When used for cracking passwords, a modern high-end graphics card will absolutely chew through “classic” hashing algorithms like SHA-1 and SHA-2. When a single desktop machine can run through 50+ billion password combinations per second, even decent passwords can be guessed in a worryingly short amount of time. Luckily, advanced password hashing functions such as bcrypt are designed specifically to make these sort of brute-force attacks impractically slow.
Cracking bcrypt on desktop hardware might be out of the question, but the folks over at [Scattered Secrets] had a hunch that an array of FPGAs might be up to the task. While the clock speed on these programmable chips might seem low compared to a modern CPUs and GPUs, they don’t have all that burdensome overhead to contend with. This makes the dedicated circuitry in the FPGA many times more efficient at performing the same task. Using a decade-old FPGA board intended for mining cryptocurrency, the team was able to demonstrate a four-fold performance improvement over the latest generation of GPUs.
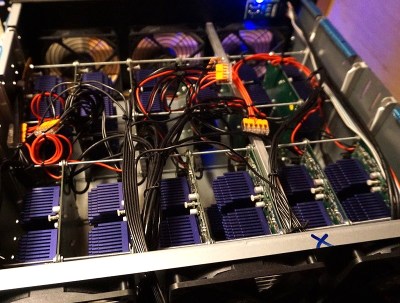
After seeing what a single quad FPGA board was capable of, the [Scattered Secrets] team started scaling the concept up. The first version of the hardware crammed a dozen of the ZTEX FPGA boards and a master control computer computer into a standard 4U server case. For the second version, they bumped that up to 18 boards for a total of 72 FPGAs, and made incremental improvements to the power and connectivity systems.
Each 4U FPGA cracker is capable of 2.1 million bcrypt hashes per second, while consuming just 585 watts. To put that into perspective, [Scattered Secrets] says you’d need at least 75 Nvidia RTX-2080Ti graphics cards to match that performance. Such an array would not only take up a whole server rack, but would burn through a staggering 25 kilowatts. Now might be a good time to change your password to something longer, or finally get onboard with 2FA.
We’ve covered attempts to reverse engineer hardware designed for cryptocurrency mining, but those were based around application-specific integrated circuits (ASICs) which by definition are very difficult to repurpose. On the other hand, disused FPGA-based miners offer tantalizing possibilities; once you wrap your mind around how they work, anyway.
[Thanks to Piejoe for the tip.]
















Two Factor Authentication is nice and all.
But it has downsides when every website wants its own app…
Would be nice to bake it into Email in a standardized way.
So that one can just give one’s email, then have the website/service send one a confirmation email that one uses a link in to log in.
It’s not like Email already is the single point of failure for accessing nearly everything one does on the internet. So adding this functionality wouldn’t make thing any worse. (And then one practically only has one password to remember, and that is to one’s Email, and that can then be a fairly long password. (Like CorrectHorseBatteryStaple is just a casual 25 character easy to remember password that absolutely no one should use.))
What website have you used that wants its own app? Even Google will let you use another app instead of their own Google Authenticator. Snapchat, Github, Google, Reddit, Discord, Twitter, npm, TeamViewer, Microsoft, Cloudflare, Gitlab, Instagram, and Amazon were all 100% okay with using Authy even though several of them have their own app.
It would be nice if it were handled by the Email service.
So that registration and login in is just an Email, the website then just sends a request to your Email service, and the email service then relays it to your app of choice.
The request never actually drops into your inbox as an Email.
So basically you want a central identity provider. There’s SSO/Oauth2 for that.
Steam wants you to use its own app. It makes it a royal PITA to get hold of the key (iirc involving a jailbroken ios/android device), as well as using a slightly different algorithm for some reason
Banks don’t do FIDO 2 or even FIDO U2F, or even TOTP. It’s as if they have been told by higher authorities that they are not allowed to do that. They sometimes use their own app or their own TOTP “dongle”. It’s interesting to note that the major banks were some of the first companies to sign up. Also, Apple is known to use their own app. When you lose your devices you are somewhat out of luck. At least with other methods, such as TOTP (and even U2F if you are diligent) you can have backups of the code in a safe place, which can then be used to recreate TOTP or reprogram a Yubikey. The latter is not widely known, but it can be done as far as I know.
