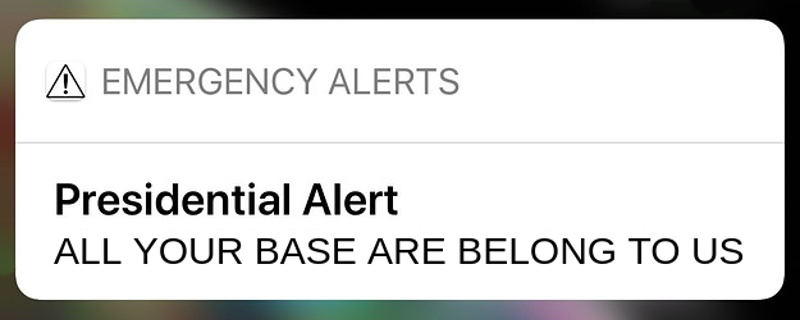
In April of 2018, the Federal Emergency Management Agency sent out the very first “Presidential Alert”, a new class of emergency notification that could be pushed out in addition to the weather and missing child messages that most users were already familiar with. But while those other messages are localized in nature, Presidential Alerts are intended as a way for the Government to reach essentially every mobile phone in the country. But what if the next Presidential Alert that pops up on your phone was actually sent from somebody with a Software Defined Radio?
According to research recently released by a team from the University of Colorado Boulder, it’s not as far-fetched a scenario as you might think. In fact, given what they found about how the Commercial Mobile Alert Service (CMAS) works, there might not be a whole lot we can even do to prevent it. The system was designed to push out these messages in the most expedient and reliable way possible, which meant that niceties like authentication had to take a backseat.
 The thirteen page report, which was presented at MobiSys 2019 in Seoul, details their findings on CMAS as well as their successful efforts to send spoofed Presidential Alerts to phones of various makes and models. The team used a BladeRF 2.0 and USRP B210 to perform their mock attacks, and even a commercially available LTE femtocell with modified software. Everything was performed within a Faraday cage to prevent fake messages from reaching the outside world.
The thirteen page report, which was presented at MobiSys 2019 in Seoul, details their findings on CMAS as well as their successful efforts to send spoofed Presidential Alerts to phones of various makes and models. The team used a BladeRF 2.0 and USRP B210 to perform their mock attacks, and even a commercially available LTE femtocell with modified software. Everything was performed within a Faraday cage to prevent fake messages from reaching the outside world.
So how does the attack work? To make a long story short, the team found that phones will accept CMAS messages even if they are not currently authenticated with a cell tower. So the first phase of the attack is to spoof a cell tower that provides a stronger signal than the real ones in the area; not very difficult in an enclosed space. When the phone sees the stronger “tower” it will attempt, but ultimately fail, to authenticate with it. After a few retries, it will give up and switch to a valid tower.
This negotiation takes around 45 seconds to complete, which gives the attacker a window of opportunity to send the fake alerts. The team says one CMAS message can be sent every 160 milliseconds, so there’s plenty of time to flood the victim’s phone with hundreds of unblockable phony messages.
The attack is possible because the system was intentionally designed to maximize the likelihood that users would receive the message. Rather than risk users missing a Presidential Alert because their phones were negotiating between different towers at the time, the decision was made to just push them through regardless. The paper concludes that one of the best ways to mitigate this attack would be to implement some kind of digital signature check in the phone’s operating system before the message gets displayed to the user. The phone might not be able to refuse the message itself, but it can at least ascertain it’s authentic before showing it to the user.
All of the team’s findings have been passed on to the appropriate Government agencies and manufacturers, but it will likely be some time before we find out what (if any) changes come from this research. Considering the cost of equipment that can spoof cell networks has dropped like a rock over the last few years, we’re hoping all the players can agree on a software fix before we start drowning in Presidential Spam.















Cheap SDR and deepfakes are going to define the 2020s.
It’s a Brave New World!
It’s been pretty cool watching the price of SDR plummet over 10 years.
Yeah it has! How rapidly things have changed, and are still changing.
I’m just itching for the right chips to show up so that we can stick a cheap FPGA on a board with a cheap wide-band IQ transceiver and give it a featherwing footprint or something.
The hobbyist world is about to crash head-on with with the RF world and I mean in all of the good ways.
In 5 years we’ll probably look back on these comments and reminisce at how it used to be only a dream, and yet, here we are now. Hello future self.
I’m curious, can you detail a bit more what would be the benefit for hobbyist?
I’ve nether done any SDR, I just see it as a way to hack RF signal, but that’s it.
Do you mean that hobbyist will have easier access to RF? Like what esp8266 did?
Just curious to know what excite you! :D
In a way, yes, as it enables users to use a wide array of frequencies and protocols without having the ‘equipment’ specific for specific tasks. Simply put, its like a sonic screw driver, but for RF.
