[Alessandro] is an unlucky VoIP PBX administrator that frequently has to deal with very, very dumb network policies. Often times, he’ll have to change something on his setup which requires him to go out to his client’s location, or ask a client to use Teamviewer so the appropriate change can be made from behind a firewall.
This isn’t the solution to the problem. It will, however, fix the problem. To get around these firewalls, [Alessandro] is using the voice channels he already has access to for changing configurations on his VoIP boxes.
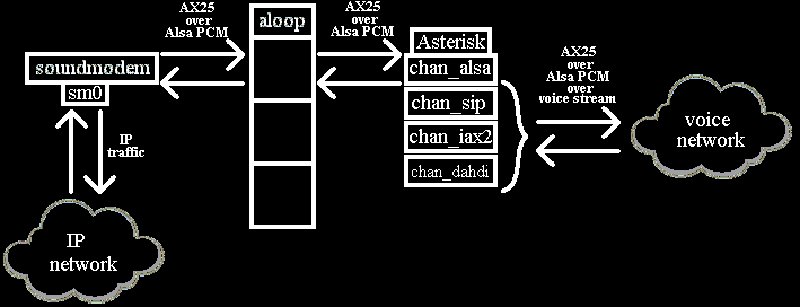
The implementation of this uses the AX.25 amateur radio modules that can be found in just about every Linux distro. This, and an Alsa loopback device, allows [Alessandro] to access a terminal over a voice-only network. Is it a hackey kludge? Yep. Is it just a little bit dumb? So are the network policies that don’t allow [Alessandro] to do his job.
This build isn’t too dissimilar than a bunch of modems from the old BBS days, albeit with vastly more powerful software. [Alessandro] says you’re only going to get about 38400bps out of this setup, but it beats begging for help for remote access.















I have customers that will not let you communicate with anything inside their facilities in any way. In-fact doing what this guy is doing is not only cause for dismissal, it would probably land him in the cooler for a long and unpleasant interrogation. The facilities are strictly red/black, with anything going to/from the black side tightly controlled and strongly encrypted. These are concepts the U.S. Government seems to know little about and/or responsibly practice. Just look at the recent IRS penetration – and that is just the tip of the iceberg.
Not having administrative interfaces exposed to the outside world is a very, very sane security policy IMO. And installing backdoors a very good ground for firing someone.
This is a clever hack, however, this guy is asking to be fired on the spot. Those “stupid” policies are typically in place for a reason which he is likely not aware of (contrary to the popular belief, network admins don’t put draconian policies in place for their entertainment and to impede everyone else’s work!). Bypassing them without authorization, no matter how dumb he thinks they are, is something that would likely put a few network people in rage and should get him fired. He might even get sued if his vigilantism caused the company to run afoul of some relevant data protection regulations and God protect him if the company gets hacked because of his stupidity.
Really, folks, don’t do this. This is pretty much equivalent to backdooring your customer. Sooner or later someone will find out (especially if you brag about your cleverness online!) and you are going to be in a world of hurt.
Thank you for pointing up this reading of my article. You’ve right in say that network administrators put their policy in place because very serious reasons. When I wrote it I didn’t mean to hack nobody’s network, in spite it might look like. As voip administrator, not frequently, I deal with structured big company with reasoned network policies. Instead, often my deals are with small company administered by outsourced IT that have as their only objective, earn as much money they can from the customer doing smallest efforts. When I wrote my article, i was referring to such situations, where customer are not qualified enough to have their own policy and let those guys administer their networks in this way. My apologies to any serious network administrator.
I believe you are a slightly too dramatic. Author only purpose is only to get access to some setups he is legally entitled to access. For what I understood, the idea behind this workaround is to get access to a network setup without the need to be physically on the spot or connected via Teamviewer (should we trust more the teamviewer guys?).
Actually this is a mere prof of concept which must be deployed in a real scenario with full awareness and acknowledgement of the customers involved and surely. Finally I could say the service could be temporary enabled on the pbx by the customer himself via peculiar commands or actions thus implying his implicit acceptance of the intervention.
This solution allows you to alter the setup of a pbx… I don’t think it would be ever possible to initiate a thermonuclear war simulation with an AI fully integrated in the DARPA defence system…
On the plus side, great work. 38k is plenty of speed for a shell prompt level access and configuration of asterisk.
On the down side, he’s just created a direct access path around his company’s entire network security architecture with 38k network access to a linux machine which, if compromised, sits on the inside of his company’s network.
From a skills perspective, he gets a round of applause. From a corporate security perspective, he gets fired and immediately escorted off the property.
No, this is not the solution to the problem. (He even admits it isn’t in the first couple paragraphs.) The admin interfaces for all critical devices should be secured behind a firewall. It would be dumb to leave them exposed to the public Internet for anyone to hit. (SSL on a random port with a ‘correct horse battery staple’ password is fine for your home Raspberry Pi music server. Your company’s phone system, not so much.)
If he needs regular access to Asterisk on that PBX, then the client should provide him a laptop with VPN access secured to their standards, or a secured local PC (or VM instance) he can remote into and use as a jump box.
This is a back door. If an outside contractor (or worse, an employee) did that on my network I’d tear up their contract.
And [Alessandro]’s hack is yet another proof that perimeter firewalls are a bad idea. In the words of Bill Cheswick, who invented the things: “it’s like circling the wagons around the state of Wyoming.” Protecting more than 30 or 40 hosts behind a single firewall is invitation for this sort of hack by anyone at your institution to bite *you* in the ass later.
Big monolithic firewalls are problematic they have always been so. The fastest firewall I know of can almost handle 10 of our machines while filtering packets at 120 Gbps.