Last week saw the revelation that you can control Siri and Google Now from a distance, using high power transmitters and software defined radios. Is this a risk? No, it’s security theatre, the fine art of performing an impractical technical achievement while disclosing these technical vulnerabilities to the media to pad a CV. Like most security vulnerabilities it is very, very cool and enough details have surfaced that this build can be replicated.
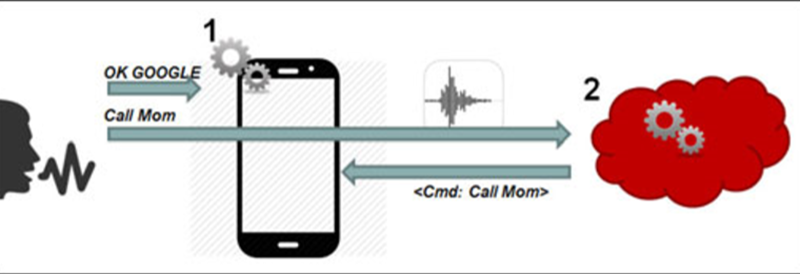
The original research paper, published by researchers [Chaouki Kasmi] and [Jose Lopes Esteves] attacks the latest and greatest thing to come to smartphones, voice commands. iPhones and Androids and Windows Phones come with Siri and Google Now and Cortana, and all of these voice services can place phone calls, post something to social media, or launch an application. The trick to this hack is sending audio to the microphone without being heard.
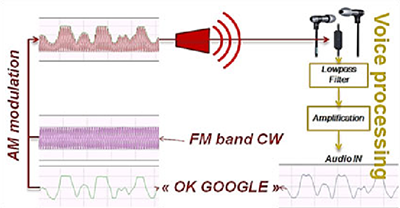 The ubiquitous Apple earbuds have a single wire for a microphone input, and this is the attack vector used by the researchers. With a 50 Watt VHF power amplifier (available for under $100, if you know where to look), a software defined radio with Tx capability ($300), and a highly directional antenna (free clothes hangers with your dry cleaning), a specially crafted radio message can be transmitted to the headphone wire, picked up through the audio in of the phone, and understood by Siri, Cortana, or Google Now.
The ubiquitous Apple earbuds have a single wire for a microphone input, and this is the attack vector used by the researchers. With a 50 Watt VHF power amplifier (available for under $100, if you know where to look), a software defined radio with Tx capability ($300), and a highly directional antenna (free clothes hangers with your dry cleaning), a specially crafted radio message can be transmitted to the headphone wire, picked up through the audio in of the phone, and understood by Siri, Cortana, or Google Now.
There is of course a difference between a security vulnerability and a practical and safe security vulnerability. Yes, for under $400 and the right know-how, anyone could perform this technological feat on any cell phone. This feat comes at the cost of discovery; because of the way the earbud cable is arranged, the most efficient frequency varies between 80 and 108 MHz. This means a successful attack would sweep through the band at various frequencies; not exactly precision work. The power required for this attack is also intense – about 25-30 V/m, about the limit for human safety. But in the world of security theatre, someone with a backpack, carrying around a long Yagi antenna, pointing it at people, and having FM radios cut out is expected.
Of course, the countermeasures to this attack are simple: don’t use Siri or Google Now. Leaving Siri enabled on a lock screen is a security risk, and most Androids disable Google Now on the lock screen by default. Of course, any decent set of headphones would have shielding in the cable, making inducing a current in the microphone wire even harder. The researchers are at the limits of what is acceptable for human safety with the stock Apple earbuds. Anything more would be seriously, seriously dumb.














Your average consumer grade headset is not built with coax cables. Even if you managed to find one that is built with shield *audio* grade cable, it might not work too well at FM radio frequencies that are at 3 orders of magnitude higher frequencies than what it is intended for. A common mode snap on ferrite block at the connector side would probably going to do a good job for blocking this.
Not sure why one would need SDR for this other than google buzzword for noobs. It is not like you’ll need a fancy digital modulation scheme. A sloppy one that SPAM all over the spectrum would probably work better. It is far easier and cheaper to find or build 1-2 transistors FM transmitters (“Mr microphone” “FM bug”) and modify it for AM. Back in the days that is probably one of those beginner’s projects. I would be surprise if those discrete transmitters are not also amplitude modulating the output. Just need to add the RF amp to boost the output. Chip based ones intended for ipods to car radio are probably harder to modify.
Heck, if you could the extra earbud wire that would almost certainly be enough. A ferrite should murder it.
Coil, not could. Get.
It’s a fun hack.
Practicality of it as an attack vector is pretty negligible…
You dependent on some one having ear buds, and they need to be a brand you can identify and find the wavelength for the microphone wire… and even after all that, you only have access to give voice commands not to intercept the output… unless google and siri can “email asdf@asdf.com my calendar” or “send all private documents to russian@hackers.com” then you’re not going to accomplish much… and if the other person is wearing that headset (likely since a microphone cable coiled up in some one’s pocket is going to be harder to have a signal induced in it.) they’ll hear siri or google saying “Private documents sent to russian hackers” or worse “Do you want to send private documents to russian hackers?”
Though the obvious solution is to put a captcha on siri and google now… “If you’d like to send private documents to russian hackers please read text on the screen.” or maybe security questions “If you’d like to text your wife [it’s ok to sleep with the guy across the street with the big yagi antenna pointed at our house] please tell me the name of your first pet.”
A number of Siri commands require that you unlock your phone with passcode or fingerprint. I’m sure the same is true of Android.
The microphone wire is no narrowband filter. You can roughly estimate the frequency from its length (as a lambda/4 antenna). But it will easily work +/-50% of this frequency, perhaps an even bigger range
I heard my brothers CB radio (27MHz) in my stereo when he had his antenna (non-directional) in front of my window with just 4W of power. I do not know, which wires (speakers, mains, CD) were susceptible or if it was the internal electronics.
Use a scatter-gun approach:
Build the device using some simple electronics, then leave it in a public-ish place. A friend of mine has a second-floor apartment right above the entrance to the subway. Just hang it out the window and have it constantly transmit on a loop using varying frequencies then transmit the various commands to visit a specific URL hosting exploit code. Depending on the foot traffic near the transmitter and then success rate of the attack, you could get a couple dozen bots a day for a mobile botnet (Which seems to be the thing to do nowadays, eg enslave phones to spam telemarketing calls to other people)