power. Feed in an RF signal and the inline filtering beads dissipate most of the energy.
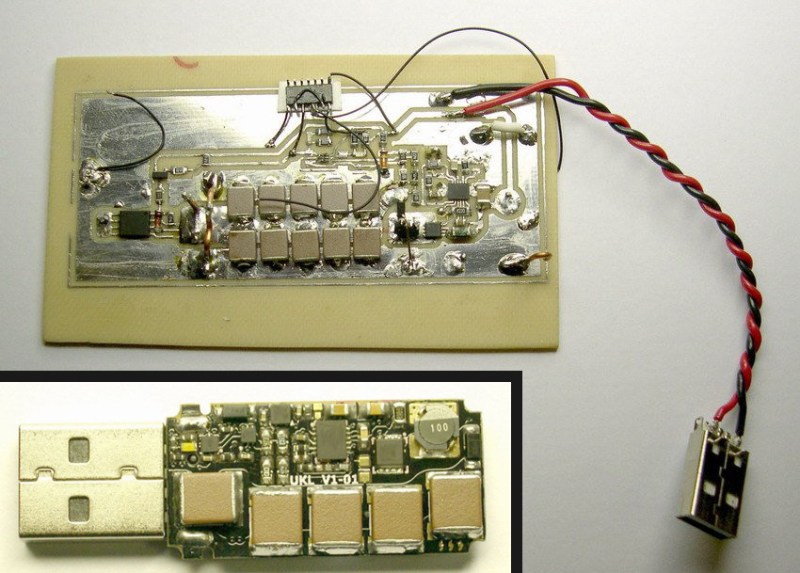
To get around or break through these protections, [Dark Purple]’s design uses an inverting DC-DC converter. The converter takes power from the USB port to charge a capacitor bank up to -110VDC. After the caps are charged, the converter shuts down and a transistor shunts the capacitor voltage to the data pins of the port. Once the caps are discharged, the supply fires back up and the cycle repeats until the computer is fried (typically as long as bus voltage is present). The combination of high voltage and high current is enough to defeat the small TVS diodes on the bus lines and successfully fry some sensitive components—and often the CPU. USB is typically integrated with the CPU in most modern laptops, which makes this attack very effective.
Thanks for the tip, [Pinner].














Which means you can make a USB stick with an autoplay video that will literally self destruct 5 seconds after viewing ^_^
“self” destruct ;)
Actually that’s a great idea. You could have a secret block in the device that activates the mechanism. If someone just straight copies the whole device, it will fry itself and the device used to do the reading, but if you know what you’re doing, you can just use the stick regularly ;-).
In particular, you could have a (long) video file that says “Remove this stick now, and you won’t face the consequences.” with the last block activating the mechanism..
This is completely diabolical! I love it! The best thing would be for TSA, customs or some other gov’t asshats to decide to Fsck with your data and plug your drive into their computer to dump it. PWNED!
You stand a very real chance of turning that customs check into arrest on federal charges. The government looks poorly on destroying data to prevent it being searched, and even more poorly on destroying their equipment.
Logically the fault would be theirs, but logic and federal are two mutually exclusive terms.
That’s a decent point. I’d just politely suggest that they don’t plug the USB device into anything as it could damage their equipment. That would bring up more questions, but at least I wouldn’t be involved in willfully damaging TSA computers (either way, you’re not going anywhere for a good long while).
Speaking of TSA though, airplanes have USB drives for charging, and apparently they have data pins because many flyers have complained that when plugging in e-readers, the plane mounts them as USB drives (meaning they can’t continue reading while charging) instead of just providing power.
Now I know these USB jacks are totally separate from flight controls (HOPEFULLY in all cases!), but there would be much unhappiness if the entire in-flight entertainment system was fried.
On a related note, every once in a while, security auditors will scatter a few USB sticks in the parking lot outside of secure buildings to see who plugs the USB sticks into secure machines. Bricking their computers would help to drive home the lesson!
The government looking poorly on “destroying data to prevent it being searched” is just further evidence of them being corrupt. There is nothing anywhere that saya they have a right to unencrypted, uncorrupted, and undestroyed data. If it was incorporated as a general safety mechanism against anyone trying to steal your data it would hardly be your problem if they failed to access it properly in such a way as to not destroy it.
You could always design it some fashion so that it will eventually overheat and catch fire or destroy the data. Heck,if you just made a way to flash melt the silicon… Just make it require some sort of authentication to get at the data and cause failed authentication to corrupt the data/irreversibly destroy the drive electronics etc.
But, you haven’t destroyed dick. It’s on them for plugging your private property into their (probably most unclean Windows-based) computer.
I’m quite certain this could never be manufactured and sold. It breaks FCC laws and therefore could never be sold to public.
I’d really like to leave one for the jerks who go through my luggage and help themselves to the contents. Maybe label it, “Danger, hot pr0n”
That would interact in a funny way with antivirus file scanning, os file indexing, or even disk prefetching.
