FireEye just put out a report on catching the Russian hacker group “Advanced Persistent Threat 29” (APT29, for lack of a better code name) using the meek plugin for TOR to hide their traffic. If you’re using meek with meek-reflect.appspot.com, you’ll find it’s been shut down. If all of this is gibberish to you, read on for a breakdown.
meek is a clever piece of software. Imagine that you wanted to communicate with the Tor anonymizing network, but that you didn’t want anyone to know that you were. Maybe you live in a country where a firewall prevents you from accessing the full Web, and blocks Tor entry nodes as part of their Great Firewall. You’d want to send traffic somewhere innocuous first, and then bounce it over to Tor, in order to communicate freely.
That’s what meek does, but it goes one step further. The reflector server is hosted using the same content-delivery network (CDN) as a popular service, say Google’s search engine. The CDN has an IP address, like every other computer on the Internet, but it delivers content for any of the various services it hosts. Traffic to the CDN, encrypted with TLS, looks the same whether it’s going to the meek reflector or to Google, so nobody on the outside can tell whether it is a search query or packets destined for Tor. Inside the CDN, it’s unencrypted and passed along to the reflector.
Anyway, meek was invented to help bring the uncensored Internet to people who live in oppressive regimes, and now cybersecurity researchers have observed it being used by Russian state hackers to hide their tracks. Sigh. Technology doesn’t know which side it’s on — the same backdoor that the FBI wants to plant in all our communications can be used by the mafia just as easily. Plugins that are meant to bring people freedom of speech can just as easily be used to hide the actions of nation-state hackers.
What a strange world we live in.

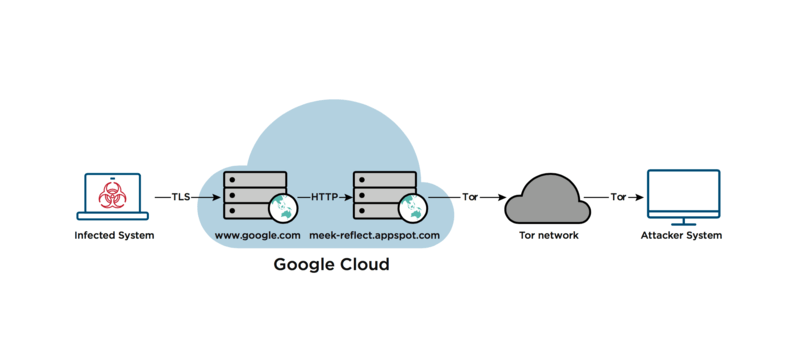














I notice at the end of the connection diagram is an “attacker system.” It could just as easily have been a “free speech site.” I see which side of the issue you’re coming out on. Technology is neutral, it can be used for good or evil. The same arguments can be made for encryption, it’s ok when the government uses it but everything else must be unencrypted so they can monitor our communications.
The diagram is from FireEyes article.
Yet again HAD is being attacked for REPORTING what is said. DID YOU LOOK AT THE FIREEYES POST!
Or maybe the diagram ends with an attacker system because the article is about how such a great tool was being used by hackers. Almost half the article is about how this tool was meant to facilitate free speech, and literally contains the quote “Sigh. Technology doesn’t know which side it’s on” which I read as meaning that tech cannot know if it is being used for good or evil.
Granted, I disagree with the idea that technology is perfectly neutral, but that is a whole other issue than you failing to read well and accusing hackaday of being biased.
Your own logic could equally apply to the WikiLeaks claim just as easily. You are trusting the source stating it is or isn’t the Russians in either case…and making a generalized conclusion as a result.
I trust neither source 100%, which is rational I hope given how difficult Internet source attribution can be. That said, neither Russians nor CIA would want their activities discovered. I think it’s highly more likely the that they would both have remote resources out of country to launch attacks or simply pivot through other systems that are compromised. At least I think erasing your tracks from such a system and giving a false impression of source attribution is simpler and more likely than going out of your way to plant evidence…at least for the majority of use cases.
When they outlaw computers, only crakers will have computers.
Sounds racist…or salty
I’m still not sure how you can define uncensored internet. It’s a relative concept.
Well, by now the reasons of transition from (D)ARPANET to the Internet are abundantly clear. Instant spying by able (governments, mafia, script kiddies) on clueless (plain folk).
Right, because the illuminati minds behind the internet could see from the outset that it would become a huge success and network the entire world together. Meanwhile, Bill Gates was publishing his “The Road Ahead” treatise on how the CD-ROM was going to revolutionize computing, with products like Encarta.
