We’ve all heard of card skimmers, nefarious devices that steal the identity of credit and debit cards, attached to ATMs and other machines in which unsuspecting consumers use them. Often they have relied on physical extraction of data from the card itself, such as by inserting a magnetic stripe reader in a fake ATM fascia, or by using a hidden camera to catch a picture of both card and user PIN entry.
The folks at Sparkfun write about an approach they received from a law enforcement agency bearing a selection of card skimmer devices that had been installed in gasoline pumps. These didn’t rely on interception of the card itself, instead they sat as a man-in-the-middle attack in the serial line between the card reader unit and the pump electronics. Let that sink in for a minute: a serial line that is readily accessible to anyone with the pump manufacturer’s standard key, carries card data in an unencrypted form. The owner of the skimming device is the criminal, but the company leaving such a wide-open vulnerability should really be joining them in having to answer to authorities.
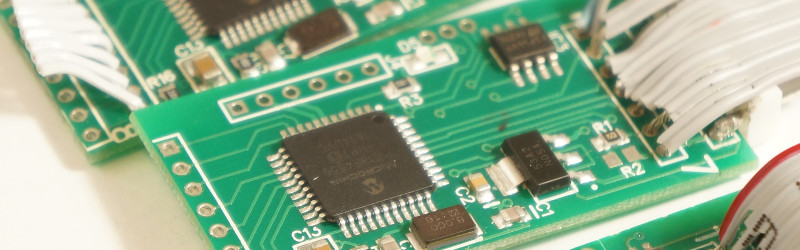
The device itself is quite simple and well-executed, though it appears that attachment of wires and connectors is a job left to the crook. Some boards boast excellent soldering, while others have joints that are, well, simply criminal. On the board is a PIC microcontroller, a serial Flash chip, and a commodity Bluetooth module. This last component provides the means for the miscreant to harvest their ill-gotten gains, and incidentally a handy means by which compromised pumps can be identified. The Sparkfun people have provided an Android app that interrogates any modules it encounters, and warns of any that return the signature of a skimmer.
It is sad to say that some level of crime is an inevitable feature of the human condition, and therefore it should not be an unreasonable expectation that any entity with which we trust our sensitive data such as a credit card number should take reasonable steps to ensure its security. If a bank transported customer cash through the streets as bundles of $10 bills in open handcarts it is likely that they would get into trouble very quickly, so that the pump manufacturers send card information in the clear over such a readily accessible medium should be a scandal of similar magnitude. That financial institutions prefer to cover up the problem and shift the loss onto the gas stations rather than mandate better device security from the pump manufacturers speaks volumes about their misplaced priorities.
If this topic interests you, we’ve shown you a teardown of a more traditional skimmer in the past.
Thanks [CYK] for the tip.















A few years ago I noticed the same kind of thing at a Sonic’s burger joint. There was an access door that was open and visible was a 9 pin serial cable right behind the credit card unit. I think the moral of the story is “Pay With Cash”. Thank you Spark Fun for the App and HAD for the article.
Just because a connection is serial doesn’t mean it can’t use encryption though.
I assumed they would, but I guess I too was wrong in that assumption.
For what it’s worth, access doors are meant to be locked and afaik serial cables for debugging are (or were) practically standard for nearly everything. The existence of a serial debug cable and minor incidence of careless employees/tech people alone is not that great a cause for concern. The /real/ moral of the story is that nothing is as secure as you think it is.
The moral of the story is get rid of stripe, like yesterday.
I discovered in Japan that the stripe on none of my cards worked. And that while Japan has chip and pin readers everywhere either they are disabled or the staff do not know how to use them.
What do they use, telepathy? Old fashioned friction and carbon paper machines?
If Japan is anything like Korea, it’s likely lots of cash and NFC payments.
From what I hear, lots of NFC and QR code payments, and lots of cash.
It is similar in Canada, at least in Montréal. Most terminal refuse to use the magnetic stripe of card when a chip is present. I actually got quite alarmed and surprised when I went on a trip to the USA last year when I realise their payment system are quite archaic and most would not even take chip. I was always confused when I needed to sign bill because I haven’t done so in so many years.Here, not only all card are coming with chip by default and has been for over a decade, but we can pay with paypass for a while now.