I still wouldnt consider it safe since yo could just record the screen with a camera.
also i dont see the point of frying the pc that was used to play the message instead of the medium the message was recorded on
also once people are aware of this they could add extra protection to thir usb drives
And now you know why you never plug in a USB drive you found laying on the ground.
you give it to some one else and let them take the risk for you. ( on their machine of course.)
Yep. The old “does this milk taste funny to you” trick.
“Never do this at home. Do it at your neighbor’s house.”
Do it at Best Buy
Always wear a jimmy hat on your dongle ;) You’ll wind up with Willy Lump Lump.
That’s silly. The probability of a drive you pick up on the ground being dangerous is extremely small, probably less risky than driving to work.
You do realize that leaving drives laying around in parking lots and the like is a standard method for pentesters to gain access into networks right?
It’s a matter of trust, and you’re breaking the physical trust boundary. I have no reason to trust that thumb drive and I have no reason to feel that anything on that drive could be considered safe for consumption. Why you would blindly trust some random device you know nothing about and shove it into your computer is beyond me.
Do you have unprotected sex with random people you know nothing about? Because USB sticks might as well called virtual STD sticks.
New name for USB flash drive invented: STD drive. Well done
Maybe that should be DTD drive – Digitally Transferred Disease/Disaster/… drive.
“Stupidly Transmitted Data”
Protect you self! http://int3.cc/products/usbcondoms
STD = “Soon: Total Destruction”!?
Someone hasn’t gone to college in the last decade. Flash drives are like pens, people forget them everywhere. Get some help for your anxiety problem.
I can’t imagine ever feeling the desire to even bother looking at the contents of an unknown flash drive. Why would people? Just to be nosey? Hoping for nude pics? *shrug*
It wouldn’t even peak my interest.
In school or Uni it would be to find out who stupidly left their drive with important work behind
its called “drop fishing”
Good time to follow Dave Jones’ advice: “Don’t turn it on, take it apaaaat!”
I heard of a bank being compromised by someone leaving a basket full of free USB sticks with the Bank’s logo on them in the lobby (before Microsoft disabled the autorun feature) . It is amazing how many layers of security can be bypassed by “free”.
It would still work today with BADUSB the device emulates a keyboard, and boom instant trust. Human input devices are trusted by computers by default.
You open it first. I always crack the case on random abandoned flash drives.
Sorry, not all of us can see the installed firmware by looking at the PCB.
you don’t decap all your IC’s and inspect the silicon? Serious security flaw there mate, bet you’re PC is a breading ground for viruses…
topkek
The thing is bristling with capacitors. A normal flash drive has very few components besides a large flash memory IC or two. A bit more than just firmware going on here.
A dead giveaway that something is up is the fact that it’s bristling with capacitors and power circuitry. A normal flash drive will have very few components besides a large flash IC or two. There’s a bit more than just firmware going on here.
Nothing good will come of this. Take out all usb ports on my computers. =)
Apple engineers are way ahead of you. Maybe this explains the new Macbook’s lack of USB…it’s not a bug it’s a feature!
Technically, it does have a single USB3c port on it.. which from my reading of the pinut includes the equivalent of two usb3a ports (and thus, 2 normal USB ports). Just buy the matching hub for 79.99 from the apple store. :)
80$ for a hub? That is robbery.
But it has an Apple on it!
It’s also a graphics card; it has an HDMI port as well as USB3A and 3.1C
Or get the Asus ux305, which is thinner, has better battery life, aluminum unibody, three USB 3.0 ports, an SD card reader and microHDMI… With all other specs being equal (or better, in the case of the touchpad, keyboard membrane, grade of the aluminum used, rating of the SSD… etc. )…
For half the price.
And then hackintosh it.
And then kill yourself because all Apple-designed OS are pure dogshit.
@ AppleSucksDick oh! that must be why only apple cpu’s are used in all major professional movie & music environments… because MS-designed OS’ aren’t pure dog shit!
makes sense! : /
need to make with a micro to have a password protected usb
I worked as a lab assistant at my school. One thing we did as standard operating procedure was plug found USB keys in and check their contents (Yeah not the greatest security but we regularly wiped/reinstalled these PCs) and see if we can find the owner. So unless you have a warning this sounds like a real liability move.
Not unless it has, consent written on it. Plugging in someone elses flash drive is like opening someone diary. Just put it in the lost and found and if no ne comes by chuck it in the waste bin after three months.
law doesn’t require You to check for content and return it so it is Your call to do that, if it is Your call it is Your problem if something goes wrong
it could be a liability if it were stuffed with something that might be harmful to anyone that finds it, but I very much doubt that anyone could win with “It damaged our PC while we were browsing it’s content instead putting it to lost and found” scenario
There’s no reasonable expectation on your part that it will function for a particular purpose… you didn’t order it, pay for it, or come by it in any context where it was warranted for any given suitability. If you pick it up, assume it’s a flash drive, and plug it into a USB port… well that’s on you, bro.
I believe the lawyer-ly term is “tough nooggies”.
You have the right to a silent attorney, if you can not afford one….
No schematics == CSB, just like the USB in the urban legend they tell.
Blasting cap?
