As we’ve mentioned previously, the integrity of your vehicle in an era where even your car can have a data connection could be a dubious bet at best. Speaking to these concerns, a soon-to-be published paper (PDF) out of the University of Birmingham in the UK, states that virtually every Volkswagen sold since 1995 can be hacked and unlocked by cloning the vehicle’s keyfob via an Arduino and software defined radio (SDR).
The research team, led by [Flavio Garcia], have described two main vulnerabilities: the first requires combining a cyrptographic key from the vehicle with the signal from the owner’s fob to grant access, while the second takes advantage of the virtually ancient HiTag2 security system that was implemented in the 1990s. The former affects up to 100 million vehicles across the Volkswagen line, while the latter will work on models from Citroen, Peugeot, Opel, Nissan, Alfa Romero, Fiat, Mitsubishi and Ford.
The process isn’t exactly as simple as putting together $40 of electronics and walking away with a vehicle. The would-be thief must be close in order to detect the fob’s unique key — although they only need to do so once for that vehicle! — as well as reverse-engineer the other half of the code from the vehicle’s internal network. Exploiting HiTag2’s vulnerabilities to unlock the vehicle can be achieved within a minute by a well-prepared thief. [Garcia] and his team note that only the VW Golf 7 has been spared from this exploit.
If thievery is not your thing and you’re looking to white-hat hack your vehicle, Volkswagen still has the best option in the form of the loveable Beetle.
[Thanks for the tip therafman!] Via [Wired].















Looks like some car drivers will have to go back to Mr. Beaning it.
https://drkokogyi.files.wordpress.com/2011/10/mr-bean-army-cadets-mini-car-8.jpg
I think I’ll stick to my bicycle: No remote locking or CANbus for the blackhats to hack!
and the basic basic bike is not worth stealing so you dont hear of bike theft much except for the more expensive ones
You probably don’t live in Holland? :)
Yoo Bro. Kan je zo’n apparaatje in mekaar zetten? Enige ervaring?
You must not live near a pub.
Great idea. And to at least keep *some* of the convenience, use a smartphone controlled padlock!
You did see the recent article on how terrible bluetooth locks are, right?
VW halts production today
My car had IR remote locks. I was able to get through with a learning IR remote app for a palm pilot. Removed the receiver for safety.
thing is that the IR remote has such limited range that you’d be able to detect someone sniffing your signal very easily. Its actually quite a secure solution in that regard.
Again and again, people fall for the trap of “limited range” of security-critical devices. This has to stop!
The cheap FOBs they can put on your keychain have limited range when combined with the cheap sensor they place inside the car. With radio waves, a parabolic antenna and a good amplifier will allow you to extend the range enormously. In the case at hand, some optics will probably allow you to gather many more photons allowing a decode of the signal from much further away. You might argue that someone with a big parabolic antenna pointed at your car will raise suspicion. Maybe. Maybe not. Some materials are transparent to infra red and not for visible light. So put the parabolic receiver in a suitcase with one side replaced with IR transparent fabric and the device is concealed.
I recall on my 2004 volkswagen jetta (sold now) I improved the range of the fob dramatically by putting a bigger antenna in the car (pulled some wire through the A column, behind the trim work) I do not recall doing anything to actually tune that antenna… I got more than halfway across the parking lot with that new antenna… and it was just an extension of some automotive grade wire.
A well designed well tuned antenna would probably have given me a range of the whole parking lot, with no modifications to the key fob… a directional antenna might have gotten me even further (so long as I always approached the car from the same direction the antenna was pointed)
If an improvement on the receiver can make that big of a difference then the attacker can get that same advantage on their receiver.
They can also seek out high ground and line of sight on the location they expect the fob to be pressed at… or just put a drone up over a parking lot around bar close, or when work gets out at an office building… lots of people leaving lots of fobs being pressed, those cars are likely to return to the same spot another time when you can just unlock them and drive off… (or just take any valuables that were left in the car… I’m sure hanging around bars near the infinity loop complex at 5-8pm would yield a number of laptops perhaps with confidential information on them…)
Yeah and they can then steal your 1970’s clunker.. I bet they are soo eager.
