Readers of a certain age will no doubt remember the external modems that used to sit next to their computers, with the madly flashing LEDs and cacophony of familiar squeals announcing your impending connection to a realm of infinite possibilities. By comparison, connecting to the Internet these days is about as exciting as flicking on the kitchen light. Perhaps even less so.
But while we don’t use them to connect our devices to the Internet anymore, that doesn’t mean the analog modem is completely without its use. The OpenModem by [Mark Qvist] is an open hardware and software audio frequency-shift keying (AFSK) modem that recalls some of the charm (and connection speeds) of those early devices.
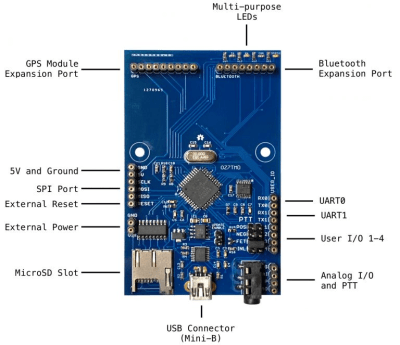 It’s intended primarily for packet radio communications, and as such is designed to tie into a radio’s Push-to-Talk functionality with a standard 3.5 mm jack connector. Support for AES-128 encryption means it will take a bit more than an RTL-SDR to eavesdrop on your communications. Though if you’re really worried about others listening in, the project page says you could even use the OpenModem over a wired connection as you would have in the old days.
It’s intended primarily for packet radio communications, and as such is designed to tie into a radio’s Push-to-Talk functionality with a standard 3.5 mm jack connector. Support for AES-128 encryption means it will take a bit more than an RTL-SDR to eavesdrop on your communications. Though if you’re really worried about others listening in, the project page says you could even use the OpenModem over a wired connection as you would have in the old days.
If you just want a simple and reliable way to get a secure AFSK communication link going, the OpenModem looks like it would be a great choice. But more than that, it offers a compelling platform for learning and experimentation. The hardware is compatible with the Arduino IDE, so you can even write your own firmware should you want to spin up your own take on this classic communications device.
The OpenModem is the evolution of the MicroModem that [Mark] developed years ago, and it’s clear that the project has come a long way since then. Of course, if you’re more about the look than the underlying technology, you could always just put a WiFi access point into the case of an old analog modem.
[Thanks to Boofdas for the tip.]
















Are radio hams in other countries allowed to use encryption on their ax.25 links?
I’m pretty certain it is still not allowed by the UK licence.
Definitely not allowed in the US
Irony is DMR is proprietary technology that is taking over UHF ham frequencies.
DMR is not proprietary. You can download the standard at ETSI. The voice codec may be proprietary, but it is not standardized, you can plug in another one. This is also a disadvantage, some radios don’t work together as they use a different speech codec. The data parts are completely standardized and interoperability seems to be good in my experience.
While you could theoretically write your own codec, no one else would have it (at first) and you’d have no one to talk to. This is the practical problem you run into with standards. Being ubiquitous beats technical merit most of the time.
There is an open source vocoder that can be use over the air, It s called Codec2 and it’s implementation is called M17 protocol.
There is even a project to inject open source firmware into some commercial/ham radio’s to implement the M17 vocoder right in the radio. It is called OpenRTX.
Some of the people in that project are even working into an open source/hardware radio that would natively be M17 compatible and also analog for back compatibility with the analog repeaters.
DMR it’s an ETSI standard. An yes reprogrammin Motorola HTs to be used in HAM band was a thing in the ’90 even if that wasn’t officially supported by Motorola. And if you don’t put keys in the codeplug the radio will transmit unecrypted signals.
Besides both the Icom D-Star and Yaesu C4FM digital modes are proprietary.
D-STAR is actually not proprietary, it was developed by the Japan Amateur Radio League. The spec is freely available, but it has the same problem as C4FM and DMR – the proprietary vocoder. I’ve heard people discuss implementing D-STAR with Speex (open source vocoder) but that would require a lot of buy-in.
I’ve heard of people encoding TCP/IP over amateur radio. In this day and age is this in practice illegal since most publicly available services over TCP/IP have strong encryption, or is it enough for the transport layer (the TCP/IP headers) to still be in the clear?
I see no issues with TCP/IP as long as TLS or SSH or other form of encryption is not used and that the trafic is non comercial. Encoding is not allowed unless is decodable by open public know software.
Definitely not permitted in normal circumstances.