Something similar was done by an angry hacker when confronted with an “unhackable” CVS camera. For those who don’t know, CVS once sold super cheap “disposable” digital cameras. Initially, they used USB on a strange connector with a protocol that was quickly reverse engineered. Later, they used some proprietary interface that wasn’t worth reverse engineering (and the camera itself was downgraded in quality!), so the frustrated hacker rewired a few of the pins to the flash cap and returned the camera “unused”. Nobody seems to know how it ended, but I’d imagine some later customer who bought the camera to use as intended ended up frustrated when CVS couldn’t get the pictures out and the workers probably were puzzled at why the machine stopped working.
You could leave this usb stick in a cvs with “5exting” in silver sharpie on the outside and shut down self print for the day…or week. Kidding of course.
Glad I got my disposable camera hacking out of the way when I did, Palm connector and all lol. I didn’t realize that they went back and uber crippled it. Kinda sad really, it was like hacker training wheels and taught folks about crippleware and basic software scouring. Glad ya brought it up, Mike.
I have the second gen of that camera laying around, the one that had an obscure pin set that was still USB on 4 of the wires. I recorded some project demos on it, and then my solder connections broke since I didn’t use any strain relief. It might have required some custom program to be run once to send some data out over USB to the camcorder; virtual machine kept me from running that crap locally.
Would it be easy to protect against this? Buffer chip? I think I saw somewhere some kind of “power” protection USB-thingie which protects the ports from high current / short circuit / voltage spikes.
Just a device between USB host and USB device.
And let’s take this further; a data protection device in same manner – for example you could list all the files but not open any before “unlocking” the device. And permanent protection to autorun.inf etc :)
Just use an old, disposable PC for that. If you keep it offline, it also thwarts any virus from getting onto a machine you actually care about.
Hmm. Disposable PC. I assume you meant to say a PC worth throwing out. I would certainly hope no PCs being produced today are at the level of disposable. We live in a strange world.
they may not be at that level, but they’re certainly marketed that way.
Use a raspberry pi.
Many microcontrollers can speak USB in software to some extent, and some of these micros are only a buck or two.
They typically start at the electrical protocols for USB, followed by USB framing and a specific protocol (serial, storage, hid, etc), followed by either linking that to an existing micro function (serial) or the app on top of everything (fat32 on storage for example)
One would think it shouldn’t be too difficult to make a microcontroller system that does the electrical USB signalling part of things and verifies all is within spec. It can then either report failures that would result in things like this, or indicate such by way of no longer functioning. I could see measuring current draw alone being useful for much more than this one attack as well.
The next step would be to speak enough of the storage protocol to check the filesystem type and possibly even read a directory listing or open a file on the device, just in case the attacking USB dongle is only triggered on such actions (which seems to be a good second step for the attackers to take in later versions trying to avoid detection)
While I agree a $35 rasp-pi falls well within “disposable” for most people, especially people trying to check for this specific attack, a sub $10 build with a PIC would be even more so while being able to do more “wierd” things at the electrical level than a normal USB host controller chip in any device serious about using USB (which some would argue the pi isn’t quite)
@Dissy (since we hit comment depth limit)
uCs that speak USB usually speak only as a USB client. The number that speak USB-OTG, and are a buck, are limited. Ones with full USB host capability are usually more expensive from my experience.
But if you know of some chips with full USB host for a buck or two, please share. I can think of some fun havok those could cause!
OTG are crippled when you compared it to EHCI etc. i.e. you won’t have that high level of hardware abstraction that you could port say the linux drive to it. Since each chip or family are done differently, you’ll have to write (or find) the code to a Mass Storage class on your own. Writing a host USB stack from scratch is easily 10X more difficult than writing a client. When you write a client, you are only doing one thing for your device and may be only ever have to talk to 3-4 host OS types. (vs all kind of buggy USB sticks out there.) Then there is a stack that handles a whole lot of USB classes.
There are a couple of interesting USB peripheral chips (requiring CPU parallel bus level interfacing) that can talk to USB as a host. FTDI FT313H is about $3 from digikey and is closer to EHCI 1.0 implementation than ST ISP1763.
There are also those $8-10 “3G” routers from China. Some of them reads USB media and can share it as an access point right out of the box. They are as disposable as they can be and you don’t have to solder or write any code. Just need a USB charger and once you configure it, it is ready to go.
(No you don’t need a 3G connection nor do they come with a 3G modem.)
I think a hub would likely offer enough protection
“Likely” isn’t good enough. I use a Surface Pro 2 at work with exactly one USB 3 port and my job involves designing, building and plugging all manner of dodgy crap into it including knock-off Arduino boards from god knows where! That port gets fried, be it sabotage or otherwise, and I’m in trouble. I can’t lug a PC around with me everywhere and while the USB hub I do use would, as you say, “likely” provide some protection I’d feel a bit better knowing I have something more reliable in place.
Well, if it sends the pulse down the data lines as it purports to do, then it would fry the hub chip since it will not have a direct connection to your computer.
If the hub has power switching (most cheap hubs do not) and the pulse is being sent down the power lines, then it is possible that you could damage your PC. There is usually a steering diode and sometimes a fuse in even the cheaper hubs, though.
