A while ago, a few journalists from China visited the Metalab hackerspace in Vienna. They wanted to do a story on ‘fablabs’ and ‘makerspaces’, despite the objections to the residents of the Metalab hackerspace. Apparently, mentioning ‘hacking’ on China Central Television (yes, it’s called CCTV) is a big no-no.
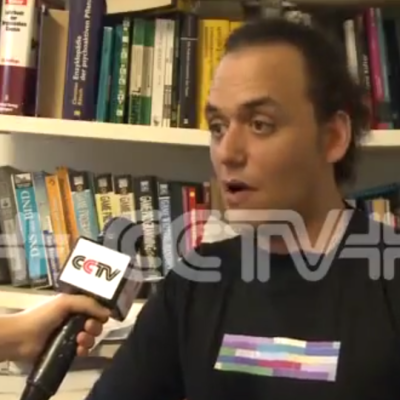 Wanting to send a message to at least a few people in China, the members of the hackerspace had to think laterally. Metalab member [amir] came up with a way to encode data that could be printed on t-shirts. These bright, colorful squares featured in all of the interviews with Metalab members carried messages like, “free tibet!”, “remember tian’anmen 1989” and “question the government. dont trust the propaganda”
Wanting to send a message to at least a few people in China, the members of the hackerspace had to think laterally. Metalab member [amir] came up with a way to encode data that could be printed on t-shirts. These bright, colorful squares featured in all of the interviews with Metalab members carried messages like, “free tibet!”, “remember tian’anmen 1989” and “question the government. dont trust the propaganda”
All the videos are available in this playlist, and [amir]’s code to generate the colorful rectangles of political activism can be found here.
In a related note, we’d like to say ‘hi’ to our one reader in North Korea. Yes, according to the stats and analytics, we have one reader in North Korea.
https://www.youtube.com/watch?v=KZzG98NZqfo
https://www.youtube.com/watch?v=_dyXtmaidnc
















“question the government. dont trust the propaganda”
I think that’s one everyone regardless of nation can benefit from.
Except you people are so preoccupied with “the Government”, that you don’t realise how bad your fellow civilians are.
Quote: “Yes, according to the stats and analytics, we have one reader in North Korea”
Hi Kim.
I haven’t actually noticed that stat. But thinking of this, is it the country’s intranet pulling in a static copy of everything?
Regardless, if their IT security team is as good as the US would have us believe, you may have just identified an individual out of the metadata.
There is no reason to think the relatively covert security program would use a North Korean IP, rather than a Chinese one. There is, however, reason to be cautious when publicising information which could identify small groups of individuals when combined with nation-state resources.
Has Paul Revere’s metadata taught us nothing?
I literally have no clue what i just read, who is Paul Revere’s, and why do you have to be a dick about it with lmgtfy.
TLDR;
Through relatively innocuous datapoints it becomes trivial to identify persons of interest. If modern metadata techniques were applied by the British troops, Revere could have been detained before his midnight ride, Samuel Adams and John Hancock may well have been captured, and Massachusetts school children might well be singing “God save the queen” at the start of school.
The dickness was to press a point; Privacy is important, and this was a breach of privacy, and the principles of anonymisation should be known by journalists. T. M
The importance should be easily understandable. If you got rolled, RTFM and turn on the status bar..
If North Korea is as bad as it is made out to be, this kind of re-identifiable data can identify an individual with serious repercussions.
If others are correct in asserting that this is just the IP of the “Intranets” this may be an overreaction. But given that the your postcode, your Birthdate, and your gender are enough to Individually identify 85% of Americans, the uniqueness of the datapoint renders the “anonymity” moot.
“Who am I; I am an American, the only person who signed federal Acts for the United States of America since 20th Janurary 2009”
“Who am I; I am the only individual on this side of the network gateway to visit a politically inappropriate website”
– I own the network log; I can find which IP/s connected, which ties locations and computers to an account. This may yield multiple physical locations and co-conspirators
– I may be able to work out which posts were viewed based on timing. Trends in topics may lead to interesting findings such as an interest in social media, electronics, or explosives
– Based on outgoing traffic volume, I may be able to work out which posts were the individuals giving me insight into their opinions/interests/activities
– I can correlate this against other website traffic on other sites, against TOR traffic, known proxies etc…
The implication is that if 18th century British intelligence had modern metadata analysis available to them, they could have quashed the impending American Revolution easily by killing a few well-connected individuals.
