Biometrics–the technique of using something unique about your body as a security device–promises to improve safety while being more convenient than a password. Fingerprints, retinal scans, and voice identification have all found some use, although not without limitations.
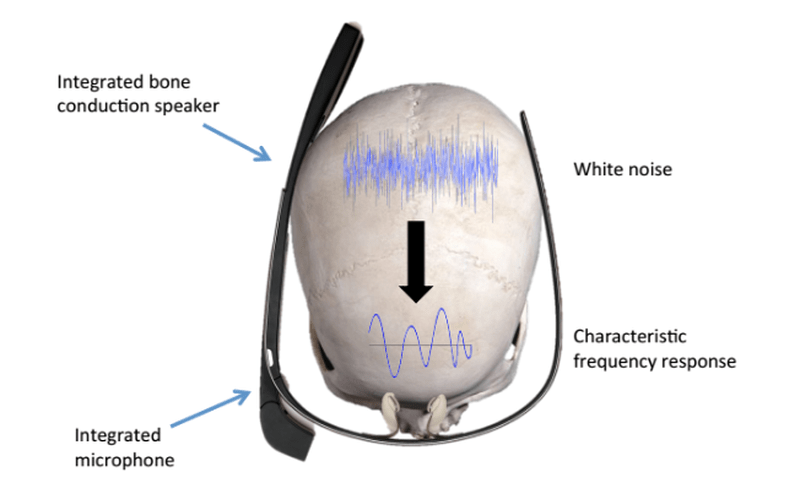
Now researchers in Germany want you to use your head, literally. SkullConduct measures vibrations of your skull in response to a sonic signal. A small prototype was successful and is particularly well suited for something you are holding up to your head anyway, like a smartphone or a headset like a Google Glass.
There are some limitations, though. For one thing, background noise can be a factor. It stands to reason, also, that more testing is necessary.
This looks straightforward enough that you could try your own version of it. After all, scanning veins in your hand has been hacked. We’ve even seen a biometric safe.















I don’t like people who criticize articles in the comments. HaD is awesome.
I do have to say though, that after reading several articles about how terrible and insecure bio security is, and providing very compelling explanation as to why, I am very surprised to see an article opening like so:
“Biometrics–the technique of using something unique about your body as a security device–promises to improve safety while being more convenient than a password.”
Constructive criticism is always good.
Promises have been made in the past, just like about any technology, and even though in biometrics are pretty crappy it doesn’t mean there can’t be anything new that would keep those promises, just because the current technologies have not delivered. Not that i think this will deliver.
The problem (as I learned from reading HaD) is fundamental. A password can be changed periodically, where as after bio security gets compromised, it remains compromised forever. If your skull data gets leaked? Somebody can fool the sensor to open your emails _forever_. You can change your password but you can’t change your skull (well I guess you could drill some holes in it, but i’d prefer to make up a new password).
The way I see bio is that it is ok for a username but not a password.
To be fair, a lot of the criticisms of biometrics seem to be focused on the wrong end of the problem. People say things like “what do I do when my phone is compromised and someone gets ahold of my fingerprint data? What do I do if it happens more times than I have fingers?” I feel this misses the point that not everything needs to be on the internet.
People criticize physical security hacks all the time, and talk about how locks only keep honest people out. But this is plainly false, as not all thieves know how to pick locks. The simple fact is that not everyone has the means or inclination to learn to bypass security that people on this site and elsewhere consider childishly simple. Consequentially, the requirement of geographical proximity reduces the pool of those with means, motive, opportunity, and *inclination* to defeat even a retina or fingerprint scanner is below the “background noise” people happily face every day.
Now, if all banks used biometrics then sure, a limited supply of fingers would be a huge problem. But for, say, unlocking a safe, for someone to defeat the protections they’d need either unrestricted access to the safe for long enough to just crack it the literal way; or to have followed me around, taken fingerprints or iris scans without my knowledge, and *then* got access to the safe. Finger-limited problems that wouldn’t be just as bad with literally any other security device won’t happen as long as I keep that safe OFF THE GODDAMN INTERNET.
To be fair, it’s not that easy to get a retina scan without the scanned retina noticing it.
Either way: Problem with todays biometrics is their convenience. Each and every fingerprint scanner is built to be convenient, because it would be massively annoying to have to put your finger onto the scanner multiple times, because you got the angle/pressure/position wrong. So, to make biometrics convenient, the scanners are made to have tolerances high enough to a point where they basically say “eh, close enough.” This means less precision. Therefore it’s easier to grab a fingerprint off a glass, scan it and etch it into some silicone formed to resemble or placed over a real human finger. Even if it’s not 100% matching, it’s still close enough.
It’s trivial to get a retina scan without the scanned retina noticing it. All you need is malicious or simply compromised scanner at some arbitrary legitimate scan point. Biometric security salesmen are all snake oil peddlers. No exceptions.
Bad example. Unless you wear gloves you leave fingerprints everywhere! You don’t need to leave your prints on the internet for someone to get them.
You seem to have missed the central point, that focusing exclusively on technical ease and difficulty of exploiting a vulnerability is not actually the same as assessing a risk within the larger context of your life. You’re thinking of security as an exercise rather than a means to an end.
Again, beating a fingerprint reader requires someone *near you* who knows this is possible and how to do it to identify you as vulnerable to that attack. This is nowhere near as common as you might think: if you can do anything with silicone besides maybe seal a bathtub you’re already on the opposite end of the Dunning-Kruger curve as most petty criminals.