The stupidest conspiracy theories are the ones where shadowy government cabals are assumed to have foresight that matches the theorist’s hindsight.
I’m telling you, Joss Whedon caught onto it 17 years ago…
http://www.imdb.com/title/tt0533477/quotes?item=qt0251430
I mean think about that for a moment, perfect clarity of insight that the 3 largest threats to mankind would one day be IoT, AI and Keurig/Tassimo machines needing an area the size of Texas to bury their waste pods weekly….
… and they’re converging into one appliance!!!!111oneoneone
Of course Joss had to stick it in a dream sequence for plausible deniability when the black helicopters turned up, but still.
Real problem with backdoors is its mainly the bad guys who want them, and the sorry individuals who are deemed bad guys by the bad guys.
s/Internet/Books/g
The fascist agenda should then be very clear.
Without control of information/education bias, a populace will fail to reach a coherent political consensus. Internal unresolvable conflicts will often arise, such that every despotic power in history must eventually implode under their own propaganda, misinformation, or outright wars.
In such systems, criminals who leverage a system for economic purposes are indistinguishable from political opposition targeted by intelligence agencies.
The error is assuming a political problem is a technical one.
s/Iam/soclever/gaClPBlZiT42069.sonic.exe
APT29 has a better code name, it’s also referred to as “cozy bear”, not proven to be a state sponsored group but often alleged to be a russian state sponsored group. The fact that they were using a Pluggable transport for TOR just shows that they were trying to remain anonymous while doing their hacking.
The bigger issue I see here is that Mandiant has claimed to have been watching them do this for over 2 years while keeping their ability to see this a secret. Tor is used for good things as well as bad but the fact is that it doesn’t really seem to do its job anymore as there are constant attacks on its vulnerabilities trying to find ways deanonymize the people who use it. the troubling thing to me is that almost all of the attacks have come from the “free” nations that should be supporting it.
When every hack attributed to Cozy Bear aligns w/ Russian government interests it’s highly unlikely they don’t have some ties to at least a portion of the Russian government.
Irrelevant.
I’m talking about whether APT29/Cozy bear is state sponsored not making some grand moral judgement on them for doing it. Besides are you really surprised a spy agency like the CIA is spying on people? Isn’t that what they get paid to do?
>>Prove they are “state sponsored”.
HAH.
The same people who attribute Stuxnet to the US & Israel say these guys are probably Russian Intelligence but you don’t believe them?
If these guys aren’t state sponsored they should be. They’ve got the skills for it. It’s a bit strange that they heavily target Russian interests if they aren’t at the very least, occasional government contractors.
https://www.f-secure.com/documents/996508/1030745/dukes_whitepaper.pdf
As well as Kaspersky’s analysis of their older exploits these are non-native English speakers that are familiar w/ the Cyrillic alphabet, and like to work between 0600 – 1600 (sometimes 1900) GMT.
https://securelist.com/blog/incidents/64107/miniduke-is-back-nemesis-gemina-and-the-botgen-studio/
Finally someone with some sense.
It was an Israeli-American effort that coordinated say, stuxnet.
But we like to pretend they obey the US charter…
I’m not going to say that cozy bear is not somehow aligned with the russian state but given the number of times that the US or its allies have cracked TOR open do you really think the russian government would use it for state spying purposes? Some of the evidence shown that they are state sponsored points more to a lack of technical ability then the russian government has.
Hmmm the argument there is similar to saying, since we’ve been to the moon and cracked gravity, we should all float off into space. Yes with large effort the thing can be done, but it’s not done all the time, and not done “permanently”.
It’s still “camo” in the time of thermal imagers, it’s not a 100% cloak, but you still use it as part of your attempt to be low visibility.
AFAIK TOR is still vulnerable to correlation attacks and they have been around 10 years or more so thats pretty permanent in computer time, there was a university in wisconsin that showed most of the pluggable transports had vulnerabilities a year or 2 back including meek. So the question stands, why would the russian government use systems they knew their opponents owned in such a shoddy way when there are better ways to do it with infrastructure that you own?
Yah but you need x volume of recognisable traffic, like being daft enough to webrowse popular sites while you do the blackhat shennanigans.
It seems to be amazing how well it aligns… almost like someone wanted us all to notice. Which means it’s really the CIA. Or China. Or the Ruskies are double-bluffing us.
I tend not to think of it as the govt per-se but more like one of the mafia-criminal-political-oligarchy factions, either in it for the money, the power or hard communist ex-KGB splinter… and they’re all pulling strings in govt somewhere.
I think there’s various hookups with the more purely commercial Russian criminal hacker groups, but they may be fiscally based as required, or used for diversions.