We’re still catching up.
Wow. Here in Europe we’re mostly past chip to contactless.
From what I heard and read, the biggest blockage for the US to adopt less archaic payment methods is due to the fact they have literally thousand of banking institutions, whereas we technically only have a handful under many different names. This makes adopting new technology a PITA.
Same here in Sweden. While you can find payment stations that still use the magnetic strip, they are increasingly uncommon. If the reader uses a magnetic strip and your card has a chip, the reader will complain and tell you to use the chip instead.
What i find annoying is that most payment terminals, at least the mobile ones, have support for wireless payment behind the keypad without any information that its supported. And then you have all the stores with their own standards for wireless payment..
Now every time i pay i first have to slap my bank card against the keypad then try the chip, have not used my magnetic strip for years..
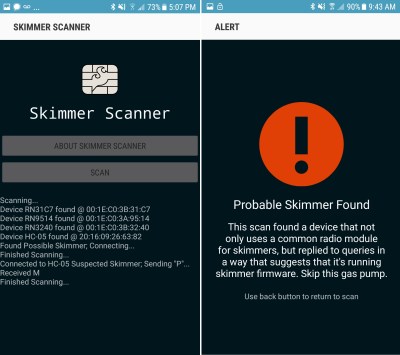
Is it just looking for HC-05? Why not just use the bluetooth pairing scan built into the phone?
The app seems to crash a lot! Most of the reviews are complaining about that, and when I tried it, it also crashed.
It’s looking for
– a device named “HC-05”
– which accepts the PIN “1234”
– and answers ‘M’ if a ‘P’ is sent to it on a Bluetooth serial connection.
While this app does little, running it should be less hassle than fiddling with a Bluetooth serial terminal app. Especially if you want to quickly determine if you should use the gas pump in front of you.
That is, if it wasn’t so unstable.
The whole point behind EMV was to make skimmers pointless. Knowing the human-readable and mag-stripe numbers shouldn’t be enough going forward.
At some point, card-not-present transactions are going to be the only avenue left for fraud and there will have to be *some* sort of browser e-commerce extension to connect to a smart-card reader so that e-commerce can be done with chip authentication. ApplePay for Web is a start, but something like that needs to be standardized.
Agreed. Yet I find 9/10 times the chip reader is damaged or disabled by the establishment’s owner. It really sucks things aren’t tighter these days. My only comfort is being a broke ass and not having enough money or credit to do much damage :(
With the liability shift, it won’t be too long before those merchants are driven to fix that or they’re driven out of business by the cost of covering fraudulent transactions.
EMV liability shift for fuel dispensers doesn’t kick in until Oct 1, 2020.
It’s not the merchants (as far as gas stations go), but the hardware vendors who are at fault here. The majority of gas stations all use hardware provided by the same vendor: Gilbarco/Veederoot. THEY, have not updated their hardware for gas dispensers in ages.
I have yet to see a gas pump with a chip reader.
Go to Europe. Could not buy gas on a Sunday in France because my card did not have a chip and there were no manned stations in the area.
Most of Canada’s self-serve gas pumps expect chip cards (though I suspect most will also still accept mag-stripe credit cards too).
Here in BC you must pay at the pump or pre-pay in order to activate the pump.
In my experience so far with having my card frozen and having to replace it, the terminal in the station is more likely to have been hacked than the one in the pump, though such incidents have drastically reduced since all of Canada’s banks went to chip-cards a few years ago.
I wish I could get them to disable the NFC tap-to-pay feature on all my accounts though — some stores have tap-to-pay limits as high as $200, and a stolen card is probably now my biggest risk.
AFAIK and probably depending on the bank, the cards are available both with and without the NFC element built-in. You probably have to ask specifically for those tho.
Does anybody know if tap to pay is done with a separate chip still? In that case it’s trivial to trace out the antenna on the surface of the card and disable the NFC chip with a sharp object and a hammer. Heck! If there’s only one chip you can probably just break the coil to disable NFC.
You can easily break the antenna coil – it can often be seen by shining a bright light through the card.
EMV is broken and has been for some time.