@AussieLauren British children don’t sign ‘god save the queen’ at the start of school, that kind of indoctrination is a north-korean and good old USA thing.
I recall an article tearing apart their Firefox clone, and apparently their entire internet is actually an intranet, set up like a home network. So it might be possible that the entire country shows up as one person.
Yeah, I think that was a HaD post, and I agree with you.
Analytics question – what system did you use to find that? GA, Apache logs (what IP-> geography service?), or something else? Very interested as I work in a site which we suspect has readership in NK but never seen Analytics to support it.
Your log files will have IP addresses for all the httpd requests. Just use something like geoip or the ip location database to extend the traffic data to location.
That’s what we’re doing. Just not sure if they’d identify an NK user reliably. I suppose NK IP range is known, but users would likely be using a proxy?
All request log files will show you is the last point from which the page request came from. It’s useful for stats only. There are proxies, vpns and all manner of ways that users will avoid you ‘identifying’ them. So just take them as stats only and with a pinch of salt.
what happened to that ladies eyes?!?!?
Which lady?
yay a story from my homecountry :D
“no trust to Govt.” of course.
In the infographics shown in 2nd video, the “maker” is presented as TIE-WEARING-WHITE-COLLAR.
What a dismay… or did they hack us back?
;-)
I say wear whatever you want as long as you tech tricks are strong and you share them with others ;-)
Just don’t wear long sleeves near the dangerous machines…
Don’t forget your Safety tie!
Not OK to pronounce “hacking” on CCTV, but pronouncing metalab as “methlab” is A-OK?
Actually, metalab _is_ called methlab.
See http://methlab.at ;)
I hope the Chinese government doesn’t get wind of this and raid them, (and they most likely will).
Also, why are most of them white?
Yeah, right, China raiding an Austrian Hackerspace. Not very likely.
And most of them are white because Austria is a predominatly white country.
WTF has “white” got to do with anything.
The hackerspace is located in Vienna (Austria, Europe). I doubt the chinese government would risk an international conflict because of a few colorfull recatangles.
The journalist from China might be in more trouble, but i know too little about the chinese legal-system to make any predictions.
Ah, sorry. Skimmed. Should take my own advice to RTFM.
So people can’t be white? Nobody would’ve asked the question “why are most of them black”, “why are most of them Asian”. And that’s racism.
Taking a political stance is great and all, but know your audience.
They should have used QR codes. Whilst they haven’t caught on quite so much in the West they are prolific in China.
If you want to get a message across far more people understand them than what was used and can simply point their phone at the screen.
Right, because the state tv wouldn’t scan the QR codes before airing it.
I bet the chinese censorship-guys are smart enough to do the same….
Some tought was put into this venture up front.
Making things too obvious would have the team cut everything up or not send it at all.
Also look at that guy with the giant tin-foil hat ..
He walked around all the time to increase the chance of being in the spot later on.
And in one video overflo (the guy with the green marble around the neck ad the black cappy) gave a short interview mentioning the “metalab hackerspace” in every second sentence so it would be hard to edit it out..
And it got on air as well.
But yes .. there is no great success in this.. just some toying with the media.
One question – how are they gonna decode this? I mean, there are many, many ways to encode data in colorful rectangles, and GitHub is blocked in China, so will they need to re-engineer the algorithm to understand it? Or are they supposed to just read it on Hackaday?
As far as i understood from looking at github the “colored rectangles” are morse code.
This is not very well visible from the compressed youtube videos, but i guess you can spot that on the original HD content on TV.
Its morse code, duh. ;)
You rock, Amir! Great stuff from you as usual ..
No, it is just a raw Morse code, it is only a little bit colorful (see GitHub examples). Bigger problem is a very poor camera/screen resolution, so it is difficult to see the borders between dots and dashes.
Of I understood Armir’s code correctly it is just Morse code in form of colorful rectangles. I will ask him the next time I see him ^^
TOR can get around the great firewall of china
It will be slow as the internet from the 90s and won’t use flash and Java or something but it would work. All TOR does is use the darknet and VPNs to bypass firewalls and provide some sort of anomity but any one with the resources, know how, and hardware could track you. And so no one can ask what TOR is here’s a link
m.disclose.tv/news/exploring_the_darknet_a_complete_beginners_guide/124143
Um on a secondary note you need fast internet to use TOR
Who do you think is running all the exit nodes in China?
