Remembering passwords is one of those things which one just cannot seem to escape. At the very least, we all need to remember a single password: namely the one for unlocking a password manager. These password managers come in a wide variety of forms and shapes, from software programs to little devices which one carries with them. The Mooltipass Mini BLE falls into the latter category: it is small enough to comfortably fit in a hand or pocket, yet capable of remembering all of your passwords.
Heading into its crowdfunding campaign, the Mooltipass Mini BLE is an evolution of the Mooltipass Mini device, which acts as a USB keyboard by default, entering log-in credentials for you. With the required browser extension installed, this process can also be automated when browsing to a known website. Any new credentials can also be saved automatically this way.
Where the Mooltipass Mini BLE differs from the original is in that it also adds a Bluetooth (BLE) mode, enabling it to be used easily with any BLE-capable device, including laptops and smartphones, without having to dig around for a USB cable and/or OTG adapter.
I have already been using the original Mooltipass Mini for a while, and the Mooltipass team was kind enough to send me a prototype Mooltipass Mini BLE for evaluation and comparison. Let’s take a look.
Hardware Password Manager Basics
Sometimes it feels as if the need to remember five dozen passwords is a recent thing, but it’s been pretty much a requirement ever since someone came up with the concept of ‘user accounts’ on computer systems. However, dealing with the passwords for one’s computer OS, two dozen online stores, banking and social media accounts does take a bit more wrangling. Especially if one does it the Right Way® and uses a different password for each login.
While passwords scribbled on a Post-It note are guaranteed secure so long as nobody sneaks a peek at them, this method is awkward and a bit of paper is easily lost. Software-based password managers are a definite step up, and is what I have been mostly using the past years. They use a master key to encrypt a database which contains the credentials as well as other sensitive information. One can safely carry this encrypted database file around by putting it on an online drive or USB stick.

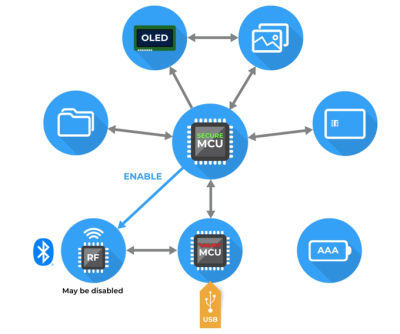
A hardware password manager like the Mooltipass Mini (BLE) is similar to that concept, only instead of an encrypted database file, the Mooltipass device is essentially the database in physical form. The credentials are stored locally, within a tamper-proof storage device. To unlock the device, you needs two things:
- Something you have (smartcard with AES key).
- Something you know (PIN code).
This two-factor authentication ensures that if someone runs off with your smartcard, they still cannot unlock your Mooltipass device. Also interesting with this approach is that multiple people can share the same Mooltipass device, only seeing the credentials which their personal smartcard and PIN code unlock. This is very different from another recent hardware password manager called the BeamU, which unlocks with only a finger print (‘something you are’), theoretically allowing anyone who lifts your finger print to gain access to all the credentials on your BeamU card.
That said, the Mooltipass Mini BLE still allows you to use it as a Web Authentication (FIDO2) device, with the lack of biometrics a wise choice, as I covered in a recent article on FIDO2. This is the same hardware token functionality we find in the SoloKey, but combines password keeping and FIDO2 in a single device. So far the Mooltipass Mini BLE is looking good.
Enter Low-Energy Dentistry
Bluetooth Low Energy (BLE) has become a favorite parallel protocol next to the regular Bluetooth protocol. It enables a similar communication range to regular Bluetooth, while using significantly less power. This is a good thing for the Mooltipass Mini BLE, as unlike its predecessor it now has to live off a battery. By default BLE is disabled, but can be enabled in the settings of the device.
With BLE enabled, a single battery charge should last approximately a month, depending on how often the screen is turned on. As this happens every time one has to confirm adding new credentials or manually sends credentials to a log-in field.
 The USB port has moved from Micro-USB to USB-C, but otherwise the USB-based functionality remains unchanged. In the Mooltipass Mini BLE the cable serves as both USB-based communication and charging the internal battery.
The USB port has moved from Micro-USB to USB-C, but otherwise the USB-based functionality remains unchanged. In the Mooltipass Mini BLE the cable serves as both USB-based communication and charging the internal battery.