It’s more complicated than skimming & replay attacks are largely mitigated but the (usually guardianless) point of sale is still the vulnerable part of the equation. Skimming just requires different equipment that some criminals don’t know about yet. Shimmers are still a problem, and the outdated PoS terminal OSs are still vulnerable.
And with all security, implementation is often done poorly. Ignorance and haste abound.
No haste with the United States Postal Service. They’ve had the chip readers for a long time, so long that they’ve had special dummy cards printed to stick in the card slots to tell customers chip reader is ‘coming soon’.
Those dummy cards actually damage the devices, ironically. They either keep the contacts that read the card depressed for so long that they lose their spring, or they keep the card detection button in the back depressed for too long and it will not go back to an open state. Then, merchants turn on EMV and the device beeps at them non-stop to remove a card that isn’t present.
EMV may be broken, but it beats the snot out of mag-stripe.
It looks to me that whole CC system is based on “I don’t care” premise. Guys who make communication modules for transfering CC numbers to gas pump don’t care about making more secure line because they’re not requested to do such thing, gas pump doesn’t care because loss is not significant, banks don’t care because they get refunded from gas pump (or insurance), card owner doesn’t care because he will get his money back, so actually no one gives a crap about improving the system. So we have secure data transfered over 9600 baud serial unencrypted link in 2017.
Just as I was leaving on a long weekend trip I got a call from Discover’s fraud unit. My card had been used to buy gasoline in Arizona about 1000 miles from me; a place I have not been in over 30 years. When I asked how my card information had been obtained they said they did not know.
While driving I contemplated the problem. It is statistically trivial to locate the skimmers and to identify accounts which are at risk. There are sets of fraudulent transactions associated with each skimmer location. Any card associated with that location is at risk. Quite clearly I cannot buy gasoline in Arkansas and Arizona on the same day without making TV in a very high speed chase across Texas and New Mexico. I live in Arkansas, so it’s easy to tell which transaction is legitimate.
The card companies force the losses onto the businesses as much as possible and use their losses to justify loan shark interest rates of 25%. Allowing fraud is an integral part of their business model. They do care, but not in a good way.
What’s real fun is when you call you cc company and tell them you’re going to be traveling out of country, then try to use your card for gas, and it gets declined. After 3 hours of “we’re sorry, all technicians are on another line” at 2am, you get “we declined it because the system didn’t know you were traveling out of country”…
Not with AMEX.
But with AMEX, when you arrive, no-one will take your card.
I know for a fact that they do exactly this. Of course it relies on first getting enough reports of fraud to correlate, but once you do its quite easy find a common transaction. It seems to me this might be how they figured out that your transaction was fraudulent, 1000 miles could be only a LONG days drive.
I had the opposite problem. I traveled one state over and tried to pump gas, all my cards failed to work. Chase’s fraud detection unit had shut off all my cards. I had no cell service and no gas. Yay, thank you Chase for taking proactive action for “my protection”.
You can actually travel pretty much anywhere in the world without putting a note on your account now since nearly everyone uses chip. But apparently if you want to travel anywhere in the US? You need to tell your credit card company.
The code protect bit is on, that’s why most of the firmware reads 0.
Usual security principles apply – you have physical access & it is game over. The only real surprise is that this kind of thing isn’t more prevalent/wide spread.
Probably, but if communication line was made more secure (for example AES encryption, critical stuff in epoxy) it would take much more time to install skimmer. Thieves are willing to spend 30 seconds exposed until they install simple chip in the middle hack, but probably wouldn’t be willing to spend 30 minutes to completely disassemble pump and access card reader from inside. In many cases security comes only to making attack time infeasible.
More common is to encrypt with a computer that is tamper resistant and using RSA2048. Asymmetrical encryption is much preferred over symmetrical as the key has to be distributed to thousands of endpoints. 3DES DUKPT is also common. This is symmetrical encryption, but an algorithm is used to derive a unique key from the prtivate key for each transaction which makes replay attacks impossible and patterning of the key more difficult
Then it would be good practice to make it difficult to gain physical access wouldn’t it?
Sure, if you are transmitting a cleartext key. It’d be amazing if we had some kind of cryptographic module embedded in credit cards that could combat these MitM attacks.
This happened by my house. During maintenance, three pumps were discovered to have them installed. They have no idea how long they were there. Luckily I always pay inside.
