It’s a sad commentary on the state of the world when it becomes a good practice to closely inspect the card reader on every ATM and gas pump for the presence of a skimmer. The trouble is, even physically yanking on the reader may not be enough, as more sophisticated skimmers now reside safely inside the device, sipping on the serial comms output of the reader and caching it for later pickup via Bluetooth. Devilishly clever stuff.
Luckily, there’s an app to detect these devices, and the prudent consumer might take solace when a quick scan of the area reveals no skimmers in operation. But is that enough? After all, how do you know the smartphone app is working? This skimmer scammer scanner — or is that a skimmer scanner scammer? — should help you prove you’re being as safe as possible.
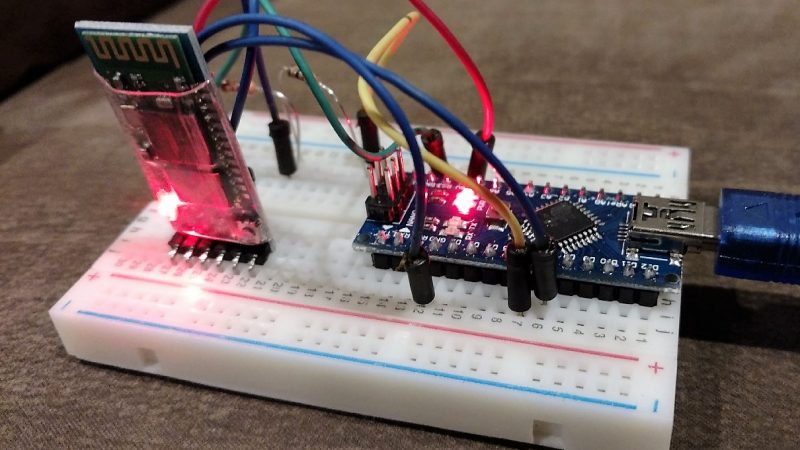
The basic problem that [Ben Kolin] is trying to solve here is: how do you prove a negative? In other words, one could easily write an app with a hard-coded “This Area Certified Zebra-Free” message and market it as a “Zebra Detector,” and 99.999% of the time, it’ll give you the right results. [Ben]’s build provides the zebra, as it were, by posing as an active skimmer to convince the scanner app that a malicious Bluetooth site is nearby. It’s a quick and dirty build with a Nano and a Bluetooth module and a half-dozen lines of code. But it does the trick.
Need a primer on the nefarious world of skimming? Here’s an overview of how easy skimming has become, and a teardown of a skimmer captured in the wild.















Recently had experience with these in the wild:
https://krebsonsecurity.com/tag/insert-skimmer/
Can’t tell if they were wireless or not.
Infraudred
Some need to be removed.
Isn’t this “skimmer” problem basically solved* when using chip cards? In Poland, they were a standard for more than a decade – I believe this is also the case for most of Europe. Why are these (insecure by design) magnetic cards still in use, when there is a much better alternative available?
*maybe not solved, but made orders of magnitude more difficult than just reading the magstripe
Chip cards still have the mag stripe on the back to be read by a skimmer. You could demagnetize it so only the chicp works. While at it, why not also cut out a notch out of the edge of your card to disable being hacked by RFID scanners?
Not all chip cards do. And chip is more secure (and more common) than RFID so why even mention that?
chip cards are still susceptible to MiTM attacks
While we now have the chip cards in the USA, it is left up to the merchant whether to require the chip or use the mag strip. I have never seen a gas pump in the USA with a chip reader!
If the merchant decides not to use the chip, they are liable for fraud that results from it, but gas pumps usually require entry of the billing zip (postal) code and have video of the transaction, so I guess the fuel industry decided they were ok without the chip.
If I remember correctly Chip readers were supposed to be installed in gas pumps by 2018, but that got pushed back to something like 2025. The only chip readers I have seen are in brand new stations that have been built in the last year or so. Best option, pay cash at the register. Nice hard to trace cash.
Are the penalties too low for this type of criminality?
Is anyone familiar how badly they get punished for skimming? Like is it per card number stackable or is it just a straight shot generally?
Interesting read.
Different case on different jurisdiction for sure. But from previous cases here, the jail terms are one shot (you rarely see one of them got hundred years term!), the fine/damages might be cumulative (but they’re rarely can afford to pay them anyway).
More people shafted generally means a stronger case and more pissed off people who can afford better lawyer, so it might indeed affect the punishment in a way…
“sipping on the serial comms output of the reader”
Well, that particular case is caused by people buying the cheaper ones without encryption. Which I think is plain irresponsible, because I’m sure encrypted versions are available. Maybe even systems with anti-tamper stuff to make it harder to e.g. attach wires to the mag head.
However, I’m sure people get really creative when it comes to stealing money, anti-tamper would just make it harder to steal card data.
The problem is that the chip cards do not reliably read. Magstripe works first time every time.
This is a neat little demo, but it seems the same thing could be achieved with some Python and a Bluetooth adapter, no? Just need to set the BT device name and respond to the connection appropriately, if I’m understanding it correctly.
Also seems that it would be trivially easy for the makers of these skimmers to avoid detection by this app, but i guess the hope is that at least you’ll be able to detect the ones already in the field.
Why is this article tagged with ESP8266? Maybe I missed something, but the primary project linked uses an Arduino Mini clone and a HC-05 Bluetooth module. And I don’t see anything about ESP8266 being used in any of the secondary links either. Seems like a topic tag in err, but maybe I’m blind.