Discovered in 1997 by Aaron Spangler and never fixed, the WinNT/Win95 Automatic Authentication Vulnerability (IE Bug #4) is certainly an excellent vintage. In Windows 8 and 10, the same bug has now been found to potentially leak the user’s Microsoft Live account login and (hashed) password information, which is also used to access OneDrive, Outlook, Office, Mobile, Bing, Xbox Live, MSN and Skype (if used with a Microsoft account).
The bug itself seems to be present in all Windows systems since Windows 95 / NT, although only Windows 8 and above are effectively compromised. To see if your machine is affected, you may want to check the public demonstration of the exploit, set up by the guys from [Perfect Privacy] and based on [ValdikSS] original work.
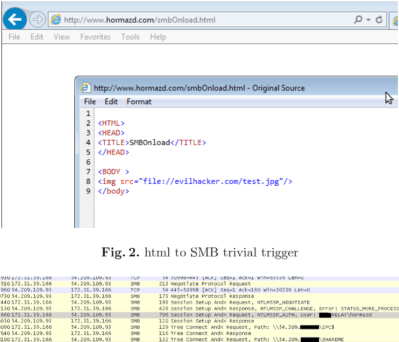
Basically, the default User Authentification Settings of Edge/Spartan (also Internet Explorer, Outlook) lets the browser connect to local network shares, but erroneously fail to block connections to remote shares. To exploit this, an attacker would simply set up a network share. An embedded image link that points to that network share is then sent to the victim, for example as part of an email or website. As soon as the prepped content is viewed inside a Microsoft product such as Edge/Spartan, Internet Explorer or Outlook, that software will try to connect to that share in order to download the image. Doing so, it will silently send the user’s Windows login username in plaintext along with the NTLMv2 hash of the login password to the attacker’s network share.
Even though the original issue exists and is known since more than two decades now, its severity has crept in only lately. Back in 1997, the attacker would have only obtained your local Windows login data, but in Windows 10, the default login method is the user’s Microsoft Live account. An attacker may have to resort to GPU-assisted hash-cracking to retrieve the password from the NTLMv2 hash (or even not), but the result can be as thorough as full compromise, including the mentioned Microsoft services and even remote access.
To mitigate, use a firewall, strengthen your Microsoft Live account password and avoid using Microsoft products such as Edge/Spartan, Internet Explorer (just saying..) and Outlook, as well as VPN connections over IPSec, which may leak VPN credentials in the same way. Firefox and Chrome are not affected.















1997 is three decades ago? Is this some kind of baker’s decade?
“…almost three decades…”
Pendant Fail!
1997 was still only “almost two decades” ago.
Derpa derp. :( I failed.
It sure felt like three decades…
Epic! But well, “almost”.
You just made me feel like I’m 35 in a flash! Good one ;-)
Pedant. Don’t leave us hanging.
lol
Sorry.
Took me awhile to swing back!
You forgot about the Y2K bug….thats where three decades comes from.
2 decades perhaps?
Yup, 22 years since WinNT
I think someone has reposted your article with no referrance to the author. Unless it was the other way round?
http://bertlandhope.com/microsoft-live-account-credentials-leaking-from-windows-8-and-above/#respond
That’s not the only one!
http://bertlandhope.com/infrared-flashlight-with-screen-uncovers-whats-hidden/
Funny story – I followed this link to the berlandhope site, and that’s how I found out my Ugly SMD Adapters have been written up on HaD today! I just happened to see the headline on their site while exploring the unbelievable fraud there. That’s really a problem.
This is probably a SEO site, like part of a really crappy PBN or something. It’s not really a real website though, it’s just sort of there and on autopilot probably reposting from an aggregated RSS feed.
Also found on that site.
http://bertlandhope.com/retrotechtacular-old-transistors/
Don’t know which came first, but interesting to see the copy/pasta.
http://bertlandhope.com/your-laundry-is-done/
That site is a copy-paste machine; just unbelievable.
unbelievable ? not so much. HaD bloggers themselves don´t create content, but aggregate content created from other people, without asking their consent to publish it, so what ?
I wrote this post. Please avoid confusions and allegations here.
This bertlandhope website appears IMO to exist only to sell advertising and steal logins + passwords from commentators.
And it does it using blatant copy-paste with zero credit to the original ‘blog post’.
I’m glad I’m not the only one who thinks this behavior sucks.
It’s been happening a lot in the last few months. I’m not sure if that’s a recognition of how awesome the Hackaday writers are, or something else. I like to think this is a problem you only have when the articles are awesome :-D
Thanks for pointing this out. I contacted them and asked them to stop.
Here’s my public issue demonstration if anyone is interested
http://witch.valdikss.org.ru/
And the article
https://medium.com/@ValdikSS/deanonymizing-windows-users-and-capturing-microsoft-and-vpn-accounts-f7e53fe73834
Thanks, I added the link to your the post!
Can you please change typo VladikSS to ValdikSS please?
Done! My apologies!
And this is on hackaday because…?
… someone can use it to hack your accounts. obviously.