I wonder if they do an effort to preserve fingerprints when they remove such devices.
The pervasive use of fingerprint evidence and its effectiveness in police procedural dramas on television VASTLY overstates both IRL.
That’s why I wondered. I think in such cases as this where a device is probably possessing flat plastic surfaces and aren’t touch by others you’d stand a good chance on getting a fingerprint, and the chance the person is already on file classified in a certain category is also well higher than average I expect. But I also see it possible that the cops don’t bother anyway.
From the sparkfun article — “It’s unlikely the pump controller market would gravitate towards the same number of pins using the same type of connector but use two different orientations.” If you’re at all familiar with eurorack you know this is NOT unlikely.
I’m shocked they’re surprised. Every country has their own different version of “local” card transactions, which generally require slightly different terminals and the big petrol pumping hardware companies want to sell the same equipment everywhere. Standardisation is inevitable.
I misunderstood, I thought it was a case of two fractionally different versions of the same connector because $REASONS, but Sparkfun’s conclusion is that the assemblers are idiots and this is the simplest way to make it idiotproof. “Plug it in, does it work? No? Flip both connections”
That said, _either_ option is plausible to me. I know there are at _least_ 4 different standards for the “bus” petrol pumps are connected to (at least one is modified RS232 … on a bus, with the “master” device communicating using a different _voltage_) so two different card terminal connection standards which only differ by the connector is completely plausible.
On the one hand, this is illegal and very irritating that now I have another reason to worry about my gas pump stealing my money.
On the other hand, some of the most impressive hacks I have ever seen on HaD have started as criminal activity, so hats off (and handcuffs on) to the lowlife who came up with this one.
Time to put skimmer Bluetooth modules on a schedule so that they’re only active during a 5-10 minute window each day, during which their data can be dumped.
Or make them not broadcast anything before waking them up with a magic packet or magstripe card.
Why has the USA been so slow to implement chip and pin…. I’m Canadian and travel overseas all the time and have not “swiped” a card for about 15 years. I have also not used cash in years. When I recently traveled to the USA I was surprised to see that some companies would only take cash or offer discounts for cash and only 1 or 2 companies could take a chipped card. Mag strips were old tech 20 years ago, replaced 15 years ago by most countries…. why is the USA so far behind?
USA is using card with chip, but, like stated earlier, some places only use the swipe, some do not even have that, some will have to type in the card number (shutter on that one).
From my travels, this is the same all over the world, so don’t go there with that “better than thou” attitude.
You kinda revolve around the places where the chip is used,the others, they will get the picture and switch over soon enough.
I remember when I got this and thought “hell yeah,no more standing in line behind several losers cashing in their lotto cards! Dont even have to go inside anymore!”
But, the usefulness of this verses the hassle and threat has gotten to the point where paying with cash is easier and better.
Lol i dont have a “better then thou” attitude. Swipe does not exist here, as far as I have seen that is without exception, I assume that’s driven by the banks, or maybe insurance companies, or maybe by the card providers themselves. I was just curious why the USA is so slow to adopt. (was hoping for some constructive discussion about that)
As far as i know chip and pin offers the same ease of use with none of the risk, now the new tap to pay is a different story, but chip and pin is quite secure due to its challenge and response architecture.
Ditto for the UK. Stripe readers exist, but are only used as a last resort if the chip is broken in some way. Contactless is getting omnipresent too, and is (afaik) card issuer-limited to £30.
Checking in from Germany. We use cash for most transactions, however if you do use card it’s always chip+pin
The contactless limit seems to be rising in the UK.
And I noticed recently that if you spend too much too fast on contactless, it prompts you to chip and pin again to check the card wasn’t stolen. Nice feature!
Because the banks and equipment owners don’t want to have to spend the money to upgrade all their point of sale terminals and card readers. Same reason we had AMPS and the digital overlay to AMPS when the rest of the world went GSM, corps didn’t want to spend the money.
It’s the size of the market and thus the larger existing installed base of older equipment. Look how long it took us to get digital HD broadcast TV. Several years to get most of the stations’ equipment upgraded, still leaving many lower power transmitters on analog.
Smartcards go back quite a ways. IIRC reading about them being used in Europe in the 80’s.