With the accompanying software installed (known as moolticute with sources available on GutHub), one can tweak various settings for the device such as the keyboard layout to use for when it is emulating a USB or BLE keyboard. Accessing the list of credentials is also done through the application, allowing for the manual adding and maintaining of credentials. With those in order, one then merely has to install either a browser extension, or connect the Mooltipass Mini BLE via USB or BLE (or both) and pick the credentials to send to the connected device. If both BLE and USB are currently connected, the device will use its display to ask the user to choose between the two connections.
When trying this on a Windows 10 laptop via BLE, it managed to successfully fill in the log-in fields at sites like Github using the ‘simulated BLE keyboard’ functionality. No special software required, which makes it very useful for occasions when using a software-based password manager isn’t going to fly, like using a public or work computer.
My Beta Experience
After having been sent an early version of the Mooltipass Mini BLE device, I was informed that a second device was also on its way to me, on account of the first having a presumed firmware bug. Although I did not encounter this bug, it turned out that having a second device was very useful, due to the nature of Beta-level hardware. At some point, the display of the first device stopped turning on, despite the rest of the unit still working. This was confirmed as a known issue with early units.

The second device has not given me any major issues so far. I was able to use it in a similar way to the Mooltipass Mini, before exploring the new features. In terms of feel and looks, both devices are quite similar. They’re still encased in a similar metal shell, the clicky scroll wheel on the right-hand side is very similar and the display is the familiar monochrome look, albeit a more high-resolution OLED screen than on the original.
When I received the first device, I could pop in one of the provided smartcards and creating a fresh key (‘user’). Also useful is the ability to clone a smartcard via a menu option. This way you have a backup of the key in case you somehow lose the original smartcard. In the Moolticute application you are also constantly reminded to make a backup of the credential database. This all should make it pretty hard to ever get locked out of one’s accounts as the database is never confined to a single device.
Seeing the login fields on various sites while on my laptop get filled in almost as if by magic was also an interesting experience. The only issues which I encountered had to do with the Mini BLE’s USB interface currently not dealing well with my usual USB hub, and the BLE HID on my Xiaomi Mi 5 smartphone did not work. USB hubs are no problem on the original Mini, so that appears to be a temporary glitch, with the Mooltipass team already aware of the issue.
Early Verdict
The Mooltipass Mini BLE seems to be pretty much the hardware password manager that I hadn’t really realized I needed. I’m not really into Web Authentication, nor do I trust biometrics for securing my data. That’s where the Mooltipass Mini BLE offers non-biometric two-factor authentication to unlock it, even allowing for different categories of encrypted data (unlocked with different smartcard and PIN). Having FIDO2 support is a bonus in case I ever want to use it and need a token.
 Like the original Mini, the Mini BLE is an open source project, for both the hardware and software. Whether this is an important point to you or not is mostly a personal choice. For me, it does add a certain level of confidence in the sense that I can look at the schematics and source code whenever I feel like it.
Like the original Mini, the Mini BLE is an open source project, for both the hardware and software. Whether this is an important point to you or not is mostly a personal choice. For me, it does add a certain level of confidence in the sense that I can look at the schematics and source code whenever I feel like it.
Since I got early prototype hardware to use, it seems unfair to put too much weight on some remaining hardware and firmware issues. I do however hope that these last issues get resolved before the final hardware is ready. Once that happens I might be tempted to retire the Mooltipass Mini for its BLE successor.





















Embedded advertisement: The article forgets to mention this item is sold by tindie, which like hackaday belongs to supplyframe.
The Mooltipass is sold by Stephen Electronics on Tindie. You are correct that Supplyframe owns both Tindie and Hackaday.
You’re indeed right!
However, the mini has been out of stock for 6 months and the mini BLE won’t hit Tindie before a couple of months as well :)
Already signed up for two.
thanks a lot for your support… developing that device was one of the hardest things we have ever done. We now have a lot of respect for routers given the complexity of a dual MCU architecture….
I really do need a PW manager. I frequently find myself having to reset my passwords, which really means my e-mail account is the key to the kingdom. There’s no good way around that unless I use a bunch of different addresses, which requires one to not only remember yet more passwords, but also which addresses are associated with which website accounts.
