Cloudflare announced recently that they are seeing an increase in amplification attacks using memcached servers, and that this exploit has the potential to be a big problem because memcached is capable of amplifying an attack significantly. This takes DDoS attacks to a new level, but the good news is that the problem is confined to a few thousand misconfigured servers, and the solution is to put the servers behind a tighter firewall and to disable UDP. What’s interesting is how the fundamental workings of the Internet are exploited to create and direct a massive amount of traffic.
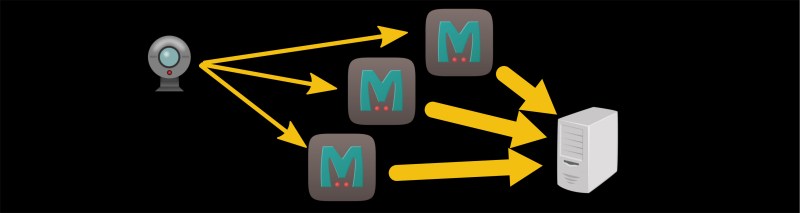
We start with a botnet. This is when a bunch of Internet-connected devices are compromised and controlled by a malicious user. This could be a set of specific brand of web camera or printer or computer with unsecured firmware. Once the device is compromised, the malicious user can control the botnet and have it execute code. This code could mine cryptocurrency, upload sensitive data, or create a lot of web traffic directed at a particular server, flooding it with requests and creating a distributed denial of service (DDoS) attack that takes down the server. Since the server can’t distinguish regular traffic from malicious traffic, it can’t filter it out and becomes unresponsive.
This DDoS attack is limited to the size of the botnet’s bandwidth, though. If all the web cameras in the botnet are pounding a server as fast as they can, the botnet has reached its max. The next trick is called an amplification attack, and it exploits UDP. UDP (as opposed to TCP) is like the early post office; you send mail and hope it gets there, and if it doesn’t then oh well. There’s no handshaking between communicating computers. When a device sends a UDP packet to a server, it includes the return address so that the server can send the response back. If the device sends a carefully crafted fake request with a different return address, then the server will send the response to that spoofed return address.
So if the web camera sends a request to Server A and the response is sent to Server B, then Server A is unintentionally attacking Server B. If the request is the same size as the response, then there’s no benefit to this attack. If the request is smaller than the response, and Server A sends Server B a bunch of unrequested data for every request from the camera, then you have a successful amplification attack. In the case of memcached, traffic can be amplified by more than 50,000 times, meaning that a small botnet can have a huge effect.
Memcached is a memory caching system whose primary use is to help large websites by caching data that would otherwise be stored in a database or API, so it really shouldn’t be publicly accessible anyway. And the solution is to turn off public-facing memcached over UDP, but the larger solution is to think about what things you are making available to the Internet, and how they can be used maliciously.















” And the solution is to turn off public-facing memcached over UDP, but the larger solution is to think about what things you are making available to the Internet, and how they can be used maliciously.”
Or raise better citizens that don’t think this kind of behavior is OK.
its sad that in the lasr 25 years or more, thar little has been done to enforce rules related to hacking and other cyber crimes. you can report it all you want but unless your one of the chden few at the top of the food chain rsrely anthing gets enforced.
not to mention that little has been done to really establish edicate, short of don,t use all caps cause the equivilent of yelling.
I can’t even tell for sure what you are saying but..
“thar[sic] little has been done to enforce rules related to hacking and other cyber crimes.”
Yeah for sure, handing down 250 year prison sentences is a slap on the wrist. They should have been in prison until the sun burns out at least, and in extreme cases until universe heat death.
If you can raise people in a fashion that precludes security then congratulations, you’re the first to successfully change human nature in over thirty thousand years of attempts by billions of people.
Like a lot of the things in the world, it isn’t about absolutes, but percentages. It’s how society continues to function without falling apart.
Well, imagine how much worse it *could* be.
this is a terrible article. If memcache is acting as an amplifier, that’s the news, and it should be addressed, like the DNS amplification issues of years past. The underlying botnet is fairly irrelevant. Where are the details of how memcache amplifies attacks? All we got was a sub-par wikipedia description of what an amplification attack does, and a half-assed ‘solution’ that doesn’t address why you might want memcached to serve UDP.
Be nice and try to see it from the perspective of someone who doesn’t have your particular specialty. It elucidated enough of the process for me to get the gist and have what I need to do independent research about what wasn’t said.
That said, it could use more detail in the areas you said, fair enough.
Oh there is worse stuff going on for ages now,
DNS attacks and Cache attacks have been on going in South Africa for the last +- 7 years
And have been growing,
Wow, if they ever connect South Africa to the Internet, that could be trouble.
These people need to learn how to use their firewall. Drop everything that isn’t explicitly allowed. White list by IP or subnet unless access is required from anywhere such as for public services. memcached instances are not public services.