It seems like a simple tester could be fashioned as a counter-measure. Plug the device into that first so it can test current draw, check for shorts, etc…
*doesn’t have power switching*
So only one computer in the universe per person where you live, bro? CL has “beater” laptops for 30 bux daily. You can get a dual core with 2 gigs to run whatever malware you want and you can even look at pictures the wife and boss hate, confess your love to boxxy, or play runescape. By far the best search engine is hotbot, so steer your browser that direction .
zener on data line?
USB already has that kind of protection. Many interface chips have zeners on board or as the summary says TVS diodes. The key here is that this circuit over-stresses those components to failure and then bad things happen.
isolated hub?
If you work at all in the EE world, you really better have one anyway.. which reminds me, order time… heh.
Good luck; optocouplers at USB3 rates are hard to come by…
Access speed isn’t necessary, protection is, and opto-isolators are fine at USB 1.0 speeds.
Analog Devices makes a few USB 2.0 isolator parts that should be beefy enough to protect from this.
An optical coupler would do the trick… especially with current limiting on the data pins.
april 1st yet to come
Brought back an old memory. Back in the glory days of clone PC building, we would routinely get super cheap mainboards that would have an intermittent failure. We would send it back to the supplier for testing and they would invariably tell us they found nothing wrong and back it would come. Only one thing to do in those circumstances, take a PC power supply, break out the 12V line and run it along the leads of the chipset.
Now it’s dead.
We called our 30 V/3 A power supply ‘testing station’. We even had a check box on our RMA forms that said ‘tested’ – which really just meant ‘fried’.
yep, some old Dell pc’s (talking Pentium 200 top of the range area) had MB’s that where very susceptible to physical stress – the ideal intermittent failure, so of course they came back again and again “no fault found”.
So we popped the processor out, added some tin foil between cpu and it’s socket, powerded up until magic smoke, removed tin foil, RMA’d
fixed
http://fiftythree.org/etherkiller
I remember threatening a CCNA class with one of those when we spent a week making normal, cross-over, and Cisco-serial-to-ethernet cables. They hadn’t heard of it (who didn’t read BOFH in those days? sheesh) so I just mentioned “120VAC over the solid colors, neutral on the striped ones. Now, can we do some real stuff?”
The poor tech teaching at the community college turned pale, the other geeks in the class fell over laughing, and the folks who had no clue previously asked for explanations.
Did the same a few times, except using a cheap stun gun.
Piezo sparker from a gas grill wired up to DB-25 connector took care of the “intermittent failure/works fine for us” Dell MBs…
“Only one thing to do in those circumstances, take a PC power supply, break out the 12V line and run it along the leads of the chipset.
Now it’s dead.”
And now you’ve committed fraud…
It’s not fraud if it’s actually broken and they refuse to repair it, now if you did that to get an upgrade; that’s fraud. But when you can’t use a tool %80 of the time, you can’t use it as a tool can you?
If ever sued, how would you prove it was “actually broken”? The determination is whatever test the manufacturer uses. So if the tests passed, you can’t prove it failed.
We used to clip a lead to the corona wire of an old laser printer. It was both effective and fun to watch.
it’d be funny if it set off some explosives at the same time. more bang for your buck.
like :D
What if there’s an good person who found it on the ground and want to return it to the owner by searching for a name in USB? Regardless, the proof of concept is already out. I’d be pissed off if my $1,000 computer is burned.
I would not plug something I found with a USB connector on it in any of my devices, regardless of how small the chance is that it would blow up my port. The chance of getting a virus or similar from something like that is too great in my opinion. If I cannot read something on the outside of the device to identify the owner, then I either leave it where it is, or make sure it ends up in a lost and found place. Be nice, but make sure you’re safe first, and an unknown USB-thing is not safe.
KR,
Theo
The college I went to would keep found USB drives in the lost and found for six months, if they were unclaimed they would put them in the free box. Anyone who needed one could grab one for free, never thought anything of it. Grabbed a few for myself, used their computer to reformat the drive. Figured I was safe, checked the boot sector for anything strange on a virtual machine on my home computer. Never realized anything like this was possible. What if the drive was configured to deliver the pulse on the 3rd or 4th time it was accessed, I’d be screwed
guess that would certainly teach you an important lesson now, wouldn’t it?
I’ve used some shoddy USB equipment on my motherboard, and it recovered. It offers 1.5A to all USB ports, and I don’t think it uses the smart charging based on resistance. The easy 12V short was fixed after a whiff of smoke and a reboot, and some bent/crushed USB plugs have caused it to fail until reboot (but no smoke.) According to the manual, it powers all the USB ports while the system is off, so it must have some nice detailed circuits.
Interested in seeing if this could fry my board. I’d gamble on it once I have a reason to upgrade the core stuff on my desktop.
What you’re talking about here is problems in *power delivery* through USB. You can defend against that pretty well, because, well, they’re just DC lines. You can put hefty protection on those.
This USB stick, though, doesn’t attack the DC lines. It attacks the *signal* lines. And those *can’t* have hefty protection. There’s just no way – they have to be high-speed, and anything that can absorb a big giant voltage spike can absorb a USB bit transition just as good.