Heck come to think of it some of them are so purely commercial I bet the CIA can hire them.
TLS through design provides no protection from state actors. Many CAs are run by governments, which can sign certificates for any website or even any top level domain, which are totally 100% legitimate and valid in every respect. Then they can MITM the whole communication in plain text (https in effect becomes http). Every CA can issue a valid certificate for every domain.
The whole security of encryption used on the web is broken by design.
If you are a (possibly state sponsored) high profile hacker, you won’t rely on a CA to validate a cert that important. You’ll check it manually.
It was suggested to me by a friend that the reason TOR is use-ably fast is because the FBI runs “half the nodes.” Supposing that comment somewhat reflects reality (I have no idea), wouldn’t using TOR for illicit reasons such as hacking be a liability, regardless one’s use of meek?
only the last node (be it a hidden service or an exit node) can see the traffic unencrypted.
as long as your destination is inside tor (i.e. a not compromised hidden service) your communication should be safe (standard caveats apply). where the three letter agencies could intercept traffic is at the exit nodes (if it doesn’t use tls or they can’t mine a cert for what ever reason), as an exit node is essentially the last server of the route inside tor.
“standard caveats apply”
i.e. the assumption that the majority of the inside nodes are not under centralized control…
i.e. exactly the premise of user Robot
If you live in an oppressed society you don’t need things like TOR, what you need is a tunnel to a proxy in a safe haven where you can trust the operator with your identity. This is the key different, total privacy can and is abused, having “good” friends help you is a very different set-up but just as effective at protecting the rights of people.
I’m surprised that the NSA, CIA et al don’t offer proxy and VPN services for free on the understanding that they can monitor everything you do, but will otherwise protect your privacy and give you access to the entire web without restrictions. If all nations who were lovers of freedom (in it’s different forms) offered such a services there would be a huge benefit to the oppressed while giving very little advantage to criminals and pathological state entities.
I imagine if you’re worried about your state, you might not trust another. Also, if you’re in, say, Iran or China, using CIA-proxy.com is probably not going to make you safer…
The CIA is no threat to freedom loving individuals in China, or Iran, their own governments are, that is the point.
Furthermore they need not be so blatant about it and there are many other countries that can help to form a securely authenticated mesh of tunnels.
You sir are an embarrassment to all who call themselves Dan, not to mention adults in general.
The CIA is no threat to freedom loving individuals in the U.S. either…….. They get the Brits or Aussies to do it.
LOL, actually it is the New Zealanders who spy for those guys who then hand it over to the CIA. Those sheep lovers have been pulling the wool over everyone’s eyes for decades.
US government orgs like the NSA sponsored Tor (used to be listed on Tor’s site), and run nodes.
But of course not for freedom, which is something they aren’t a fan of really, but to ensnare foreigners (and locals) into using it and then snoop on those that think they are safe (the US government also purposefully pushed weaknesses into it it was revealed).
I think they also own a few VPN services, but probably through shell corporations.
You are only at risk if you are using the web for activities that would allow you to be compromised, but then that is a risk you face no matter what system you use.
I am talking about people with a genuine need and a benign motivation, not deviants who just want to hide in the shadows.
If you just need to get news in and out of your country then all you need is a service that lets you do that safely and that requires authentication by a third party that you do trust, so if you are genuine and paranoid you can use a Dutch service, or whatever, whoever you do trust, and if that is nobody well then you are screwed anyway you do it aren’t you?
It was a Dept of Navy Project. For the purpose of protecting online military communication.
It’s now a completely separate Tax exempt 501(c)3 Charity.
As for intentional weaknesses I’m not sure if you’re talking about egotisticalGiraffe, which was just a 0-day on the browser bundle, or the weaknesses inherent in onion routing as a mechanism.
Neither of which were maliciously introduced.
I was talking about the deliberate weakening of the randomness, which was documented.
As for the other commenter: The dutch? Really? Is that a joke? The Dutch are really not reliable and very VERY VERY good friends of US ‘security’ services and the leadership is on call for various US think tanks.
And as for being ‘at risk’, I remind you that most all of the US leadership has severe mental issues, I’m talking about congress and various committees as well as the white house. And the US (like so many countries) has a long history of not exactly having a solid grasp of the concept of justice and fairness.
And reportedly the spooks found that many foreign diplomats used Tor, and in doing so not only revealed juicy information but even passwords/logins, so that’s all wonderful stuff for the NSA/CIA and a good motivator to support it. But of course over time there were various stores about the hacking of Tor by the spooks and FBI and whatnot so I guess even most of those silly diplomats now know better and it’s less interesting for the feds to support Tor.