All the fancy technology can’t stop a person with their Mark One Eyeball and a good memory for numbers from borrowing your card number, and the CCV on the back. One of my uncles and his wife were on their way home from staying in Arizona for the winter. They stopped for gas and their card was declined.
They were pretty certain it had been the arab person at the checkout at a restaurant they’d eaten at earlier that day, because the bank told them they’d blocked their card because someone had tried to use the numbers to buy a couple of plane tickets to the USA from a country in the middle east. Sure it *might* have been any one of the number of Caucasians who’d handled the card at various businesses during their trip, but what’s most likely?
A friend of my folks had the same thing happen with his cellphone a few years ago. He worked at Fort Huachuca , which is right on the US Mexico border. He got a big bill with a ton of calls from Tijuana, starting almost immediately after he’d made one call outside his carrier’s coverage area. Apparently a tower just over the border had grabbed it, and nefarious persons had tapped its systems so they could clone phones.
“It’s the size of the market and thus the larger existing installed base of older equipment.”, I do not buy this, I would say lack of regulation or interest from involved parties.
Because of patent. They don’t want to pay license that’s all.
This only works for your american magswipe cards, right?
The “regular” cards only use tamper resistant and approved hardware and asymmetric keys, which should prevent pretty well this kind of easy attack, isn’t it?
Yes, but EMV cards are becoming the norm here too. Just have to wait for the liability shift to wake up (or kill) complacent merchants.
because right now, who is responsible? the obligatory card payment insurance?
Doesn’t matter, the cost eventually gets passed along to customers.
It’s useful to understand that the card payments industry is really just a legal framework defining how to execute business that members agree to in order to participate in the system. Technology is very much secondary.
There is an explicitly specified dispute resolution process that almost never is completely perused except in the cases of massive fraud, which fraudsters rarely commit because they know how not to get caught: do not drink deeply from that same well twice. The formular process — last I looked — in the US hinged upon a couple pieces of consumer authentication data: signatures — which the US system still prefers, and PINs — which have established history in the US from the 70s and so are also accepted (mind you: only PINs constructed and delivered in a very specific technical context, not just some scheme you made up for a web page or a mobile app).
Outside of that, the customer will almost always win a dispute if they are persistent in prosecution of their case. Who pays in the end is usually a matter of business pragmatics. In my experience, usually the merchant will choose to eat the costs rather than aggressively defend. The merchants I have worked with usually have an expectation of a certain amount of dispute, and choose to eat it rather than create ill-will. Mind you, I’m speaking from personal experience about in the hospitality industry. I’m sure the mechanics are quite different in, say, the professional services industry. Anyway, as a consumer, try it! No signature, no PIN, no problem! (disclosure: I founded a mobile payments company in the past decade, and I have more experience that I would like in having to talk to the particulars of this chink in the armor of the card payment system.
The recent drive towards EMV adoption in the US has spawned many conversations on the topic of ‘liabilty shift’. The real liability shift is towards the consumer: if and EMV transaction has occurred, then it becomes the consumer’s responsibility to show that it wasn’t them (ostensibly because of the instrument’s security features). The secondary liability shift is towards the merchant: if you do not transact in EMV, then you will now by default lose the dispute. However, as I mentioned, practically this was the way things went down anyway, so that dog has no teeth. Lastly, there are practical incentives for the merchants; e.g. tweaking the transaction fees to give a break on EMV transactions relative to swipe and CNP, and even lessening the burden of PCI DSS annual audits (exquisitely painful).
In the end, though, all this system is built on antiquated technology and practices. It it ripe ground for disruption, but that has been the case since the late 90s. So why no advancements? Haha, because the card payments industry likes things eeexxxaaaccctttlllyy as they are. The last time there was an upstart was Discover in the late 80s and we will simply not be having any more of that, thank you very much. Even PayPal could not disrupt; they eventually played along, and now are just a husk of their technical origins (but really they are just too busy making money to fool around with ‘disrupting’ anything. But they cannot move forward! Enjoy the doldrums while those balmy days do last.) Google could not disrupt. The mobile carriers could not disrupt with their hilariously ill-conceived Isis (and the guys were a bit of rude and hubris-y, so good riddance to them; best of luck on your future faileurs!). Bitcoin cannot disrupt, at least not yet, and probably not them specifically. Apple cannot disrupt despite their legions of mesmerized sycophants happily tithing their hard-earned income to the corporate monument of a desiccated folk hero. I think Amazon has the best opportunity, and the most plausible technical chops. But then, doesn’t Jeff Bezos have enough money, already?