You might as well steal a volkswagen then, if you have such low standards. ;)
I think you might be surprised to learn that some 1970’s VW clunkers can go for quite a bit, especially the 21-23 window 1970’s VW busses which can go for over $100,000 depending on condition. And while it was a movie car, it wasn’t terribly long ago that a 1963 VW beetle sold for 126,500 at auction.
As a counterargument I could say that it’s very hard to auction a stolen car, especially a ‘classic’.
Also I have a question: Do they keep the old poor security features on classics? Because then all of them should be easy to steal right? I mean if I owned a classic worth 100 grand I’d disable the easy to copy IR door opener for sure, but is it then still a classic? And that’s an IR thing which you can disable, but what about locks that were found out to be piss-poor, would you have to keep those to not lose the value?
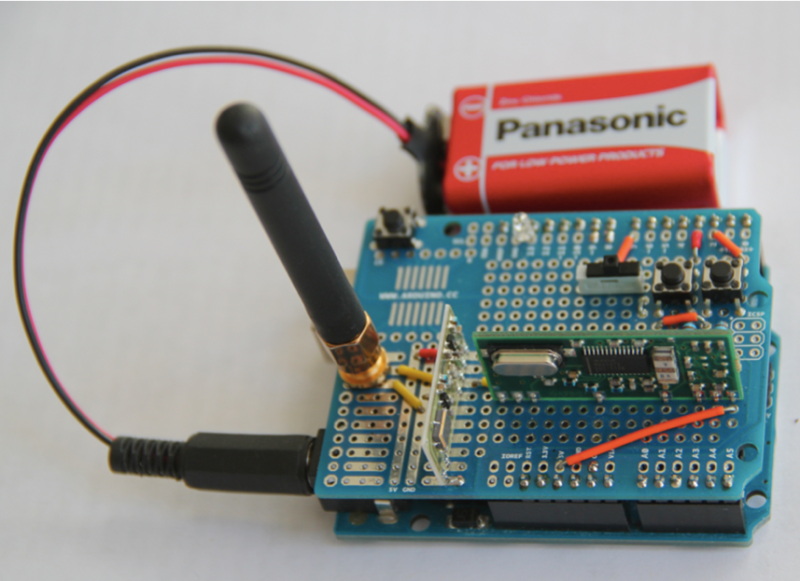
How did they make the SDR shield?
There’s three things involved:
1. The Arduino “motherboard”
2. The RF fronend PCB, which is the brighter PCB. You can clearly see the RF oscillator close to the camera on that board. If I had to take a guess, that’s an SILabs adjustable RF LO. From what I can tell, the antenna signal is probably simply amplified by the black little transistor, and mixed with LO by the other transistor, probably leading to a low-IF signal (IQ would need two signal lines, which is fed to the yellow cable going behind the
3. green PCB which looks like a ADC demo board with its standard oscillator and a SSOP28 Maxim IC.
They’re just basic off the shelf RF transceiver modules. Most of the systems just use ASK or FSK which is precisely what those modules are used for anyway.
It isn’t SDR. They used a SDR for initial investigation but the Arduino setup is using two off the shelf RF modules.
Ah! Thanks for the clarification
Yah, I came here mainly to see what the heck an Arduino could possibly have to do with SDR. There isn’t enough processor power in an Arduino to do SDR and using an Arduino to control some other device which does have the processor power just sounds silly when said device has more than enough power to control itself.
People still buy VW’s?
The old 60’s era bus are still popular. ;)
Not *any more*, now we just ‘borrow’ someone’s when we need them
you do realise the immo function is sepeate from the keyless entry dont you?
The immobilizer on VWs at least up through the A4 platform is RFID or similar mostly iirc. With A4 fobs, if you were crafty enough you could actually remove the programmed chip from an old and broken key and place it in the fresh new one to skip the ~$250 unjustifiable programming fee that VW charges.
