[Ronnie] recently posted a new chapter in his adventures in malware deconstruction. This time the culprit was an infected Excel spreadsheet file. The .xls file was attached to a phishing email claiming to be related to a tax rebate. With tax season in full swing, this type of phishing message would be likely to be opened by an inexperienced user.
[Ronnie] saved the file to a virtual machine to prevent his real workstation from getting infected. He then opened it up in Excel and noticed that it immediately attempted to run macros. A macro is essentially visual basic scripting that runs inside of the spreadsheet file. You can use it for simple automation, cell formatting, or do even more complicated tasks like reach out to external websites and pull information. This malware focused on the latter.
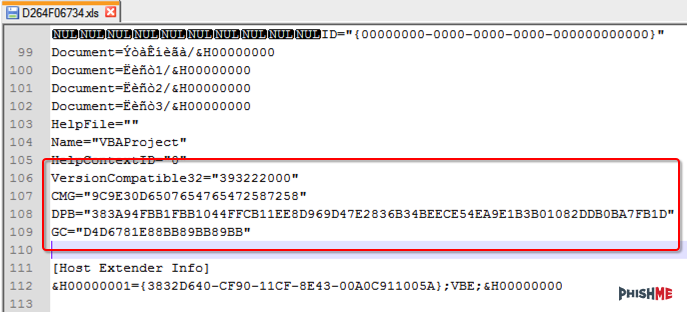
[Ronnie] used the alt + F11 shortcut to view the macros. Unfortunately the attackers had password protected them. [Ronnie] wouldn’t be able to view the macro code without knowing the password. Luckily, he learned of a surprisingly simple trick to completely bypass the macro password. He opened up the .xls file in Notepad++ and located three keys; CMG, DPB, and G. [Ronnie] then created and saved a new blank .xls document and password protected the macros with his own password. He opened up this new file in Notepad++ as well, and located those same three keys. He copied the keys from the new file into the old one, and saved the old file. This effectively changed the password of the malware file to the new one he had set for his new file. This is a nifty trick that apparently only works on the older .xls formats, not the newer .xlsx format.
After loading the macros, [Ronnie] quickly noticed that most of the code was obfuscated to make it difficult to analyze. There were, however, three named modules that reference possible sandbox evasion techniques. The malware first invokes these functions to detect the presence of a virtual machine or other type of sandbox. If it detects nothing, then the rest of the malware program is decoded and executed. [Ronnie] removed these checks and then executed the macro to verify that his change had worked.
The next step was to try to view the decoded instructions. The decoded gibberish was saved to a variable. The simplest way for [Ronnie] to view the contents of the variable was to have the program create a pop-up box that displayed the contents of that variable. After making this change and running the program again, he was able to see exactly what the malware was doing. The code actually invoked Powershell, downloaded a file from the Internet, and then extracted and executed that file. In the full write-up, [Ronnie] goes even further by downloading and analyzing the executable.















That’s a roundabout method of doing it. I remember just having to change one hex digit and then then opening the file. Excel would complain about corruption but it would allow you to get to the password box without entering the password. Then you just untick and save.
I’very done that in the past, but last time I tried that on the latest version, it really made excel very upset and you couldn’t do much. I ended up using the Visual Studio debugger to skip over the password check.
Kratz,
Feel free to check out the following python script in the update. http://phishme.com/dridex-code-breaking-modify-the-malware-to-bypass-the-vm-bypass/#update This should bypass most, if not all of them without having to open the Visual Studio debugger!
–Ronnie
@iHeartMalware
Hey Garbz,
I’ve seen some folks mention this method, however I haven’t tested it / I wanted to be able to run the macro file without it being corrupted. This method keeps everything intact, so the file is happy and still executes.
–Ronnie
@iHeartMalware
The sample subs look like dummies, they have pointless loops followed by never-true if-then-end statements. This counts as obsfucation?