But it’s not the hackaday that we all know and love. It was all about cutting down woods, building churches out of discarded materials, and exploiting one of pokemon go’s biggest cyber-vulnerabilities by binding down a phone to a fan’s propeller and letting it spin around.
http://hackaday.com/2016/07/28/log-splitters-hacking-wood-for-heat/
http://hackaday.com/2016/07/22/one-man-spends-53-years-and-builds-a-cathedral/
http://hackaday.com/2016/07/18/pokemon-go-egg-incubator-takes-your-eggs-for-a-spin/
You’re right! We should get back to the true meaning of the word hack! I’ll talk to Mike immediately. If it goes well, next week Hackaday will only cover model train content. Model trains, all day, every day. Choo choo!
https://en.wikipedia.org/wiki/Tech_Model_Railroad_Club
It wasn’t about the trains it was about the control systems.
I’m a model train enthusiast.
http://i.imgur.com/NRBtAbd.gif
Only if you get a PDP-11 to control your layout!
Because they care for their readers and want to warn a part of them.
Then why don’t we see every fatal vulnerability of MacOS/Linux/Android and Facebook/Twitter/Whatsapp, etc. here? What makes Microsoft Live so special?
Microsoft Live is special in this case, I believe, because it’s a bug that is still there that was there back in 1997. That’s really special.
Yep, and it’s so juicy. MS Account is used for, let’s see… Skype, XBox Live, Outlook.com, Office 360, MSN Messenger, Bing, Windows Phone, OneDrive, Microsoft Store… Everything pwned after visiting a website. naice.
the mistake is to think that this is a warning for the users. this is a hacking site, it is more like a tutorial or “how to” for inspiring the hackers. Why only MS ? maybe the media is biased and trying to manipulate us in a certain way. but you should feel to hack Android, Linux and MacOS as well.
HaD doesn’t cover all of Microsoft Live vulnerabilities. It is treated as any other vulnerabilities touching other systems. And there is article about vulnerabilities touching MacOS/Linux/Android/Facebook/Twitter/Whatsapp and even more. Check the tags associated with this article.
Please take a look at Hackaday’s actual coverage of vulnerabilities. You’ll find that it is highly diverse across platforms and applications. For example, see http://hackaday.com/category/security-hacks/ or http://hackaday.com/?s=vulnerability
Because this is a useful API for HAD users to use for cool hacks, good thing this API has been so stable through the years!
The vulnerability requires you use Internet Explorer as well. So if you’re using Chrome or FF, it’s not so bad of a problem. I’d say this is click-baity but Microsoft is also trying to cram IE down everyone throats again.
Funny, I’ve never had IE “crammed down my throat” and I’ve been a Windows user since Windows 3.0 came out. Windows 10 is not different, if you want to use something other than IE (or “Edge” as they’re calling it now), simply install your browser of choice and set it as your default.
I guess you don’t remember the 2001 U.S. v Microsoft antitrust lawsuit, then.
Yup, I do remember that. Funny how Apple was never sued for doing the exact same thing…
I also remember having no trouble whatsoever using other browsers on the Windows versions that were in use at that time. I think I used Netscape back then. No one was “cramming IE down my throat” or pressuring me to use it.
http://imgs.xkcd.com/comics/microsoft.png
And that is why I do not use MS products to surf the net!
Thought they are pushing Edge instead of IE for win10?
Yes, but Edge is just as vulnerable.
It’s kind of pathetic actually, every time you launch chrome, cortana is down there waving a little flag going “What about me, I’m a browser too!”
How many more bugs are out there that microsoft knew about and never fixed? This company is evil.
sed -ne “s/microsoft/${TODAYS_TECH_PUNCHING_BAG}/p” -e “s/evil\./full of humans\. Hanlon\’s razor, amirite\?/p” < your_post
But this won’t stop all you MicroSOFT-IN-THE-HEAD sheep from jumping at the headlines, pervading everything, that you need to “HURRY UP AND GET YOUR FREE VERSION OF WINDOWS 10 BEFORE IT’S TOO LATE!”
It’s okay, you can relax. No one will stop you from paying $100 for your copy.
Microsoft can’t afford to support all there “supported” Windows versions. They will continue to give away Win10 until the win7/win8 group is small enough to neglect. Microsoft is hell-bend on making there software rent-only, so if you buy now, you will end up paying twice.
Whatever happened to responsible disclosure?
I think 19 years probably satisfies most people’s standards for responsible disclosure. The only “new” thing about this vuln is that Windows now uses Live accounts for login by default. Meanwhile untold scores of Active Domain logins could have been leaked over the last two decades. (I’m assuming that’s what would happen if you’re on a domain account.)
It’s your own fault. Windows was never designed to be connected to a network (let alone anything like the internet), and despite Microsoft and other Windows software suppliers making it almost impossible to run (update, activate) there software without internet connection, it still isn’t and maybe never will.
Look for schools around your neighborhood, they might offer some basic security classes for you.
They’ve known about this sine 1997 and they haven’t fixed it yet? Well maybe they’ll get on it once they update “BOB”.
That might explain why MS pushed so many updates and patches that are related to SMB, Netbios, shares etc last month.
Most of them cause pain in the a$$ in enterprise.