I’m not against hardware devices, as long as the database can be duplicated, which this mooltipass can do. Though if given the choice, I’d like to use my phone (not necessarily as 2FA), perhaps via BT/USB in some way, and appropriate PC software. Furthermore I’d like duplicate databases with a copy being on my phone, and other copies being on PCs with the software installed. I’m not inherently against cloud storage, but really only for backups, and I wouldn’t want to pay a monthly fee (but maybe one-time fees in events such as DB recovery). That, and it would have to be provided by a company you don’t expect to go bankrupt any time soon (Amazon, Google, MS, etc). Surely this exists, RIGHT?
Bitwarden is open source and can be self hosted if desired (on your choice of the above providers). It allows you to export the DB so you can have multiple copies. Being open source means you can’t ever lose access to your database because they go bust, which is a big win for me. They do provide a hosting option which is much easier to set up.
There are both PC applications, “apps” and browser extensions, so you can use it as you find most helpful, though it doesn’t have a way of filling in PC applications from your phone, you have to read the password from your phone and type it in to the PC.
Database exports aren’t encrypted which is a little annoying as it leaves it up to the user to secure their passwords if they choose to export, but there are many ways to do this.
It’s not perfect, but it seems to meet the majority of your desires so may be worth a look
Interesting. It seems like their free option seems to have a lot of the features I want, including the option for self-hosting. I need to look into it some more, but so far I like what I see. Thanks for the suggestion!
If you have the time to put on id always thought deterministic password generation (in the vein of bip32) would be excellent if it could be made to work. Maybe domains are hashed? Or usernames ? Somewhat to derive a path
I’m very happy with EncryptPad. It is an openPGP backended text editor, on github, yada yada yada….
It allows me to edit my passwords in a free style way, add notes, keep a history. Like in an editor. Because it is an editor.
I’ve got a relatively simple setup. When I need to login to somewhere, I just reach into my pocket and flip over a coin, this is detected by central control of my earth station network and the nearest transmitter uplinks to my cubesat and passes my 4 digit pin code, with a voice library hacked from a Russian GPS-satnav so everyone thinks it’s a meaningless numbers station. Now a lot of people say that quantum entangling two coins is unpossible, that’s because they tried it with quarters, are you batshit crazy? Quarters are far too massive, you need to use dimes. However, you can’t be too careful, either about the quantum signal or the 4 digit pin code, soooo 2 factor baby, so my cubesat, running freeBSD, fires up it’s webcam and looks for a yellow umbrella near my last recorded location. Now this is slightly embarrassing, it was supposed to work with a regular sized umbrella, but I misunderestimated the resolution of the cam or something and I need to carry around a 10ft patio umbrella for it to work. Then it charges up the supercapacitor, which takes 5 minutes, then using a railroad surplus contactor, this discharges into a CO2 gas laser in pulse mode, blipping out my password as an IrDA HUD device signal (Gotta make sure the dongle is plugged in when the device doesn’t have IrDA) which types it directly into the website for me. There’s a few niggles with the system in cloudy weather, but otherwise seems to work well.
;-)
I call bullshit. Any secure implementation would use OpenBSD and not FreeBSD!
You don’t want to use your phone for 2 reasons. #1 what do you use to manage the passwords while you are browsing the web on your phone. #2 your phone is it’s own always connected general purpose computer, quite capable of being compromised and sending your password DB off on it’s merry way all on it’s own. The Mooltipass has a BLE and a USB connection and that’s it and it does Mooltipass things with Mooltipass (signed) firmware, much safer.
As Mike has said, there’s Bitwarden.
Personally my needs are more complex so I use KeePass. It’s a bit more complicated to sync the database but not impossible. I use it on my smartphone, tablet and laptop. All sync to my own cloud.
I find it more powerful than Bitwarden but I did examine Bitwarden at one point for use with family shared secrets.
StashPass is an offline password manager. You store your user names and passwords on a hardware device so its not connected to any servers, etc. Its pretty slick and there’s no subscription. You should check it out if you’re still looking for something.
Shame they kept the clicking wheel. It’s just too fragile a point of failure.
You have to dump IPA into it every few months to keep it responsive. That IPA is reportedly weakens the plastic.
It’s a beautiful device that’s for sure.
I do wish it took a wider spectrum or at least easier to source smart cards though 2-4 is probably more than anyone will ever need. (Two accounts with a backup card each).
We’ve actually switch scroll wheels for a better one!
As a funny anecdote my daughter and I have thrown the device on the floor multiple times without any damage to the Mini BLE. Given that it was a weak point for the mini, it is something we spent extra effort on :).
Am I missing something here? Something I have (smartphone) and something I know (password). I’m already carrying that and it’s got a touchscreen, battery and BTLE.