By “resources” you mean “owning a large proportion of all nodes, and even then it’d be a crapshoot”.
TOR, AIUI, only requires one honest anonymiser in the chain you use, to be untraceable. Sure there’s traffic analysis but again, the nodes do a bit of scrambling on that. As long as one node forgets your details, the chain from endpoint to entrypoint is broken.
Of course owning an endpoint gives you the data the user is sending to whichever computer they’re connecting to. But that depends what the data is. You can still encrypt your own data if you’re sending it somewhere important. If you’re just posting on 8chan, your data’s worthless anyway.
It works the same way the old email anonymisers used to work, wrapping an encrypted session in another encrypted session, layer by layer like pass the parcel, til the endpoint connects back to the ordinary Internet. Far as I’m aware, nobody can find a user’s IP if he uses TOR. You CAN do detective work, and collect lots of data to try spot patterns. They only got Dread Pirate Roberts because he fucked up and used his name on the clear Internet. They had to use traditional social-based ways to trap him.
Sorry, but using TOR without an obfuscated bridge in china is _really_ a _very_ bad idea in china. It’s easy to spot those “honest” nodes your talking about – resulting in possibly grave consequences.
I would use non-standard wiring colors and then lie about the traces just like their circuit boards ;) They are just going to give your university a grant from AliExpress to cover the fact they send students as industrial spies. Nothing to see here folks…
Hello to you too dear Hackaday people. -Kim
Ya right.. because china is evil..
Who was that austrian guy again? The one that wanted to be a painter but never made as one..
They should have written “TREAT REFUGEES WITH DIGNITY” in plain german…
The Germans are doing a better job than the British are. And gods help us, than the Americans would if refugees turned up there.
To keep this short, the anti-refugee thing is another example of loud-mouthed arseholes making everyone else look bad. I have a mate who’s an American Christian, and is intelligent, logical, and humble. He gets pissed off with the way certain members of the flock end up making him look.
If most decent people MET a refugee and heard their story, they’d welcome them. It’s just the stupid shit that passes for “news” these days. Walter Cronkite will be turning in his grave, if he’s dead. Bernstein and Woodward next to him.
You USED to have a reader in North Korea.
Looks like the Great Esteemed Peoples Progress of Glorious Technology Revolution just got set back another 60 years…
Smooth move, HAD, that’s Prime Directive stuff right there.
“free tibet!”
I suspect some people need to research what Tibet was like before the Chinese came into power there instead of knowing some popular phrases being their entire understanding of a complex issue.
Hint: It’s wasn’t exactly a utopia.
Yeah but it might have been by now. Plenty of places were fascist shitholes in the past. Including Spain.
It’s just the utterly arseholishness of invading a country full of pacifists. Not the sort of thing a great people would do.
Still I sort of admire the Chinese’s view on stupid mystical hippy religions. If people aren’t going to be critical themselves, kill the bullshitters! In another life I’m in the chemist’s right now, chainsawing anyone who picked up a homeopathic “remedy”.
Tian’anmen eh. So, let’s remember what ‘we’ did since 1989.. or maybe no, let’s not eh. The tally of victims might be a bit ‘upsetting’
As for propaganda, the chinese are complete amateurs in that field, else they would not need to attempt to hide things.
They should outsource propaganda to the US and europe and use the expertise available. They’ll never catch up on their own. And they use western made firewall equipment and advise so it’s not like they didn’t outsource such things before.
You guys have a typo. What you typed was you have one “reader” in North Korea. What you should have said is you have one “leader” in North Korea. I get it, though, pronunciation differences and all.
Assuming that wasn’t a typo though, I can tell you that reader is fearress…
I don’t think he’s a tech type of guy, maybe it’s his gf or nephew though.
The problem apart from censorship is also that the average NK citizen might not be too well versed in English I imagine.
Although it can be surprising with some countries in how many people speak English, if they for some instance made it mandatory on NK schools for some reason that would have quite an impact I imagine.
And you might think they would never do that, but then again you’d also not expect them to allow tourism, and tourism from US tourist. But they do.