So if I were you I wouldn’t gamble it. Protection against USB devices that offer a ton of power means nothing when talking about spikes on the signal lines.
“There’s just no way – they have to be high-speed, and anything that can absorb a big giant voltage spike can absorb a USB bit transition just as good.”
SATA lines use series caps to allow the high speed data through but block any short/DC bias. Also the caps are a relatively small value 0.1uF I think, so a high voltage spike would start to cause a differential more quickly than a larger value like 47uF and simply charge the cap up. Though if the cap can survive this voltage is another issue..
Series resistors and clamping diodes are more intended for this but most all USB data-lines have a relatively low resistance chosen if any on the host side. It’s probably more common to see the 10Ω-100Ω on the peripheral side of things.
USB never really thought beyond ‘protection from ESD’, it doesn’t mean that protection can’t/doesn’t exist.
>> USB is typically integrated with the CPU in most modern laptops, which makes this attack very effective.
Aren’t USB ports usually handled by a southbridge chip or Platform Controller Hub?
Yes, they are. Not one smartphones, but on PCs, they certainly are. Generally, PHYs for interfaces are not very popular amongs CPU manufacturers, as you often can’t use the same process for both the incredibly high-speed, low-current, small-charge transistors in a CPU and the current-bearing, high-voltage lines of a external interconnect.
Not in most modern laptops..
This USB bar does work well if connected to the computer directly but what if someone does use a USB hub? Will the high voltage pass into the computer or just fry the hub and that’s it. I would assume only the hub is fried.
I think in this case it depends entirely on the hub you chose, results will vary from design to design.
I think also sending some power down the D+/- ports will cause even more damage!
That’s exactly what this does…
No it pulses a negative potential down the power line not the data lines
” After the caps are charged, the converter shuts down and a transistor shunts the capacitor voltage to the data pins of the port”
Well, the prototype in the picture above certainly can’t since the data pins are not connected. Impossible to see what traces are connected in the finished device.
It’s called “prototyping” and “proof of concept” :)
sounds like an usb hub save’s you computer in this case.
It’s not cool to break other peoples stuff on purpose. While in this case it is debatable who broke what, devices that break stuff on purpose are a no-go.
Besides, it is against the law in some (most?) countries.
No it’s not. Any police officer you reported this to would tell you that you are a fool for plugging in a found USB drive. In the US at least its not illegal to do anything unless that specific act is stated as illegal in the laws themselves. Assuming that general douchebagery is illegal anywhere and that everyone is going to be nice because of potential laws is a mistake in and of itself. Its this assumption that causes people to be surprised when drug dealers still sell drugs and people still murder people dispite both acts being illegal. People will always do bad things sometimes in every conceivable situation regardless of the consequences. Bottom line stop plugging in any old USB drive!
Well, that’s not true. For example, you can get sued for harming someone by willfully accepting that this is likely to happen. The classical example is that it’s not illegal to have a power-grid connected fence around your garden, but since you know someone is stealing your apples, you’re willfully accepting that someone will get a potentially lethal shock.
Not much different for property — You can set up a “no parking” sign, but you can’t have hidden spikes that will kill your neighbours tires. There’s a difference between being free to do whathever you want and willfully dealing damage.
That depends entirely on the intended usage. And possessing somebody else’s property without permission and using it without asking first would discount any liability. It would be as simple as claiming the device is for your own personal electronics only becuase you fear the data within could be harmful to you if released publicly or used for black mail. If you put a sticker on that says please use me, then yeah it would be your fault. But just finding this thing in say, a parking lot, does not give you consent from the owner to use it, thus you’re still liable for your own stupidity.
This could actually be considered a booby trap, which is illegal.
That’s the response I got after having my car broken into, when I asked about putting a carpet glue+spikestrip and quikclot under my doorhandle. “No they shouldn’t be trying your handles to begin with, but you still can’t do that”
Lame.
The words you need to look up are “Attractive Nuisance”. “The doctrine of attractive nuisance is premised on the belief that one who maintains a dangerous condition which is likely to attract children on their property is under a duty to post a warning or take affirmative action to protect children from the dangers of that attraction. It imposes a duty to be sensitive to potentially dangerous conditions which are likely to attract children.”
Now, it doesn’t normally apply to adults, but it can. And arguing that a USB drive laying on the ground is not an attractive nuisance would be very hard. A kid picks it up and the maker is definitely across the line. An adult picks one up that doesn’t have a “Warning: High Voltage! DO NOT USE” sticker could probably make a valid claim as well. Especially if the USB trident was anywhere on the device.
And then you’ve got the gigantic problem of using the trademark without conforming to USB safety…
Why does this make me think about FTDI :-S
\
Because they would have had they only thought about it first….along with an appropriate disclaimer buried several pages deep into their EULA for the benefit of anyone wearing a pacemaker…..
Why should I want to destroy something on purpose?
Maybe I missed a point, but stepping back a bit, the question is: What do we want to happen, when a USB drive gets lost?
I can only speak for me, but: I’d like to have it going back to the owner without any private/secret content revealed to finder. (And I mean that no matter if I’m the finder or the owner).