We ARE aware that it’s dead easy for US ‘state actors’ to spoof being from anywhere they want right? China, Russia, Iran, you name it.
So be careful assuming, especially if those same US ‘state actors’ are the ones determining where the hacks came from.
It would be very inefficient for a US agency to attempt to compromise (from Russia) US military networks, the DNC, and US based NGOs when they could get a FISA or standard warrant for any of them that they didn’t have access to as part of their daily work.
Also much of this attribution was done by Moscow based Kaspersky Labs. Seems odd for a Russian company to blame Russian hackers for hacks against the US military & political networks. Unless Eugene Kaspersky is some cartoon villain trying to kick off WWIII.
Sometimes things are as they seem.
It would in fact be the ONLY way for US agencies to do so since obviously hacking the DNC or RNC by US agencies would be a huge no-no. Plus it seems clear from various hints that the leaks were insider leaks.
As for Kapersky, the owner of that was arrested for taking bribes from the US last I read right? Now that is hard to judge if it’s true or not from our perspective, but it would make sense that the US security apparatus with its huge budget would try to exploit the general susceptibility of people for being willing to take bribes. And that Kapersky management would be a good target for such efforts.
As for all the supposed Russian hacks: I now notice on Reuters that they actually suddenly say it were the Russians that hacked Sony back then. Which at the time the US said was 100% proven to be North Korea.. They now even travel back in time with their fanciful stories. Next week I’m going to read about historians telling me the KGB killed jesus I expect.
Can’t seem to find anything about bribery, it’s just vague treason charges, which are apparently pretty common in Russia lately. Incidentally for actions taken before joining Kaspersky, nor is Kaspersky implicated in the crimes. He’s also not the owner.
https://arstechnica.com/security/2017/01/kaspersky-labs-top-investigator-reportedly-arrested-in-treason-probe/
http://www.businessinsider.com/ap-top-manager-at-russian-cybersecurity-firm-arrested-in-moscow-2017-1
I can’t seem to find anything about bad randomization in Tor node selection. Do you have a link to this bad randomization attack? There are some ways to DOS the network so only your nodes stay up, but that’s not really a randomization problem. One of the common ways to DOS nodes was fixed in 2014’s Ver, 0.2.4.18-rc.
Actually, if I’m surprised about hacking from anywhere, it’s North Korea… I just can’t believe their education and restricted tech availability can produce the skills.
Im assuming here but they probably get training in china with something like PLA61398 or whatever its been replaced with these days, Are the putter pandas still around? maybe they are on training duty now when not on the links.
So could it be detected, if the website you’re trying to access is down even though meek is used?
‘double squares’ is a pretty new commenter… still deciding if he’s a masked troll or just a negger. Seems to attack other commenters when voicing an opinion. Calling out Dan or the other person a few days ago doesn’t add to the conversation (oh the irony).
Technology is always going to be used to serve someones agenda. Whether its finding a cookie recipe, suppressing thought or turning a profit. Being aware how it can be used, maliciously or otherwise, then deciding how much you give out should be in Computers 101.
Being so focused on the source (real or planted) means that the message often gets drowned out.
” so nobody on the outside can tell whether it is a search query or packets destined for Tor.”
Well, anybody not looking at the metadata… Its very obvious from just looking at the packets are destined for somewhere else, a query isn’t going to be more than 256 Bytes each and less than a few KB each minute. Communicating with CDNs is one of those things that follows a very definite pattern, small amounts of traffic from the client to server, but a massive amount of data from the server to the client. The data on CDNs tends to static or at least the uploads would be coming from a single other server within the same domain (EG, users upload content to upload.domain.tld and its served up from cdn.domain.tld).
The concept behind meek isn’t going to work all that well if its trying to hide from well-funded and determined adversaries. Its essentially a zero-day attack for spies: the method only works until the adversary is made aware of it. In this case, someone like the NSA could watch traffic going to CDNs and find anyone sending more than the average amount of data to it, then its a matter of recording the packets coming out of that CDN (which in this case are unencrypted), match up the sizes / frequency / etc and not you have that person’s data stream without needing to tap their lines.
Its the same issue that has befallen TCP-over-DNS tools, a proper network monitoring tool would alert on a user making multiple megabytes worth of DNS queries with very few, if any, being in the cache. Or the tools could monitor for suspiciously low TTLs on the query results. On my network, if your cache-hit percentage drops too low, the DNS server will no longer respond to new queries for that user and instead just go into a cache-only mode (IE if the DNS entry they want isn’t in the DNS cache, the DNS server isn’t going to bother resolving it).