Then, the criminal has to specifically decide to attack you. And *then* they have to actually acquire the print. This is easier said than done when it comes to smudge-heavy surfaces like public door handles. They basically need to either root through your trash or break into your house–both of which are already easier attack vectors in and of themselves–or follow your ass around town. We’re talking about a very, very different problem from a site getting hacked and your fingerprint data being obtained from the cloud/butt by one of the many millions of criminals worldwide. A fingerprint scanner on a portable device, let alone one inside your home, is plenty secure for the purposes of most private, individual Joe Schmos.
There’s still risk, sure. But there comes a point where security ceases to be a practical endeavor and becomes a form of recreation. There’s nothing wrong with that, but I have some kind of brain condition that makes me twitch when security discussion ignores context, or when for-fun theorycrafting tries to masquerade as commentary on universal best practice.
>“Biometrics–the technique of using something unique about your body as a security device–promises to improve
>safety while being more convenient than a password.”
I think the key word there is “promises”. Read that as you would for a politician, then it all makes sense.
I think this till needs to go into the same category as fingerprints – perfect as a unique username, not as a password. Once someone can spoof it, there’s no way I can change it to fix the security hole.
Well, no painless way…
As others have said, use this for username, maybe, but not password. Using multiple biometrics together might be safer. Of course it would also be less reliable, leading to them slackening the requirements and increasing false positives, for the sake of user convenience.
And you only find out about how it’s cracked, once people have a real motivation to crack it. Nobody’s bothered 3D printing a skull yet, or running this thing through a set of specially tuned panpipes, or a mic / speaker / DSP combination. But if necessary, they will.
Sure it keeps out the casual thief, but some thieves are more serious. Governments for one, sure there’s at least one government most people wouldn’t want running through their private stuff. Of course, for that, you’d use a known decent method, like a proper password with proper encryption.
Ultimately as far as requiring consent from a user’s mind, and not merely the presence of their living body, so far nothing’s beaten passwords. Quite possibly never will.
Perhaps a set of different biometrics AND a password, could supply a few bits each for a good key. And maybe some pass card or RFID dongle or the like.
“Biometrics–the technique of using something unique about your body as a security device–promises to improve safety while being more convenient than a password.”
I have the same comment about this as a few people had before me, biometrics do not improve safety, if anything, they can lower the security, because we cant change our biometrics when somebody runs away with our ‘skull resonation value’ (or fingerprint, or iris scan, or whatever)
I suppose you could use multiple biometrics, and if your, say, iris scan becomes compromised, remove that from the acceptable list, and require a password to replace it. Really though biometrics might work as extra security, added to a password, but can’t replace it.
Chalk up another “biometrics are not passwords” response. For a more expert opinion, I’d recommend Dustin’s blog at http://blog.dustinkirkland.com/2013/10/fingerprints-are-user-names-not.html
That said, even though the article equates this with a “security device,” it does look to be useful in having something like Google Glass automatically determine the user who just put the device on their head. This is using the skull to identify the user, and could help solve the issue with the original Google Glass being a one-user device. https://support.google.com/glass/answer/3297404?hl=en
Still, more like login, not password.
More often than not that’s the case anyway if you use your head :D
Really cool but I’d rather not use a password that makes the potential separation of my head from my torso a valid path to cracking :P
If you are dealing with someone who considers that a valid tactic almost any other security method will not hold up to scrutiny. (give us your password or my friend Sergei here goes to town with that hammer)
Turn the greatest problem into the solution.
Why not use the background noise to your advantage. Use a second microphone to listen to the ambient noise and either incorporate it into the calculation for frequency response or cancel it out of the answer.
This fails some basic security test.
Hash-able (maybe)
Change able (probably not, unless you put something inside your skull).
Fake able (Probably, using man in the middle electronics).
Unique (maybe, not a lot of research yet)
consistent (maybe, depending on the placement repeatably )
Basically if you leak the spectrum response, a digital adaptive filter can be applied to mimic the response and unlock the device Same problem as finger prints, facial recognition and other bio-metrics. It may be unique, but is probably not secure.
Better than a 5$ padlock, but worse than a password.
Especially for the suggested purpose of merely identifying the user it should suffice (if anyone got physically hold of your device you’re fucked anyways, better make sure there is nothing important on it).
I would even trust it for stuff like my car, if you can steal a frequency profile of my head, you might as well snatch the keys from my pocket (or just relay the keyless-go signals).
On the other hand, if the USAs thermonuclear missiles are biometrically-launchable it would trouble me (but still better than the “000000” password during the Cold War xD).
000000 so obvious they’d never guess it :D
Since this measures the vibrations of your skull to a sonic signal what happens if you get a skull fracture? That would change the resonance of your skull and your “password” would be invalid. Not only would you be in hospital with a broken skull you couldn’t get into your bank account to pay for treatment!
The inevitable “now that’s using your head” puns would get old within the first few minutes. Shortly afterwards, everyone would be driven into a murderous rage, thus reducing the number of password users by many orders of magnitude in a very short period of time and negating the need for strong security. It’s a self-solving problem.
Also, don’t play the game… It’s not worth it.
Usability would be a problem with this for years to come.
I have enough issues now getting users to just place their thumb flat and level on a fingerprint scanner to get into the door, much less scanning their skull with their smart phone.
(No, no, tweak it up a little bit so it makes good contact. yes, you need to remove your hat. here, just tuck it up under the hair line so it makes good contact. no, not like….*sigh*)