I’ve done this, actually. The programming sequence for the ECU is stupid simple and can easily be found on the internets.
This reminds me of Bastian Bloessl’s excellent presentation on how he opened his VW in 2015, and how he rolled that into the GNU Radio gr-keyfob module
– https://www.bastibl.net/gr-keyfob/
– https://github.com/bastibl/gr-keyfob
– https://www.youtube.com/watch?v=EkRZiFSoSZk&list=PL6D0CPBQoIVpGesCCezfOfPZ6a7b-QEan&index=11
ARDUINO + SOFTWARE DEFINED RADIO = MILLIONS OF VULNERABLE Volkswagen, Citroen, Peugeot, Opel, Nissan, Alfa Romero, Fiat, Mitsubishi and Ford.
The details are different between VW and the rest. More viruses are written to target Windows.
Opel ak GM
Opal = Vauxhall for us Brits.
And Opal =/= Opel = Holden for us Aussies.
The $40 Arduino setup isn’t using SDR. The paper mentions they did use SDR equipment like a HackRF but that appears to only be for initial investigation. The Arduino setup they’re using however just uses off the shelf RF transmitter/receiver modules instead as the actual transmission mechanism for most systems tested was just simple ASK or FSK. The “security” came from the code being transmitted itself which as the article points out, isn’t very much security at all if you’re able to sniff it with basic equipment.
TL;DR No fancy SDR is needed. Programmed Arduino + basic RF transmitter/receiver modules are sufficient to sniff and clone the remote entry on a ton of cars.
Clearly not a good thing, but, in the scale of things, it’s also not the worst. It’s not like the inside of a VW would have been as secure as a bank vault in the first place. A broken spark plug insulator can open any car!
I was a firefighter and frequently taught using an auto-centerpunch some of us carried in our turnouts pocket to pop windows like a dropping waterfall before we sawed and snipped the vehicle to pieces. I never actually tried it but why is there this assumption that a shard of sparkplug ceramic is better than anything else at breaking windows? It is spoken of as though it were kryptonite to tempered glass windows.
@dave,
Probably because vehicle windows are surprisingly tough to break without a focused point of impact. A blunt object, like a kick with a shoe, requires much more force to break than most people expect.
And this is why I still drive my grand-dad’s old ’58 Fairlane Station Wagon. The most advanced piece of electronics in the thing is the capacitor / transformer circuit to generate the current for the spark plugs… There is that, and if something breaks, I can fix it with $50 in tools I got at the local auto store, the Haynes manual, and ~$120 in spare parts and spare fluids.
It might get crap for gas mileage, but at least I know no one is going to be able to exploit the Bluetooth connection in the radio and activate the brakes. I don’t have to worry about someone stealing it, its a very noticeable car that the police would have no difficulty in finding (How many Olive-green classic station wagons are there in the world?)
And this is why im still using a horse, no transformers/capacitors that can break.
That’s why I’m walking by foot, no horse that can get sick.
That’s why I still swing from tree to tree, nothing that can hurt my feet.
This is why I dont leave my house, no feet to stumble, no diseased people to meet, no cars to run over me, no CIA agents to put probes in my brain…
I wonder what’s easier?
-Learning that a particular car has a vulnerability in its wireless unlocking method, deciding to exploit that, buying an arduino + other hardware needed, learning some basic programming, downloading the sketch or writing your own, finding an appropriate car, waiting for the owner to arrive to unlock it, capturing the data, decoding and interpreting the data, reusing the data to unlock car, then being disappointed when all you have to show for your efforts is a travel pack of chewing gum and some wet wipes after realising that just because you’ve unlocked the car doesn’t mean you’ve over come the immobiliser.