Liability shift is just an incentive to adopt, and the underlying technology (EMV) is 20 years outdated anyway.
Merchants are not the problem at all. In a perverse way, overburdening merchants with a draconian liability shift would provide fertile grounds of opportunity to create something good, and free from the hegemony of the established payments card industry. Have you seen the rates, and what it takes for a merchant to pay-to-play in that now vital system of interchange?
I was told by a small merchant, that going to a chip activated credit card reader would cost them $1500. So even though their card reader has a chip slot in it, it is unused.
teehee, yes you’ve figured it out! The real winners in EMV adoption in the US are: card personalization companies, like Gemalto, Schlumberger, etc, and card acceptance terminal vendors, like Verifone, Ingenico, etc. Hahaha! Everyone needs to be shipped new cards at a few bucks a pop! (Ka-ching!) Everyone needs new card acceptance hardware! (Ka-ching!) Everyone needs usefully improved security (crickets and tumbleweeds…)
Truthfully, for quite some time the card acceptance hardware has already long since been deployed in most locations, and only firmware update is needed (and should that cost? does it cost? oh you betcha), and then reconfiguration in the POS. That last bit: the reconfiguration in the POS, has (at least in my personal experience) been the real obstacle to switching over. Alas, switching over doesn’t really provide strong security benefits, and marginal rate improvement for the merchant. EMV is just old tech; we should create something much better to last the next 20 years, instead of digging up something created in the context of things as they were 20 years ago.
I like my electric car more and more each day!
Yes, electric vehicles have not shown to be vulnerable to nefarious people at all.
Cough, cough, whatever is the latest info-tainment system access hack and the “smart grid” cough, cough.
https://hackaday.com/2015/08/22/how-those-hacker-took-complete-control-of-that-jeep/
yes it is!!, just destroy mag-stripe on the card -is useless those days (except skimmers)
What if the gas pumps are being compromised by the gas station owners? Our gas is two cents less per gallon, but we steal your CC data! Glad I don’t have a car anymore.
“criminal” soldering!!! lol! +1 Jenny List
in other news, now that chip readers are deploying in flyover land USA, i can say, they mostly suck. one of the grocery stores is no longer unconscionably slow but the card or reader is often too dirty to work. i would have expected them to be designed to tolerate an often-just-capacitive coupling between card and reader but that does not seem to be the case. and my bank just switched to chip readers for their ATMs and the slowness, the slowness, the slowness! inertia is a thing when crap companies are deploying to millions of point-of-sale locations.
It sounds like these companies may have opted for the very cheapest barely functional option around. Chip card payment can be ridiculously swift and very reliable, but it generally tends to mostly be in places that value speed over minimal cost.
In an effort to drive people towards shitty store-specific payment systems with even LESS fraud protection (Walmart Pay) than legacy magstripe, retailers have done all they can to cripple the EMV transition, including using the shittiest EMV technology that doesn’t make them vulnerable to the liability shift. (e.g. accepting only contact-based EMV and not the MUCH faster contactless version)
It’s all just another move in a MUCH bigger game between credit card companies and retailers.
Not reliable in the case of my visa debit card. It wore out in less than a year.
That’s ok. Apparently the chips plunk out of the card before long anyway.
http://abc7chicago.com/finance/credit-card-chips-can-fall-out-posing-a-security-risk/2284510/
While I prefer chip cards, I’ve found transactions to be slower than magstripe reads. This is the case at in store POS terminals and ATMs.
I’ve found that the slowest chip payment processes can be found in tiny shops, with the fastest being found in high volume operations that are well-oiled and fully rehearsed. This tells me it’s not down to luck or the technology itself, but that investing in the infrastructure and possibly services yields a faster payment process.
Any company that can shift more customers with less staff will be interested in moving things along as fast as possible.
The reason for the speed difference is small shops will be using dial-up connections, larger ones will have a an always-on link.