Hope I miss no point, but: An encrypted partition for the content (about 99% of the drive space) and an unencrypted (text file) to find contact information of the owner.
Maybe in tow steps, contact information printed on the outside of the stick “Pleasecontact …) and the textfile “truely please contact me, exept from wiping the drive and use it, there is nothing in for you (no secrets no porn no whatever). And, NO of course this is NOT the only place these data exists.”
The point you are missing is this is only meant to be a proof of concept, not a device the creator intends to manufacture and sell. Thus no files or schematics available for the layman to build his own. If your skilled with electrical engineering then you could figure it out for your self like the this guy did. Its simply a case of “can it be done?”.
Oh yeah? Then why did he write “Would you buy such «device»? yes no” at the bottom of the page?
Maybe as a countermeasure against hacking devices in public USB charging outlets?
inspector gadget would be proud!
PS: its the stick itself thats supposed to go…
but it’s the same circuit…
no password?
you can have data, but in pieces and smoke particles!
does your computer have a smoke socket? lolz
I wonder if this would affect the new Type-C connector as it is rated for higher power capacity (100 watts)?
Probably. The attack is on the signal lines. What comes in via the power lines is irrelevant other than this device potentially charging faster.
It would go great with this https://www.youtube.com/watch?v=WqR_zYJ-Uis
This idea is really really old. In fact, BOFH may have invented this – though in his case it was a fake SCSI hard drive which utilized several 12V lead acid batteries and caused laptops to run in fire.
Sounds bulky
You sir, you made my day!
Or this old classic from the BBS era
http://cd.textfiles.com/group42/PHREAK/BOXES/BLOTTO.HTM
jesus, I haven’t read that article in years!
I prefer an auto run program that writes random garbage to the bios Flash, and honestly all you need to do is write F000 F00F at the beginning of the FLASH and the computer will never do anything until someone rewrites the Bios flash via Jtag.
You mean end of the flash? I thought PC BIOS had a JMP at the very end to the real BIOS start
Yes, of course officer, feel free to search my USB stick.
A new take on the Etherkiller. Good times.
Schematic or it didn’t happen!
The USB connection has usually sequential capacitors. Therefore, Such a mock flash stick could not destroy the device if these capacitors have the sufficient breakdown voltage.
Lots of comments about the (lack of) morality in designing something meant to trash the ‘victims’ hardware.
I would like to direct these commenters to the first sentence of the write up ‘someone stole a flash drive from another passenger on the subway’. Might not want to question the morality of malicious hardware design targeting curious thieves.
I’d like to see this idea expanded to include some form of micro-switch to select data-mode and kill mode. Or something automatic like a key-file stored somewhere in the filesystem of an authorized PC… if the usb drive gets plugged into a compter without the key file then it switches modes.
Reminds me of a line from Hitchhikers about Arthur not being dangerous until backed into a corner, then he goes to pieces so fast that people get hurt by the shrapnel.
I’m going to +1 my own post for the Hitchhikers refrence.
…I’ve always liked that quote, probably second only to the one about Ford staring into the sky like a rabbit trying to get run over by a car. Arthurs rant about the only question that matters deserves mention, and Trillians rant when she… oh hell, the entire body of work deserves mention… I mean how do I not quote the bowl of petunias?
how does this mechanism to activate the main mosfet at -107V and off at -7V to charge the capacitors again work? I can see a pnp transistor (2D) and a (zener?) diode in this picture.
I still wonder if the voltage was stepped up to over 100kV it might be just as effective. Some sort of small resonant transformer could cause some internal arcing and be able to defeat the protection circuits that way. The a-d route rather than plain bruit force like a couple of photo flash capasitors in a usb hub. Disposable cameras only requiring 1.5v to charge. (but charging faster with more) although that would make for an interesting delay, especially if leakage was kept to a minimum.
All in all I wouldn’t want it to happen to my pc but that’s what I have a junk box and a tool set for. Swap it’s case and hand it back. I would say plug it into a hub first but what if someone asked it to interrogate the device first. Perhaps look for a key. (so the real user would be safe to plug and play)
My guess is this device would feel somewhat heavier than a standard usb stick.
I’m sure this device seems familiar. Perhaps I saw it in an nas catalog somewhere.
I prefer the good old days – Does anyone besides me remember the “Little Jiffy Fuse Blower”?
Resistor [for current limting], diode and 200V cap that charges off the AC line.
Optional pilot light to show that it is plugged in.
A power relay [contactor] with it’s N.O. terminals wired across the AC line, and a push button to connect the contactor to the cap.
Lastly, a label on the button saying “Do Not Push”.
Human nature being what it is …..
I, too, am curious about methods to protect myself from such an attack…
Afterthought – I’d think one could build a breakout connection with replaceable fuses (maybe as simple as car fuses or glass tube fuses) on the data lines. If amperage coming in the data lines spikes over a certain level, it blows those fuses and voila, your compy is safe. Nothing disposed of more than a cheap fuse, and you thwart such an attack.
Not really, fuses are too slow. By the time the fuse blows, the computer is most likely dead. (at least the usb port certainly would)
The most effective defense, as stupid as it sounds, is just to not plug questionable stuff in your computer. There aren’t any economic protection schemes that will work on the data lines at usb 3.0 speeds as far as I am aware of.