Erik,
Yup, I would consider this obfuscation. The main point of obfuscation is to make it more difficult to analyze by making it look different, and they (almost) succeeded here. ;)
–Ronnie
@iHeartMalware
Interesting. There is a lot of malware going around on Steam these days. I’ve been saving it for analysis. Some of the web-based virus checkers are having trouble with some of the samples, flagging them as ‘OK’, even though it’s patently obvious they are up to no good.
Valve’s Cabal is a load of crap and will eventually self implode into a smoking mess of idiot programmers, ruined computers and angry users. That asshole Gabe Newell will be as clueless as ever, jerking off in his open door office surrounded by the mountains of cash everyone was stupid enough to send him.
It’s no surprise you’re getting a lot of malware. The developers only incentive to fix anything is if it’s interesting to them. Go ask one of the early beta testers whose accounts got carried over into final release how they’ve managed to update their account because Valve thought it was a good idea to use emails as primary keys in the database. Microsoft will happily let you change your credentials, for a small fee. Valve won’t even go that far because none of the programmers find fixing the damn database “interesting” enough.
Wow, butt-hurt much? For a small fee Mamma Microsoft will make it all better. The Steam platform may be a steaming pile of crap, but it Has a whole bunch of Linux games, that run better than on Windows. Don’t worry, for a small fee Microsoft will protect your Windows install from the millions of Viruses out there. And for another small fee, will reactivate your Windows install once Genuine Advantage sh*t’s all over itself.
I might get a lot of Malware, but it does nothing on a Linux system.
I was one of the original testers for Steam and the inability to fix the old login name (it was tied to your email) is extremely annoying since many users no longer have their email from that long ago.
I think Es is referring to the Live! Service. I think MS charges something like $5 or 500 points or whatever they use to change the login name. Something a lot of the old Steam testers have long clamored for. Check the Steam forums if Valve haven’t deleted the threads (they are prone to do that as well).
In addition I read a recent article about the problems at Valve written by someone who once worked there, was it here on HaD? I’ll have to hunt it down.
Citing the use of Linux is a rather poor solution as “protection” from a poorly implemented system. I work in a corporate environment and the Linux camp is still unable to convince a multi-billion dollar company to adopt any flavor of Linux en-mass. Perhaps the energy spent bashing Windows be better spent at improving Linux penetration?
I use all operating systems as I see fit. It took me a long time, but I decided that no one OS is better at everything than another. So feel free to bash Windows or anything else as you like, I’ll get back to actually doing something useful.
Malware is boring. Even APT stuff doesn’t attempt to get past anti-virus solutions it’s just built to scale and scrape before signatures.. Exploit dev and embedded security is where the fun is.
Also, you don’t need powershell to do HTTP queries. I once streamed CSV to sheets using VBA alone. You can actually fetch encrypted VBA and run it through eval, but there is no way to prevent the payload from being dumped since source can be recovered and edited..
Another neat trick to do is to open the file as a zip file and look at the raw data. The xlsx format is actually a zip file renamed with specific files in it. You can crack it open using 7zip. Course he is dealing with the older format…
Using OllyDbg and getting the vbStrCmp works, you can get the password that way, I remember doing it in old Excel versions.
Hey wait wait wait, back up….
How do they detect the sandbox, are you saying I just would need to make malware THINK its in a sandbox for it not to work!?
This is halarious. javascript malware aparently also does sandbox evasion.
hmmmm
That would be a pretty neat approach to security…add different mechanisms to make your computer “look” like a VM to malware. I like it!
–Ronnie
@iHeartMalware
There is more in-depth information available here: http://phishme.com/dridex-code-breaking-modify-the-malware-to-bypass-the-vm-bypass/
One of our business user’s was also affected by this today and after a few hours of poking around in the infected system I managed to find a public GitHub repository of the attacker and his code which I’ve sent onto Microsoft’s security team…
Hey Rewt0r,
We saw new samples as well that contained the same GitHub repo. The Dridex folks responded with longer passwords, so I appended an update to the blog which should work on ALL password protected macro files.
http://phishme.com/dridex-code-breaking-modify-the-malware-to-bypass-the-vm-bypass/#update
Happy hacking,
–Ronnie
@iHeartMalware