When a national drug store chain switched on their chip readers, It took more than a month for the system to stop declining my card.
Prior to this changover, the same card had worked fine as a mag stripe in the drug store and the chip & strip worked at any other merchants POS in the surrounding area.
I called both the credit card issuer and the corporate office of the drug store.
No real surprise that each one pointed a finger at the others system.
I wish someone braver than me would plumb the dark web and see how easy it is to buy these devices.
The app only searches for HC-05 modules?
Then, the bad guys can switch to another module in the next iteration…
Or just change the HC-05’s name and PIN. It can be done by issuing a couple of commands (AT+NAME and AT+PSWD if I recall correctly) during assembly (they’re persistently stored in the module’s flash memory). Interestingly, there’s a three-pin header on the skimmer board just for this purpose.
Can anyone recognise the skimmer? Who makes them? I checked DX but could not find any.
Thing is, at work, we need to analyse a lot of serial communication on some old industrial machines. To record it, we are currently using RaspberryPis. But that is a lot of rPis, that need extra power etc.
A solution, where the whole thing connects directly to the machine, with no extra power supply, would be great.
Reason #811 why I drive a tesla! No gas pump!
Unencrypted serial is just an embarrassment.
I did some poking around and found that there are standards for credit card readers, specifically Payment Card Industry (PCI) Payment Transaction Security (PTS) which includes hardware security and encryption.
It looks like they can even be downloaded without paying lots of money…
https://www.pcisecuritystandards.org/document_library
I live in NZ and we use chip & pin. Usually the chip takes a couple of seconds longer than the swipe. Certainly faster that swipe & sign. Some machines are super slow, though.
The contactless cards are fastest, but a lot of smaller stores don’t have them. I asked around and it turns out you pay additional fees for the privilege.
Whatever you do, DONT PAY INSIDE – Especially not in cash! I have heard about a new fraud type, that is becoming prevalient, and that is gas station owners who want to get a little bit extra, they simply don’t enter the payment in the cash register (or cancel out the payment) just after you walk out the door.
And then reports you for running off without paying. The tax authorities cannot defend against this type of fraud as they are not allowed to buy non-refundable products, since then the tax authorities cannot charge the company for the purchase unless they did cheat.
If you instead pay-at-pump, it will both be visible on surveillance tape, in the pump logs, and also on your statement. It will also be shown in the cash register log that your pump was not activated by the clerk.
To protect against skimming, I would recommend using Samsung Pay, or a chip card. They can skim until the cows come home, it wont work as each transaction is unique.
To use Samsung Pay at a “Dip” reader, do this:
1: Insert a plastic card that does NOT have a magstripe or chip. For example a ID card, driver’s license or something else.
2: The cardreader will now say “Can’t read chip, please take the card”. Activate Samsung Pay at this time (eg, use fingerprint, iris or PIN).
3: Take out the card you inserted, and in the same move as the card leaves the card slot, put your Samsung Phone’s back against the card slot. Since the card reader didn’t see a chip, it has activated its magnetic head. And now Samsung Pay transfers the information to the magnetic head via MST (Magnetic Secure Transmission).
4: Voila, payment done. In some cases you may be asked for a PIN, then you enter the PIN for the enrolled card (not the Samsung Pay PIN, but the PIN the bank said you should use for Samsung Pay when the terminal asks for PIN).
If a pump holder does this 3 times or so and people report it then soon they would check the guy for fraud and he’d go to jail.
I don’t buy it’s so common outside countries with a very shady law system like in South America maybe.
I mean it’s obvious and soon detected.
Where can one acquire the a fore mentioned Android app? It does not appear on the Sparkfun website, nor on Google Play Store.
follow the link, click on get the android app here…
Oh sigh, nm I’ll paste it
https://play.google.com/store/apps/details?id=skimmerscammer.skimmerscammer
I generally move money from my savings account that is not accessable from my cards to a specific card at time of purchase and leave it empty when not buying anything. Takes 5 seconds to transfer using my banks phone app.