From the UK Amateur Radio Licence:
“11.2.b Messages sent from the station shall not be encrypted for the purposes of rendering the Message unintelligible to other radio spectrum users.”
(There are exceptions for operating under direction of a national authority e.g. in emergencies).
As I understand it when the amateur radio service was set up it was only permitted as long as it did not compete with the monopolistic commercial services. To ensure this all communications must be ‘en clair’.
Additionally, in the UK we are not permitted to carry third-party messages other than ‘greetings messages’.
Not on HAM frequencies, but this modem is radio agnostic. If you have a licensed channel you can use it. Although I would then use DMR data modems, as a lot of equipment is available off-the-shelf.
It would be nice if they amended it to allow encryption with restrictions, for example encrypted transmissions must yield to unencrypted transmissions and are subject to much stricter duty cycle limitations.
An alternative for some uses would be cryptographic signing. It would work if you’re not concerned about others being able to read your messages but are concerned about others impersonating you. (As in you need authentication and message integrity, but not confidentiality.)
Signing is totally allowed for hams, though. The relevant clause doesn’t ban cryptography altogether, just using it for encryption. If I remember correctly the wording is along the lines of “nothing that would conceal the content of the message from someone listening”, i.e. any form of encryption, obfuscation and possibly steganography (good luck detecting that one, though) would be banned, while a signature is perfectly valid, as it doesn’t conceal anything, but verifies the content instead.
That’s my understanding of the law as well. But IANAL. I remember something similar to “Codes or cyphers intended to obscure the meaning of a message are prohibitted”. I couldn’t find that in part 97 the last time I checked though, perhaps the wording was changed.
I have long thought that things like repeater control codes or other remote control signals should be sent this way, encode the command along with a sequence number or timestamp with a private key. Broadcast the public key at least every 10 minutes alongside one’s callsign. You could even include a URL in that 10-minute ID leading to a page that explains the purpose encryption and how to decode it.
No one could say you were purposefully obscuring the meaning of your transmission.
But they would anyway. You would probably have 50 lurkers suddenly lose their mic fright so that they can tell you that encryption isn’t allowed plus here in the US a few that would try to call the FCC who may or may not actually care. I’m guessing it would go similarly in the rest of the world but I do not know.
I would like to see the ARRL adopt this scheme and ask their friends at the FCC to specifically write something like it into the law so that there is no question. I don’t expect this to happen so long as there aren’t a bunch of people out there trying to hijack repeaters or impersonate other hams though. I don’t think they will be interested unless there is a demonstrable need for change. We are kind of in the 1970s security though trusting one another phase that the internet started with and for now, so far so good.
Also, there are exceptions written in where commands sent to space stations and model aircraft may be coded to obscure their meaning. I think I have heard of the FCC making very liberal interpretations of what is a space station in order to allow people to encode terrestrial repeater control signals. I guess that’s better than nothing.
Rather than bending the space station rule I would rather see them add a rule to explicitly allow signed messages so long as the public key is also sent. That would be much more flexible in what it would allow hams to do while still achieving what I think the goals of the prohibition on encryption are, preventing the ham bands from being filled with commercial activity and preventing it from being a useful tool for illegal activity.
In Poland, encryption is allowed. More precisely, it is not prohibited. The encryption of international communications is prohibited by radio communications regulations by ITU
Open hardware or not, do we really need more softmodems in this world? There’s a reason they are in the dump with the S3 Virges and Tandy’s.
So drop also the SDR, which is a soft radio…
Some SDRs do the actual SDR bit in a FPGA or DSP. Besides, the modem in the article is no more of a soft modem than the serial port 56k modems. If you call that a soft modem, the only hardware modem would be the really ancient ones based around banks of analog filters.
Ironically the most simple and most popular Packet-Radio modem, the BayCom / PC-Com modem, also falls into this category. It’s purely hardware-based (no DSP) but requires the PC running the AX. 25 protocol. On DOS, this was implemented in the TFX/TFPC TSRs..
In the context of the pandemic, the natural disasters and the civil unrest all endangering the communication infrastructure could this openmodem be used with packet radio to allow people to keep texting to each other?
If a large number of people had an openmodem at home could it form a mesh network that could run signal or a similar texting app?
When we get to the point that normal communication no longer works, a ham radio isn’t going to save you from the inevitable chaos that will follow.
That has absolutely nothing to do with what I asked and it’s typical internet deflecting.
And we did get to the point when normal communication didn’t work several times in 2020. The cell network was simply overloaded a few times and a mesh network would have helped enormously.