An optical coupler on the data lines might work….
How… James Bond-ish.
I also always use random USB sticks that I don’t know where they belong to… I ESD zapped my USB port accidentally often enough. PC reboots and can’t proceed because the sata hardware has shut off. Do a hard reset and everything is fine again.
Where is the problem?This device is a nice tech demo but nothing dangerous.
Seems like I confused freeze with fry… in that case it’s a problem. Best protection? Don’t use USB stuff where you don’t know where it belongs to.
Diabolical. Love it.
I can see the lefty lawyers itching to represent some crook who has had his laptop fried because of some inconsiderate victim.
schematics please? i really need this to plug it onto my ex’s pc….
I was cashing a check at a bank, and there was a usb stick laying on the counter. They said they found it, didn’t know who’s it was, and were keeping it there in hope the owner showed up. And were getting ready to plug it in since it’s been there for days…..
I just want to add that this is AWESOME, I hate robbers. I’ve been robbed, I designed (but never implemented) a mockup phone with spring razor blades. Obbiously dangerous and illegal, :P
Instead, make a mockup phone that has a small batter and a pack of thermite. when the thief tries to turn stolen goods on. No more hand.
On the one hand, this is a Thing That Should Not Exist, and the fact that it does disturbs and frightens me. I mean, it’s not like it’s a boobytrap designed to harm people, but a boobytrap designed to harm expensive equipment is bad enough.
On the other, I’d love to see it get stolen by the NSA (or local equivalent/wannabe).
Of course, nothing’s bad enough for them, and unfortunately this attack wouldn’t put a significant enough hole in their operations to be worth the heat it brings on you. (If they catch you you can expect decades in jail. What they charge you with is secondary. They’ll think of something.).
I can’t actually think of a delivery method that is targeted enough to not be morally reprehensible and secret enough not to get caught.
Using it as an antitheft device (and thus risking it escaping into the wild) sounds like a thing only a truly terrible person would do, as the possibility of harming innocents rivals or exceeds the possibility of hitting the target (and small time thieves are not an existential threat to society, so they don’t justify the pain and suffering mistakes could cause). Maybe if you mark it “DANGER: DO NOT USE” or “SABOTAGED”, but you’ll never find a marking that excludes all innocents AND doesn’t dissuade attackers. (I don’t think you can even find a marking that dissuades all innocents period. People are curious.)
As for delivery to the NSA/other illegal, unethical, antidemocratic snoop organizations…
Border guards will arrest you if their equipment malfunctions while they try to copy/reflash your stuff.
If you are stealthy/suicidal enough to plant things in NSA parking lots/etc., you should consider traditional cyberattack. (they’re probably not going to plug it in, anyway.)
I suppose if you leave them lying around on your private property when you suspect illegal physical intrusion, that’s a possible use case. They still know it was you, but they’ll have to hide the illegal search. Or retroactively ‘make it legal’ and add charges to you for breaking things I guess.
Hardware attacks like this are clever and satisfying, but do three VERY BAD things:
-They make it obvious that an attack occured and what device caused it.
-They attack indiscriminately (this one, at least, is triggered by a powered USB port, instead of targeting a particular adversary.) Refusing indiscriminate collateral damage is what separates civilized people from savages like the NSA and IS.
-They don’t have any chance to cause enough damage to seriously inconvenience a military organization.
While unglamorous, I believe that software attacks would be much more capable of inconveniencing mass data collection organizations by damaging the integrity of the databases their work revolves around instead of destroying physical machinery.
A trojan that bides its time and eventually leaks large volumes of data from an NSA database to the public is infinitely more damaging to the surveillance state than a fried workstation, and is MUCH less ethically grey. Just watch out for when they eventually find it and start sending out misinformation/attacks against people examining the data.
Actually, thinking of hardware, I wonder if one could fit a cellular modem into a removable storage device (maybe something with DMA, did they make Firewire removable drives?) using some exploits to dump data from any machine it’s attached to (RAM is probably easy, disk harder, and network resources harder still) to a publicly accessible server while exposing a (easily crackable in a simple-but-slow way?) encrypted nonsense partition to encourage leaving it connected for longer? I’m sure the NSA already has things like this, but they seem to prefer exfiltrating private data over the Internet (that I know of).
If you HAVE to destroy things… (in a state of open revolution or something?)
The best thing to do to them would be something subtle that infects the operating system (or better, hard drive/SSD controller), possibly on multiple machines, and then corrupts data over a long period of time, ‘randomly’ but increasing in frequency over time so that it’s mistakable for a drive going bad (count up every time a file is written to and flip bits when you hit a drought between prime numbers larger than some cut off?). Better yet, try to figure out how they back the data up and make a useless backup before attacking the originals.
Obviously the biggest thing about cyberwar (or warfare in general) is making ABSOLUTELY SURE somebody is evil BEFORE taking any action against them (overt or covert). That’s what MAKES the NSA evil. (Encryption sabotage, dragnet searches, etc.) Any would-be vigilantes out there should remember that. “He who fights monsters…” and all that.