Personal computers made it possible for anyone to write their very own code and run it on a real computer, a feat that used to be not available to everyone.
So far there has not been equivalent access to the world of RF.
To “write code” for RF has until lately consisted of building physical hardware circuits, just as early computers were programmed by building physical logic gates. That is cumbersome! It is also not accessible to everyone.
Software Defined Radio makes RF accessible to everyone, as the hardware RF circuits are now replaced by lines of code.
You can now write your very own RF code to interface directly with the EM field. What will people do with that? Nobody knows! This territory is as uncharted today as computer software was some 40 years ago.
The PC didn’t really make coding available to everyone. A lot more people, sure. But you still need to invest significant time and not everyone has the required aptitude.
The same goes for RF. Even with SDR it’s still pretty complicated stuff.
But what it does make possible is for advances to be more easily copied. Just download a new program, much simpler than spending hours soldering and measuring.
I’m not sure I share the same level of enthusiasm you exhibit here and below.
How far have you gotten into DSP? It requires much discipline. It’s not exactly a world of ‘hacks’. The hardware will be there, yes, but the results?… For transmission you quickly run against a legal quagmire.
Also, Free Radio had a real movement during the early-mid ’90’s, but it petered out when people saw the web as an alternative. Many would be surprised to know that NPR had its crew in DC to put the kibosh on it along with the rest of the major players. God forbid they lose one of their two or three stations per major US city.
Well as for the legal quagmire, that’s something I’m particularly excited about too.
It turns out that the legal hurdle is the last one remaining as the others have all come down. That’s an unstable situation that can’t persist for very long.
Soon hopefully the FCC will have to recognize the need for reform, as they’re currently posing a massive and undesirable hindrance to progress.
I think this hindrance comes mostly from the fact that making an RF design used to be so much more costly and the FCC testing was only a portion of the overall cost, whereas now RF has become so accessible that there are countless designs (existing or imagined) where the FCC testing accounts for literally 99.9% of the cost. That is…. a problem.
There’s plenty of room to get the cost of testing down without sacrificing anything. They just haven’t been motivated to do it.
Although, the reason I think SDR will leave such a mark on the next decade is less excitement about what you and I can do with it but more a reaction of “the world isn’t ready for the possibilities”.
So far there is a ton of stuff happening in the EM field which is currently “secure” through obscurity. This article gives a textbook example.
There are just so many examples, from somewhat big things like this article down to countless small things like maybe the local makerspace is as easy to get in to as sending an unencrypted UDP packet containing the word “operate” on the right 802.15.4 channel to open the front door.
SDR isn’t what makes it possible access these things. It’s what makes it possible for suddenly many orders of magnitude more people to access these things. The number of insecure RF implementations combined with the number of people gaining access to those implementations is, I think, a pretty significant combination.
Well grasshopper; the hobbyist world crashed head on with the RF world decades ago. Created the singularity that has expanded into consumer electronic world we have today.
The entire system was designed and is being used by people with little technical background and understanding.
When amber alerts are being sent out regularly as presidential alerts then not only is the technical side of the system broken but the procedural side is as well.
I tried to suggest that amber alerts should be sent out as actual amber alerts and i got labeled as a monster who doesnt care about the children, I got labeled the Anti-Christ when i suggested that you should be able to silence amber alerts on your phone before they even come in. Yet people dont understand how these are the things that cause these systems to fail and become useless.
Amber alerts dont require the level of notification that a presidential alert will. Waking up people in the middle of the night is not going to help with an amber alert. Amber alerts should always be displayed but should not make the phone vibrate or emit a noise unless chosen to by the owner. by making every amber alert the presidential alert, the people who are using the system are devaluing the system as eventually people will intentionally ignore presidential alert levels.
Amber alerts AREN’T sent with the same priority as Presidential Alerts…
There are multiple levels of priority, all of which can be disabled except for Presidential. Almost every phone allows you to disable them.
that is the point of my comment, yet here in ontario canada amber alerts are being sent out at the presidential alert level which is causing an overload of our 911 system as angry irate people being woken up in the middle of the night are calling the number provided in the alert. So the procedural side of the system is broken here but the article shows that the technical side of the system is broken as well given that they didnt seem to be concerned about spoofing issues.
I don’t recall seeing a single presidential alert ever on my phone here in the sensible interior of the USA. Amber alerts, yes. The two are not at all comparable.
I am not American, I am from Ontario Canada and so far this year we have had a minimum of 2 amber alerts that have used presidential alert notification level, hence the comparison. The system may be being used properly down there but it isnt up here which is frustrating because we tend to use all of the same communications infrastructure as you do.
Sounds like maybe you guys need a clearer chain of command for that alert level. Have you considered getting a president?
Are you from the usa?
One orange slightly used president free to a good home
Wasn’t the EAS spoofed like this a few years back?