This can absolutely work if you get the infrastructure up and running in time. For shorter distance/”everybody” kind of communication I’d go for something LORA-based though, ideally a small open hardware pocket sized device.
“cell network overload” is completely different than “endangering the communication infrastructure”
If cell network is overloaded, you can still use a wired/wifi connection to communicate.
A ham radio mesh network would have a tiny bandwidth compared to cell network, so it wouldn’t work as a backup anyway.
There are already harmonised radio and operating protocols for this, traditional AX.25 packet radio is not one of them for a reason, (inefficiency and unreliability). And the normal citizen that wants do do pointless apping and texting is also kept out for a reason.
And yes in a natural disaster emergeny situation ham radio is most of time the only thing that works.
Please elaborate “unreliability”, sir.
From what I remember, PR in 1200 Baud AFSK worked on Cb-Radio bands, even.
And if it works on these scrap bands, even,
then how on earth can it be unreliable then? 😉
Vy73, 55
I was kind of hoping this would be a DOCSIS or ADSL modem, but a fully open source TNC is pretty cool, too.
Super cool, but would love to see a through-hole version I can just get boards made for and solder together myself after a look at that price tag for an AVR thing. Obviously a ton of work, but it would take a bit more of a benefit at that price point to beat the 30 year old serial TNC I have that does the job (mostly) fine.
Wow!
With encryption being legal on MURS and LMR, this cute little black box just made secure wireless data that much easier over distances exceeding that which Part 15 devices can offer.
Then there are the wireline applications…
Most important however, is that this is an open source project. That means people can learn things from this, and tweak their own improvements.
I am unsure if I understand the purpose of this device, what are the advantages of a hardware TNC compared to a software solution using the audio output of one’s computer?
Lower power probably, so you can stick this and a microcontroller in solar powered hut on a hill.
Hm, I thought this was mainly designed as a peripheral, so you would have to have some kind of computer anyway?
I think part of the emphasis of the OP is on security, with the AES keys stored on the modem itself, and not easily accessible by the computer. All firmware available for audit, etc.
Computers get compromised, hard-drives crash, and all sorts of bad stuff happens. Operating systems prevent interoperability.
A little standalone box like this is pretty much bombproof. Distribute a couple to your communication partners, and then you’re done.
A TNC (any type) usually does hold the connection on its own, no matter what.
Even in KISS mode, it will do the translation ASCII-Audio/Audio-ASCII.
Which means, if the PC “hangs” for a moment, the connection won’t interrupt.
Also, some TNC have a mailbox, were you can leave a message. A TNC also allows
for digipeating. So you can use a friend Ham station to connect to stations you won’t reach directly..
1) Adjusting the levels can be tricky sometimes with soundcard based softmodems.
2) You still have your computer soundcard free to play other sounds
It is popular to solve #2 by using a second USB based sound device. This is can be done DIY with a cheap USB sound dongle or commercially with products like Rigblaster which have a USB sound device built in.
It’s still easy, especially by people that are more into radios than computers to mess up the separate USB sound solution and accidentally route the wrong audio into it. There’s always one in every group that ends up broadcasting Windows alerts!
Just wondering if anyone has tried to use something like this underwater to control say a sub? You might have to adjust the freq but it seems like it could be an interesting idea. Of course I am talking about in a pool or pond not a really big body of water.
For under water communication, you need very low frequency/low speed links. I would recommand you to read on the vlf band where all the nation that have subs have there communication links toward there ships. it is below 100 kHz.
I know this is old but experienced first hand the disaster that is created when an entire exchange goes down.
The SW eastern seaboard in victoria Australia went down. No atms no eftpos no mobile at least if you were with telstra no money no business.So shops had to close for weeks until telstra remedied the situation.I was lucky with my fixed wireless as the isp had it’s own backbone infrastructure that also provided a network for a major railway in western australia so i believe.This also kept the WAN up for a local milk factory to remain in communication with it’s other factories.
I remember almost getting stuck in a town with bugger all fuel an hour in halfs drive away seeing the interstate trucks from south australia trying to refuel at the apco because they could’nt pay via eftpos. So the old washboard came out. I don’t think the young person serving was from a time when they used one so struggled. Anyway managed to get back to a main town on fumes and pulled into a Shell servo with fingers crossed hoping i could pay with my card as I had no cash. And what do you know i was able to top up. I asked the person serving how come I can pay for petrol with eftpos at this station and not anywhere else. And her answer was. “Shell learnt years ago never to trust telstra and so the SHELL servos throughout Australia have a private network”.