-See any car, see rock, pick up rock, throw rock at window. If old car with no immobiliser drive off into sun set. If the car is old enough you don’t even need the rock, my brother could open his 1967 Mini with a wiggle of his school locker key. If you want to make less mess/noise than with using a rock, then a plastic pry bar and a bent copper pipe is all you need to get into a car with flimsy door frames.
Actually the rock vulnerability is still a limited attack vector on a modern VW.
Will only yield partial access to the interior. The default locking mechanism when when activated by the key is “dead locked” which means you can only obtain what is within reach.
My older SAAB fell victim of the rock attack on a rear side widow the perpetrator then only needed to reach through and unlock the front door and remove my ashtray. Cost more for a new window than the couple of dollars they scored :(
If what you want is sitting in view on a seat than rock will be sufficient but if it’s in the boot or even under the seat out of view and out of reach the rock just became somewhat limited.
Heck I drive a convertible these days (SAAB of course) and I often don’t even bother with putting the roof up – just keep things out of reach and dead lock activated ( then yes they will need a arduino and radio modules and capture my key code )
My wife’s vw is a ute and what ever is of value is probably sitting in the open tray :lol:
Agreed Saabman but I was more referring to CA’s comment after my smug meter went off the scale. Trying highlight the fact that having an old car may make you invulnerable to such attacks as described in the article but it would still be easier to break into an old car with proven less sophisticated means.
Note that the cryptographic key that is extracted from the vehicle is same for all vehicles with same generation of the Rf protocol, thus the attacker has to do the reverse engineering part only once for each generation and then has to capture what is essentially an username (as 32bit ID) from the keyfob. Brute forcing that 32bit value over 1-2kbit/s link is not practical, but i think it’s pretty much safe to assume that these values are at least somewhat predictable (eg. assigned sequentially).
The VW engineers may end up calling this open source. Unlike the diesel engine code where you get the magic of high mileage and low emissions from simple software trickery. Long live SDR.
I think the diesel thing was actually a misunderstanding by VW, they didn’t try to hide it at all. Look up a youtube video of a dyno test, a two wheel dyno test of a tdi makes the front panel act quite odd.
The key fob unlocks the car, but there’s another RFID chip that enables the car to start. The physical key is needed to start it.
So thief can’t steal the car, but can steal anything that’s in the car. Still a big security issue.
The one part is a man in the middle attack that jams the receiver to always keep a current (valid) rolling code.
My 2003 VW Polo is immune. It doesn’t have remote unlocking. I actually have to put the key in the door and turn it! Radical!
The solution can not be to go back to stone (or at least bronze) age. Good cryptography exists and shall be used for such a system.
Point is, if you avoid these silly devices that enhance consumer laziness, your security issues start going away.
Of course there is no coolness in reducing risks by simplifying.
How the heck they put the SMA connector to the protoshield?!
Let me guess that low range savers. If i park a car, or maybe i pretend to go to a parked car near a VW when the owner is coming out, or maybe i just want to go that way between the cars. Im not aware of any law that stops me from walking half a meter of someone that gets out of a parked car…
Is it difficult to conceive for you? because for someone that steals, walking closing to someone doesn’t seem so hard.
No thief would use this beacuse generic jammers are a much easier way to get into cars. Jam the signal while the driver is walking away and thinking he’s locking the car, then get into the unlocked car and take anything.
Although the jam vulnerability isn’t as reliable, it would be a nuisance for thieves to have a separate device or code for each manufacturer.
For outdated systems, it would be best to upgrade to an aftermarket FOB with a rolling code and always make sure your car actually locked before leaving it.
Lmfao, My 2008 VW is poverty spec and hadn’t got central locking. So i guess im probably o.k as far as this hack goes.
I have seen news articles on a Faraday Cage to protect your car from this type of Hack. I went to Amazon and found a Key Fob Guard called the Fob Keeyper for $17. I was skeptical at first, but it really works. No need to keep your keys in a metal cage or the freezer!
Here’s the link to the product on Amazon: https://www.amazon.com/Guard-Keeyper-Blocking-Pouch-Faraday/dp/B01FYVWVX8/