This exists but hasn’t gained popularity. I have worked with Auth0 which is a service that developers can integrate with to add this feature to their site. https://auth0.com/passwordless There are probably other services that do the same thing.
That is why I use CorrectHorseStapleBattery
B^)
Personally, I’m fond of WrongDonkeyPaperclipGenerator.
Most people have fewer passwords than they do Standards… probably 14 or so…
There are really only 3 2fa apps out there if they don’t use one of them then they usually use text message. Also email would severely impacts the effectiveness of 2fa. The whole point is to have a single 2fa point ie your phone; you can log into email anywhere.
Secure implementations of 2fa require 2fa to reset passwords, meaning email is no longer a single point of failure. Your proposal additionally has the issue that it trains users to click on links in emails
That is indeed a downside. And why I said “Would be nice to bake it into Email in a standardized way.”
Ie, you don’t get it as an Email in itself
But rather, your Email service provider knows that messages of a certain type should go to their/your two factor authentication app instead.
This then means that one doesn’t need to hassle with setting this thing up more than once.
All a website registration suddenly needs is an email address, they send the authentication to the Email service, that then relays it to your app of choice, that you then answer and the thing works back on the chain to the website, letting them know that you are in fact who you state that you are.
Ie, registration and login is suddenly just an email address, and accepting it in an app of your choice. The website has no clue what 2FA app you use, they just need to know your email, the rest is handled from there.
Links in email is abhorrent as a solution, that I can agree with.
What you are proposing is not 2FA, it defeats its purpose.
The purpose is not to ask for a second confirmation, it is to use a second channel, independent of the first one.
No thanks.
Email login links are an awful user experience.
The app I work on currently uses them and I probably lose 30 minutes a week of productivity waiting for stupid emails to arrive, when I could just generate a 30 character password with 1Password instead.
xkcd’s 936 is still memorable and even secure after all these years, so even the FPGA might move on and look for a weaker target. Locks keep the honest people out — for a little while.
Unfortunately xkcd’s wasn’t doing as good as its webcomics https://thehackernews.com/2019/09/xkcd-forum-hacked.html…
This has been done for a while here: https://www.sciengines.com/technology-platform/sciengines-hardware/
Based on excellent work by the guys from John the Ripper https://www.openwall.com/john/, that wrote FOSS FPGA-based password cracking software!
Hmm, so if I find a digital wallet on a discarded USB and it has some unclear number of Bitcoins I might be able to find out how many ?
Or even go further and break the encryption and see where it is in the transaction history audit trail ?
Or even snatch it, is there a good forum web site that touches on this with any pertinent details ?
Can we get support for ECP5?
And then you still get the Corp folks who resist putting OWA behind MFA protection.
I guess these logins do not have lock out after three failed attempts? That would render most of this useless in less than a millisecond I would think and alert the user that some dbag is trying to unethically enter their account.
Most of the time, these brute force attacks are offline. They break into the computer (website or otherwise), grab the hashed passwords from a database or file and run the password cracker on the file for every user of the compromised computer. The first passwords to fall are the easiest to crack, only then will they try to access the live website. When they perform the brute force offline, there is no login protections like “three failed attempts”.
This is the reason security researchers have been harping on using unique passwords for every website/account. For instance, if someone cracked your username and password on “RandomForum.com” and it matched every other username and password including the one for your bank, the bad actors would be able to try that particular password anywhere that they find your username and gain access.
All of those sites you listed want you to use their app, an some like reddit are downright hostile to mobile website users.
Of course you can rent far larger/faster FPGA instances from Amazon for ~$1.50/hour ……