There are a lot of mandates. Merchants are required to be PCI compliant in order to process credit cards. PCI does allow for the use of non-encrypting readers, but it puts a lot more onus on the rest of the infrastructure. Many merchants are opting to use P2PE certified solutions which are validated by a QSA. In these solutions, the cardholder data is encrypted on a device which has a TRSM and the encrypted data is not decrypted until it reaches the host or a gateway with a private connection with the host. These solutions are very secure and allow for merchants to bypass much of their annual PCI audit. In light of the major breaches this is becoming very common. At this point, much of the security risk for the large merchants has been mitigated and processors are shifting their focus to middle and small merchants. For these merchants, they will begin mandating that if they are not using a P2PE solution then they will be forced to have their installation done by a QIR certified installer that validates all necessary firewalls/AV/intrusion detection/etc are in place.
We’ve really come a long way since the target breach, but still have a long way to go.
Also, in case you are curious, none of what I mentioned above has anything to do with EMV. EMV actually does not add any security to your cardholder data, it is just supposed to make your card harder to duplicate. It also has some pretty major security flaws that are known by industry professionals and we are just waiting for someone to discover and exploit them.
So your idea of accountability is to require that if criminals break the law, then the person they break it against is responsible? What the hell kind of Fd up logic is that? If I mug you because you’re not carrying a gun to deter me, then that’s your fault? You are truly a refuse of a depraved mind.
How about recognizing the criminals are exploiting legal and normal activities, and because of the risk, we humble request the CC companies and pump station employ better measures to thwart violent and repugnant criminals. A sane mind would recognize the criminals are the criminals, not those who I willingly give my money to, to make my life easier and more convenient.
Who are you replying to? If it’s the main article then you are being silly. instead of you gun example you should say ‘if my bank stores my money on the street at night without guards they should be held responsible if it’s stolen?” and then the answer is YES.
We have tackled the problem by developing a Direction Finding 2.4 GHz Bluetooth Skimmer Locator that scans for both Bluetooth and Bluetooth Low Energy https://www.bvsystems.com/product/bluesleuth-bluetooth-skimmer-locator/ We can target certain BT modules, set a watch list, but most importantly when a target is identified you tap on screen and can direction find ONLY on that target and ignore/discriminate other unwanted Bluetooth signals.
Funny, the gas stations don’t have the time nor money nor technology to make the gas pumps secure, ye they sure can blow a wad installing completely annoying, loud, and unnecessary video screens to blast out a stream of promo ads for TV shows no one cares about or attempts to entice me into the Circle-K for a three-days-on-the-rotary-grill hot dog.
Didn’t “Square” have this problem on their early credit card readers? The first ones had only a magnetic stripe read head wired to the mic jack pins. Only later did they include a coin cell battery an a chip to encrypt the mag-stripe data before it entered your tablet or smart phone (lest a man-in-the-middle wayward ap intercept the stuff and send your data off to Russia).
The bigest problem with going to new technologies to make electronic thefts impossible (or at least very impractical) is that it costs a LOT of money to upgrade systems. This is due to the bureaucracy not technology. eg, a secure system can cost as little as $5 per person, but to supply, test and install such a system, the price rises to $50 per person. In a system with a million users, that’s $50 Million. If the losses due to theft are just $1,000,000 a year, then it would take 50 years to see a return on this investment. Yes, it’s the bean counters that rule (and wreck) the world. I am more upset with the bean counters that have wrecked Honda’s reputation for making reliable cars. But about skimming cards, my last word of advice, beware of ATM’s unknown. There have been entire stand alone kiosks that are FAKE. Insert your card, enter your PIN and the machine just reports “Network Down” or something like that and the crooks are quickly using the entered information in a REAL machine to drain your account. Only use your card at a known or an official bank.
It doesn’t matter that the card-to-terminal link isn’t encrypted. The card-to-bank communication is *authenticated* by a private or secret key in the chip that no one can reasonably copy.
The fix for this is for the chip and card to report different account numbers and for the bank to know they can safely refuse all CNP transactions with the chip’s number. This is how Apple Pay works. You could, in principle, perform the transactions with bullhorns across the parking lot and nobody would be able to use that information for anything interesting.
When I say “chip and card have different numbers” I mean that the number printed on the front is different from the one encoded on the mag stripe and reported by the chip. Both the stripe and chip should be configured to refuse CNP and the chip account can refuse swipe as well. Yes, skimming the stripe would still let you clone the stripe, but it at least raises the bar a little bit to eliminate CNP.