Are you thinking of the accidental middle attack warning in Hawaii? That was operator error, not a spoof/hack/attack.
Missle, not middle, attack
PROTECT THE ENDS!
Presidential alert – what a buffoonery! There should be also the God Alert with even higher priority.
I would say if the people hired you to be a senator or Mayor of NYC, and instead, you spend 16 months campaigning for president while ignoring your daily duties to your constituents, the impostor might be you, so to speak. Get out of the way! It is Kamala’s time.
It’s August 1, 2019 and President Trump is in Dallas working his base. Trump is in the middle of a baffling and rambling tirade that started out about Hilary, touches on muller, but ended up being about the wall. All 20,000 people in the crowd are hanging off every word and cheering at every pointy hand gesture and ok sign.
Suddenly every cellphone in the arena vibrates and emits piercing noises. A hush descends on the crowd as they reach for their phones in confusion.
Presidential Alert
President Trump and his security team have been abducted and replaced by imposters. Citizens are asked to intervene. Apprehend and detain at all costs. May be armed and dangerous.
The message takes only seconds to process and the crowd becomes totally silent. The secret service agents, sensing something ominous, move towards the president. They can tell something is wrong, but they are on the secret service’s com system and have no idea what just happened.
The president, on the other hand, is totally oblivious to the change. He has now switched topics and is talking about Iran, no wait, NATO. A low murmur starts in the crowd and grows until a man shouts, “Get them.” And 20,000 people start to rush the stage.
The secret service agents initiate the evacuation plan, but no one had planned for the possibility of 20,000 people bum rushing the president from every angle. They manage to get him back stage, but even the presidents staffers and local police are convinced that the alert is legitimate.
Yeah, I don’t really know how to end this without getting in trouble.
Uh… most of the agents are drowned by the massive angry mob, but one agent manages to disguise the president in a bear suit he found in the green room. They make it out through the roof just as Marine One touches down. The marines initially think the bear is real because of the noises that the president is making from inside, but the agent somehow convinces them that this is the president. They all get on the helicopter and ride off into the sunset.
This story made my day. Have a cookie.
Thanks! I just hope I don’t wake up tomorrow to a couple of suits banging on my front door. My wife would kill me.
I just want to reinforce, how awesome that comment is. Thank you for the laugh.
What is the value of a spoofed message? Granted, an attacker could ‘spoof’ an ICBM attack [0], but the coverage area would be trivially small, maybe a block or two.
[0] https://beta.washingtonpost.com/news/the-switch/wp/2018/01/30/heres-what-went-wrong-with-that-hawaii-missile-alert-the-fcc-says/?outputType=amp
As a diversion for, say, a heist.
for teh lulz
Who says there has to be any value in it? If it’s somebody that just wants to cause trouble, a system that allows them to blast phones with hundreds of bullshit messages that say they’re from the President is pretty appealing.
Value? Tons of value, tons…
“Hello, is your refrigerator running?”
Find a memory bug it turns in to a RCE vector.. There probably are some.. Android 9.0 has a big attack surface for ring 0 too from container API which is the lowest-trust of everything running on the app-processor
“Presidential” is just part of the name. It has nothing to do with who sends them. They’re generally sent by FEMA. The president has no direct control over these messages.
the value of a spoofed message is exactly what the target stands to lose. An Attacker could use this to spoof any one of many things in what is the most obvious escalation of privilege attack. Its one thing if a random number texts you something but to receive an official alert message is a whole other thing. What could be done with such a message, empty a building or area, cause chaos in an area, get a specific person emotional and not thinking logical (think about receiving an amber alert for your own kid), cause confusion among the authorities, etc etc. There are lots of ways that this could be mis-used and even on the small scale of a block or two it could be potentially dangerous and/or lucrative.
I wonder if this even needs a full duplex radio like USRP B210 or if a recording of the downlink would be enough?
Osmo-fl2k shows that GSM phones will show the network name and info even with just a pre-prepared recording going over a transmit capable SDR is enough. Fl2k compatible dongles are only 7eur.
Execute order 66.
Applying security would mean that messages would be blocked by phone in case of failed check. That could mean people die.
I’ve read all the papers on LTE. There are like four types of transactions you can do without intercepting handshakes. With handshakes you gotta use pre-shared keys for MITM and intercept stream keys. I’m no expert and may be off on some of it, but I learned a lot while learning where IMSI, ICCID, MEID(CDMA), MSISDN”” are in the streams..
I plan on dedicating a lot of time to SDR and 4G in the near future. I know there are no crypto weaknesses done; researchers have to trigger certain handshakes to get some data and spoof some things but they still need social engineering for full compromises.. Using IMSI or MSISDN from a fake station to leverage buffer overflows or social engineering etc..
By the way I think this was discovered years ago and was in one of the papers presented at a con..