Mooltipass app?
if you trust your phone and all the apps running on it :)
I assume it still lacks a sync capability, which renders it useless in a family or work environment?
Real shame as it’s otherwise a nice bit of kit.
But if I can’t have two users simultaneously adding passwords to it, it’s not going to be hugely useful. Before you object, you may not do that often, but for passwords, we can’t have any risk of one user overwriting the other’s change, and you can’t rely on one user exporting a backup and another user having to import it before they continue.
The OG mooltipass lets you export to file making sure it keeps that file up to date. That file can be on a synchronised folder.
I don’t know about using two mooltipasses, but using the same mooltipass on multiple computers seems to work fine.
I don’t think I’ve deleted many passwords which I imagine is the largest concern for database synchronisation.
The issue with a database is that they’re usually a single file, or an opaque format. Thus any update to the database will require the whole thing to be updated.
The ability to export doesn’t mean it can sync. An export is just a backup.
Hello Dan!
As Alex correctly mentioned, there’s an option to constantly monitor a given export file.
It seems that what you’d like is, the moment a given user makes a change to its database, to automatically update the backup file and on the other computer automatically import it. If so, it’s fairly easy to implement.
Oh, wow, awesome!
Thanks for replying!
I still have the original Mooltipass and I love it. I must admit there were a few things that were a bit annoying but it was still a first gen device so I can’t be too critical. I love the idea of having a wireless Mooltipass Mini. With a lot of micro USB cables being power only it can be frustrating to find one that actually passes data as well when fetching one from a draw. Wireless solves this. I know it might add a bit of complexity to it but if the new Mooltipass Mini had wireless charging, that would be awesome.
I guess I’m out of touch. I have a Mooltipass and I find it a nice addition to the “wish I hadn’t spent the money” pile. I dug it out to try it again, and I’m sorry but the software ecosystem to support this device is dismal and their site is mostly advertising fluff and little technical detail. The article above likewise skips the whole “how you manage your password database” part of the problem.
For example, going to the multicute github, you can go to “releases” but hey, they’re source releases. At this point, having an APT repository that I can point my ubuntu distro at to pull binaries (and all dependencies) or, far more importantly, Windows and MacOS binaries are kinda required for anything claiming to be this close to “production”.
I use a password manager on various platforms already, and it’s closed-source, and I hate being locked in. But I’ll likely go towards another solution rather than the Mooltipass unless/until the ecosystem “grows up”. I know, I could “contribute”, but the barrier to even use the device is so high that I’m demotivated and would rather contribute to the many many other projects out there.
Lastly, scroll wheel is cute and all, but it’s just kinda clunky and slow to unlock the device and interact with menus. A couple buttons would be just as fast for input.
I concur, i bought the mini some years ago and the usability is just not there. It’s been in a drawer for over a year now…
Hello Chris!
Thanks for the time you took to write your feedback.
To address your points:
– lack of technical details: the short answer is that it doesn’t interest most people :/. We’re geek ourselves so also a bit sad to not be able to explain as much as we’d like the mooltipass ecosystem internals…
– github release: the releases on the first page are beta releases, with the executables pushed on betas.themooltipass.com. If you go to the second page, you’ll find stable release with installers
– barrier: perhaps you could try out our mini BLE emulator? https://mooltipass.github.io/minible/developing_using_emulator . It takess less than 5 minutes to be operational
– scroll wheel: we completely disagree with you on that one, especially when scrolling through credentials
I wonder;
– Is the communication with BT secure enough?
– The keyboard mode can be captured with a key logger?
Keyboard can probably be captured, but at least it’s not got your master password.
FIDO or 2FA are the only things to protect you against a keylogger.
If BLE is sniffed, that’s arguably a different threat model to what this is aiming to deal with.
Same for 5$. Now hacker please improve it : https://hackaday.io/project/171819-passstronger
Interesting, but the need of an extra smartcard completely kills this for me. I want a dongle I can use to authenticate anywhere, not a dongle AND SOME SMARTCARD. Incidentally, I’m also not happy about how standard dongles tended to store your keys OUTSIDE themselves, with a mere feeble local cypher guarding your security (but which of course granted you “unlimited” credential storage – unsurprising on account of how your key for any specific site WASN’T STORED ON YOUR ACTUAL FUCKING DONGLE).
Any plans on FIDO2 BLE functionality? Current BLE FIDO2 tokens being proprietary seems such a waste.
it’s on the todo list :)