A song by Rockwell, “Somebody’s Watching Me” might be the anthem for the tin foil hat crowd. But a new paper reveals that it might be just as scary to have someone listening to you. Researchers have used common microphones to listen in on computer monitors. The demonstration includes analyzing audio to determine input from virtual keyboards and even a way to tell if people are surfing the web during a Google Hangout session.
Reading monitors based on electronic emissions is nothing new — ask Wim van Eck or read about TEMPEST. What makes this worrisome is that we constantly have live microphones around our computers. Webcams, phones, the latest smart assistant. Even some screens have built-in microphones. According to the paper, you could even pick up data from recorded audio. The paper has three main goals: extract display text, distinguish between different websites on screen, and extracting text entered with a virtual keyboard.
The analysis looked at 31 different screens. There were 12 distinct models from 6 different vendors. They did use a special VGA cable to tap the vertical sync to help manage the data, but they claim this was only an aid and not essential. They also used a high-end sound setup with a 192 kHz sampling rate.
Measuring the sound made by different display patterns was empirical. The authors think the mechanism is from subtle changes in the vibrations of the power supply components due to changes in current consumption. The refresh rate of the monitor also plays a part.
Armed with the proof of concept, the team went on to use an LG V20 cellphone and via a Hangouts call. Imagine if the person on the other end of your call could tell when you were reading Hackaday instead of paying attention to the call.
Different types of monitors need to be learned for best accuracy. It appears that reading small text may have problems, too. Even website detection depends on training. Still, maybe the tin hat people aren’t exactly wrong.
If you want to try your hand at reading the RF emissions, software defined radio is your friend. We’ll be interested to see if anyone duplicates the acoustic method in this paper, though.

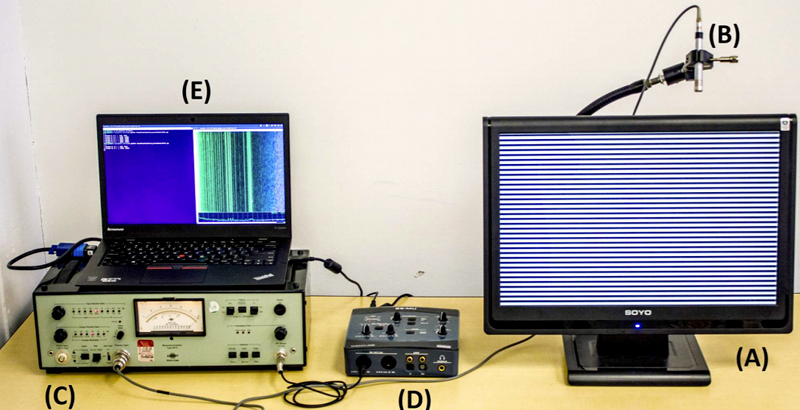














The set-up of this experiment looks suspicious to me. What is stopping the microphone and it’s long cable from picking up the monitor EMI, instead of just the monitor sound?
The same techniques used to eliminate noise in any such cable? Unless you’re accusing them of deliberate malfeasance?
Considering that the main focus of the research is in *remotely* retrieving screen contents from remotely recorded audio sources, I don’t see how they could possibly be relying on EMI that can’t possibly be present in an archived recording.
They cover this in the paper. They have several use cases (including using archived video and using a more distant microphone) and they do some experiments to show that the system performs much worse if they muffle the mic with some thick cloth.
Thank you, that sounds a lot better than what I see in the photo above.
Neat article, thanks for sharing. Seems like an interesting more COTS method that seems more like if we don’t read the fine print… consumers are consenting I’m guessing.
From what has been disclosed from what I’ve read… microwave and I’d guess precision lasers can be used somehow with improved performance using lock-in amplifiers that look like there are even cheap modules available I guess.
https://www.holographyforum.org/data/pdf/aa-Collection_a_k/aa-Laser/aa-lockin/Homebrew_lockin_amplifier.html (save this page and mirror while you can)
I’m not thinking it’s Men At Work now days:
https://www.youtube.com/watch?v=SECVGN4Bsgg
More like who knows what’s running not just the Eye in the Sky:
https://www.youtube.com/watch?v=NNiie_zmSr8
Not even remotely news. This is why we in the Air Force were forbidden to type up classified documents on electric typewriters FORTY YEARS AGO.
Chill
Shit… and he served starting in 63. So that was about SIXTY fucking YEARS AGO. With satellite BS until this very day. It wasn’t until recently when the USAF geek that let the US Army dumb asses on the ground get live streams of the drones and maybe more… died a few months back. They should of never let them have those feeds. Half the dumb asses reads to me are supposed to die for our country with the enemy’s invalids… that’s why the U.S. Army has the most casualties and like half not even in active combat live fire situations.
My Grandpa (U.S. Army Air Corp) didn’t say anything other than one time how fucked (not in his vocab) up the Japanese were and desperate to be killed. Their pilots were fucked up assholes that would beg to be killed. I guess the U.S. leadership didn’t want their bases craft either… so they’d strap their bombs on their captured pilots laps and give em enough fuel to crash out as sea and blow themselves up. The Japanese literally begged for that shit. They were cruel in some situations. I never did get any technical details though from my Grandpa other than financial investment stuff. He didn’t like to talk about the military and I wasn’t allowed to talk about with Great Grandpa or Grandpa. Crazy shit. I guess Great Grandpa got shot and wound up teaching French to the U.S. soldiers and enjoyed the French lifestyle when not on the front lines. I sometimes wonder with the Goodwill Ambassador program if my Dad and Great Grandpa got into intel roles with insurance brokering and other agriculture stuff that most don’t realize isn’t crude economic negotiations… albeit the USSR was probably drunken crude.
My god; are you having some sort of mental episode?
Dad’s birthday (deceased) and parents anniversary (Mom almost got murdered by the “cancer” remote sensing/transmission and maybe poisoning somehow crap) memorial day holiday emotionally magnified testimony moment like this article was a support group posting or something. RINT, ELINT, MASINT, SIGINT remote mind controlled orders too.
Are you familiar with the sound, body and mind control technology much? I’ve lived with the impact daily since the Clinton admin and maybe earlier in my life and don’t remember in detail… literally… most likely too much neighborhood cool aid and stunts.
IBM Selectric typewriters can be bugged by installing switches on the (IIRC) six bars that command the rotation and tilt of the type ball. That also made it fairly easy to hack them to be printers with a solenoid attached to each bar.
That is true, and I’ve owned two solenoid-equipped Selectrics. One was in a dedicated “word processor”, the other was an Anderson-Jacobson terminal. But the Air Force proscription was not limited to Selectrics. By monitoring the mains voltage and current, investigators were able to develop signatures for each key. This did require monitoring the power at the outlet the typewriter was plugged into (or possibly the circuit breaker panel), but did not require access to the typewriter itself. If access to the typewriter is allowed for, even manual typewriters can be “bugged”.