Now, I remember reading something about memory-corruption vulnerabilities in common forensics software. THAT sounds like a good method to get a destructive worm onto an airgapped spook network while being less likely to go off on innocent citizens. Then again, they might not use networked machines for data forensics.
On a cheerier note:
For this and all the recent data and firmware attacks we’ve been seeing, I would be interested in a dirt-cheap device that can do various experimentation on USB sticks without connecting them to a modern computer. Some kind of Removable Drive Warfare kit?
Maybe a simple handheld interface (I’m thinking Game Boy. The cheapest monochrome screen you can find, some cheap display controler, a D-pad, maybe a button or two, a cartridge slot for modules with USB ports and specific hardware.)
One read-only module to identify/read filesystems and list files. Maybe some text file reading capability.
One module to make an image of the memory on a drive (subvert any well-understood controllers to get wear-levelled stuff, somehow?) (would need a USB port for the target drive and some other kind of removable storage (MicroSD?))
One module to wipe a drive. (integrate this with one of the others?)
A module to do firmware dumps/reflashings. Would also need removable storage.
Isolate the thing right and you’ll be out a cartridge at most when you plug destructive devices like these in. Maybe less…
Would also be REALLY handy for antivirus people trying to figure out how a piece of exotic sneakernet-transmitted malware works (especially since they seem to be dealing with more and more state-sponsored stuff).
Do people still make Harvard Architecture (separate memory for program and data) devices anymore? Because those sound ideal for quarantine jobs like that.
So basically: this device, while generally useless (‘like an atomic bomb’, as the linked article said), is TERRIFYING. I kind of wish I hadn’t seen this headline. Thank you for carrying the story.
Holy fuck please take your medication.
sdlkfjalskd, LOL! Why yes, indeed.
God forbid anyone have a thought longer than 240 characters.
The only thing concerning to me is the number of people interested in having one.
Passive aggressive much? Why in the world would anyone want this?
And possibly the number of people amazed at a boost converter. Everything described in the article above is really just a camera flash driver except instead of one large cap, they are using several large SMT caps and making it re-trigger (more like a strobe driver, I guess.)
But, I have some doubts this is real. In the photos, I see no evidence that the data lines are connected to anything. No vias and no traces. The only vias and traces I see are on the power lines. All of the chips are obscured so you can’t read what they say, so hard to guess at what they do. But a simple charge pump wouldn’t require so many chips.
Basically the photos do not match the description of what it supposedly does.
If I were to guess, I would say it looks like a high-voltage driver for a USB powered negative ion generator.
In the prototype, notice only the power wires are connected. Also notice the lack of a transformer or inductor. Also notice on the prototype the bent copper wire across the caps formed like a spark gap and the third copper lead (the one sticking straight up) as a trigger.
I’d like to see something like this built into a line of high-security flash drives. A fully functional drive, on insertion t would mount as a human interface device and launch some program to ask for a password. If the correct password is entered, the device would scan the host computer for monitoring software (sort of a mini-audit) and mount the internal storage area of the drive after completion. If the wrong password is entered, the drive would install any manner of nefarious software selected and raise an alert to the user to remove the drive within 10 seconds. If the drive isn’t removed, initiate the computer destruction sequence noted above and then use the excess charge to ignite a small store of thermite placed above the memory chip. Still clean and useful. A good solution for those that need to travel with secure data, and a fair warning to those who get ahold of their device without permission. You could even include a duress password if you were forced to give the unlock code.
“A good solution for those that need to travel with secure data”
Yeah, airlines have no issue with people travelling with electronic devices that contain combustible material. Destroying the data not the host is always going to be the better solution, but it doesn’t need anything quite so theatrical.
I had in mind CIA agents traveling with mission details as opposed to your standard commercial traveler. Besides, thermite ignition isn’t a combustion, it’s an oxidation-reduction reaction. But I agree that most airlines wouldn’t be generally pleased with either. I’d be happy to hear other suggestions, perhaps just the nichrome would work?
If it works I will buy a few of them. or make one if I have to. put it in a envelopment in my house safe that say’s “bitcoin and admin passwords”. So if anyone steals it they will get jacked when they plug it in.
I recently fried most peripherals on a PC motherboard, including some connected USB devices, by accidentally plugging in a non-USB device that has a USB connector. It’s a handheld GoPro gimbal, Feiyutech FY-G3. I forgot u need to plug in a USB to serial converter dongle in between to carry out firmware upgrades.
A VERY easy mistake to make given the very poor choice of connector and months since I last did it.
The computer still worked, but lost on board audio, the wired network connection, along with all 10 plus USB ports and some connected USB devices!
Hella effective! Paid out hundreds in repairs.
Congrats. Now the TSA will ban USB drives from being carried on airplanes.
32gb micro-sdhc card. and plastic card reader :) You can smuggle a library of congress on yourself, before cards trigger a metal detector.
Just test it by plugging it into the photo kiosk at Walmart. If it works, you’re good to go, and if it fries, it wasn’t meant to be.
Shut up and take my money! Where do i buy ten units of it?
https://darkusb.wordpress.com